Category: Viral
A zero-day vulnerability in CrushFTP was exploited in the wild against multiple U.S. entities prior to fixed versions becoming available as the vendor recommends customers upgrade as soon as possible. Background On April 19, CrushFTP published an advisory for a zero-day vulnerability in its file transfer tool which bears the same name. CVE Description CVSSv3…
Read More“The statement that came back to me from Broadcom was, ‘We appreciate that with these changes VMware is not for everybody,’” says Tom Smyth, head of technical solutions as Misco, a U.K.-based solution provider. “Everyone else can use it. Broadcom is not going to gear its decisions towards them anymore. … I can appreciate that.…
Read MoreApr 23, 2024NewsroomSupply Chain Attack / Application Security Researchers have identified a dependency confusion vulnerability impacting an archived Apache project called Cordova App Harness. Dependency confusion attacks take place owing to the fact that package managers check the public repositories before private registries, thus allowing a threat actor to publish a malicious package with the…
Read MoreUnitedHealth Confirms Data Theft From Change Healthcare, ‘Substantial’ Number Of Americans Possibly Impacted
by nlqip
The data stolen from prescription processor Change Healthcare includes ‘files containing protected health information (PHI) or personally identifiable information (PII),’ UnitedHealth says. UnitedHealth Group said in a statement Monday it’s confirming that a potentially significant amount of data belonging to Americans may have been stolen in the Change Healthcare cyberattack earlier this year. The stolen…
Read More“These access points have a role in not only networking for AI, but also AI for networking,” said HPE Aruba’s VP of product and community marketing Larry Lunetta, in reference to HPE Aruba’s acquisition target Juniper Networks’ CEO Rami Rahim’s own take that the industry is just scratching the surface with AI networking. HPE Aruba…
Read More‘This isn’t a feature that will allow partners to steal other customers,’ Microsoft program manager Brent Serbus said on a call Wednesday. A Microsoft partner program manager says the tech giant’s upcoming partner-to-partner new commerce experience license transfer policy for the Cloud Solution Provider program is not designed to encourage solution providers to poach customers…
Read MorePart 3 of CRN’s 2024 Big Data 100 includes a look at the vendors solution providers should know in the big data system and cloud platform space. All Systems Go Today’s “big data stack” includes databases, data management software and data analytics tools – all critical components of an effective operational or analytical data system.…
Read MoreThe new M-Trends report details how ransomware, zero-day attacks and other major cyber threats evolved last year. The discovery of compromised systems continues to accelerate thanks both to improved detection tools and increased ransomware activity, according to Mandiant’s M-Trends threat report for 2024 that was released Tuesday. The analysis is the 15th annual M-Trends report…
Read MoreApr 23, 2024NewsroomEnd-to-End Encryption / Privacy European Police Chiefs said that the complementary partnership between law enforcement agencies and the technology industry is at risk due to end-to-end encryption (E2EE). They called on the industry and governments to take urgent action to ensure public safety across social media platforms. “Privacy measures currently being rolled out,…
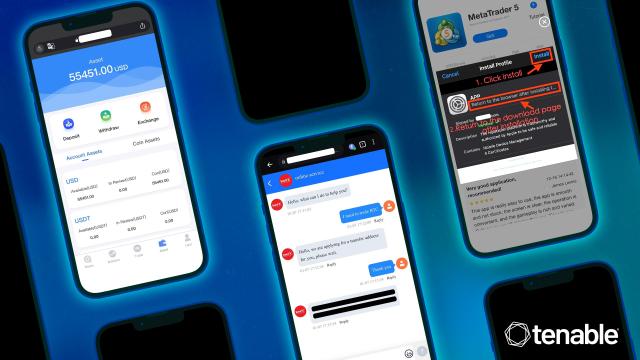
Read MorePig Butchering Scam: How Bitcoin, Ethereum, Litecoin and Spot Gold (XAUUSD) Investments Are Used in Romance Scams to Steal Hundreds of Millions
by nlqip
This is the second part of a two-part series based on firsthand research into pig butchering scams from the end of 2022 into early 2024. In this post, we delve into the types of investment scams perpetrated by pig butchers to steal hundreds of millions of dollars from victims, including in the form of cryptocurrency…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA