Category: Viral
‘Enterprise clients usually have some level of company-wide program as far as sustainability goes. Toner recycling programs have been offered to all of our clients for many years. We continue to do so. If they wish to take advantage of it, it’s quite simple for us to start up with them. All of our vendors…
Read MoreHPE will sell 30 percent of its stake in China-based H3C for $2.1 billion, with the option of selling its remaining 19 percent share, HPE said in a regulatory filing today. Hewlett Packard Enterprise will sell 30 percent of its shares of H3C to Chinese IT provider Unisplendour for approximately $2.1 billion, HPE said in…
Read MoreThe main contributor was Nvidia’s data center revenue, which more than quintupled in the first quarter from the same period last year, growing 427 percent year-over-year to $22.5 billion. Nvidia once again reported triple-digit growth in revenue and profit in the latest quarter from the same period last year, a sign that demand for the…
Read MoreMay 24, 2024The Hacker NewsCybersecurity Webinar Don’t be fooled into thinking that cyber threats are only a problem for large organizations. The truth is that cybercriminals are increasingly targeting smaller businesses, and they’re getting smarter every day. Join our FREE webinar “Navigating the SMB Threat Landscape: Key Insights from Huntress’ Threat Report,” in which Jamie…
Read MoreMay 24, 2024NewsroomVulnerability / Browser Security Google on Thursday rolled out fixes to address a high-severity security flaw in its Chrome browser that it said has been exploited in the wild. Assigned the CVE identifier CVE-2024-5274, the vulnerability relates to a type confusion bug in the V8 JavaScript and WebAssembly engine. It was reported by…
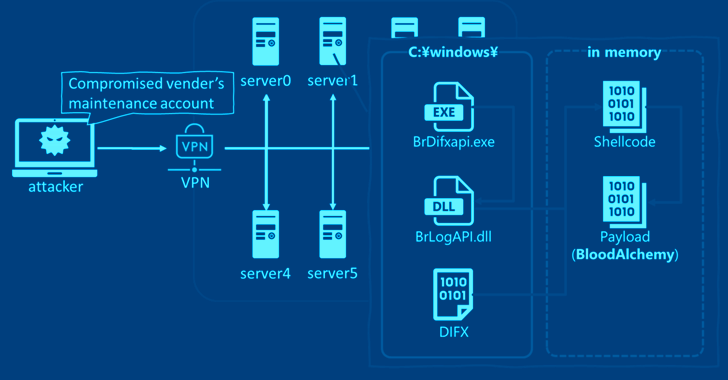
Read MoreMay 24, 2024NewsroomAPT Malware / Cyber Espionage Cybersecurity researchers have discovered that the malware known as BLOODALCHEMY used in attacks targeting government organizations in Southern and Southeastern Asia is in fact an updated version of Deed RAT, which is believed to be a successor to ShadowPad. “The origin of BLOODALCHEMY and Deed RAT is ShadowPad…
Read MoreESET Research Available as both an IDA plugin and a Python script, Nimfilt helps to reverse engineer binaries compiled with the Nim programming language compiler by demangling package and function names, and applying structs to strings 23 May 2024 • , 5 min. read The Nim programming language has become increasingly attractive to malware developers…
Read More‘Security is a team sport,’ Microsoft CVP Vasu Jakkal said on a panel this week. Microsoft solution providers are “critical” to the vendor’s plans for achieving and maintaining responsible artificial intelligence and security, Microsoft executives told CRN this week. During a panel on responsible AI and security held the week of Microsoft Build 2024, CRN…
Read MoreMay 23, 2024NewsroomThreat Intelligence / Vulnerability, The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a security flaw impacting Apache Flink, the open-source, unified stream-processing and batch-processing framework, to the Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. Tracked as CVE-2020-17519, the issue relates to a case of improper access control…
Read More“So once the acquisition closes, our partners will have the opportunity to join Palo Alto Networks’ partner program, if they’re not already part of that, so they will be able to then sell Palo Alto’s Cortex XSIAM,” IBM’s Channel Chief Kate Woolley tells CRN. IBM and Palo Alto Networks are working together to make sure…
Read MoreRecent Posts
- Safeguarding Healthcare Organizations from IoMT Risks
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks