Category: Viral
Video Almost 400 people in India and Pakistan have fallen victim to an ongoing Android espionage campaign called eXotic Visit 12 Apr 2024 Could your messaging app of choice have been authored by a threat actor known as Virtual Invaders? As described by ESET researchers this week, this is what happened to the victims of…
Read MoreScams Here’s how cybercriminals target cryptocurrencies and how you can keep your bitcoin or other crypto safe 15 Apr 2024 • , 6 min. read Bitcoin is on a tear. The world’s largest digital currency by market cap passed its previous record value of nearly $69,000 in early March. It’s now worth an estimated $1.3…
Read MoreKids Online From promoting questionable content to posing security risks, inappropriate ads present multiple dangers for children. Here’s how to help them stay safe. 16 Apr 2024 • , 5 min. read In today’s digital world, ads are practically unavoidable. From pop-up ads on your daily Wordle to sneaky affiliate posts on your favorite social…
Read MoreScams What are some of the most common giveaway signs that the person behind the screen or on the other end of the line isn’t who they claim to be? 18 Apr 2024 • , 5 min. read Our world is becoming more impersonal as it becomes more digital-centric. And because we can’t see the…
Read MoreWhat are the risks and consequences of having your health data exposed and what are the steps to take if it happens to you? Source link wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3…
Read MoreApr 20, 2024NewsroomVulnerability / Endpoint Security Users of the CrushFTP enterprise file transfer software are being urged to update to the latest version following the discovery of a security flaw that has come under targeted exploitation in the wild. “CrushFTP v11 versions below 11.1 have a vulnerability where users can escape their VFS and download…
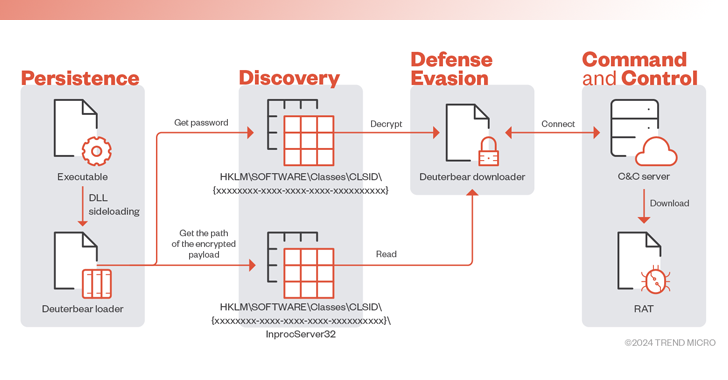
Read MoreApr 19, 2024NewsroomNetwork Security / Firmware Security Technology, research, and government sectors in the Asia-Pacific region have been targeted by a threat actor called BlackTech as part of a recent cyber attack wave. The intrusions pave the way for an updated version of modular backdoor dubbed Waterbear as well as its enhanced successor referred to…
Read MoreAttackers are increasingly making use of “networkless” attack techniques targeting cloud apps and identities. Here’s how attackers can (and are) compromising organizations – without ever needing to touch the endpoint or conventional networked systems and services. Before getting into the details of the attack techniques being used, let’s discuss why these attacks are becoming more…
Read MoreThreat Actors Exploit Multiple Vulnerabilities in Ivanti Connect Secure and Policy Secure Gateways | CISA
by nlqip
SUMMARY The Cybersecurity and Infrastructure Security Agency (CISA) and the following partners (hereafter referred to as the authoring organizations) are releasing this joint Cybersecurity Advisory to warn that cyber threat actors are exploiting previously identified vulnerabilities in Ivanti Connect Secure and Ivanti Policy Secure gateways. CISA and authoring organizations appreciate the cooperation of Volexity, Ivanti,…
Read MoreAs many as 37 individuals have been arrested as part of an international crackdown on a cybercrime service called LabHost that has been used by criminal actors to steal personal credentials from victims around the world. Described as one of the largest Phishing-as-a-Service (PhaaS) providers, LabHost offered phishing pages targeting banks, high-profile organizations, and other…
Read MoreRecent Posts
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips