Category: Viral
Mar 13, 2024The Hacker NewsApp Security / Cyber Security One of the most common misconceptions in file upload cybersecurity is that certain tools are “enough” on their own—this is simply not the case. In our latest whitepaper OPSWAT CEO and Founder, Benny Czarny, takes a comprehensive look at what it takes to prevent malware threats…
Read MoreMar 13, 2024NewsroomLarge Language Model / AI Security Google’s Gemini large language model (LLM) is susceptible to security threats that could cause it to divulge system prompts, generate harmful content, and carry out indirect injection attacks. The findings come from HiddenLayer, which said the issues impact consumers using Gemini Advanced with Google Workspace as well…
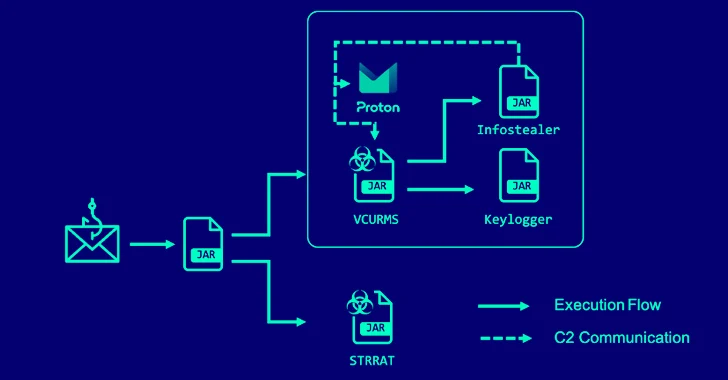
Read MoreMar 13, 2024NewsroomPhishing Attack / Threat Intelligence A new phishing campaign has been observed delivering remote access trojans (RAT) such as VCURMS and STRRAT by means of a malicious Java-based downloader. “The attackers stored malware on public services like Amazon Web Services (AWS) and GitHub, employing a commercial protector to avoid detection of the malware,”…
Read MoreCritical Infrastructure What cyberthreats could wreak havoc on elections this year and how worried should we as voters be about the integrity of our voting systems? 12 Mar 2024 • , 4 min. read This year, billions of people will go to the polls to decide their next political leaders. From India to the US,…
Read MoreMar 12, 2024The Hacker NewsCryptocurrency / Cybercrime Threat hunters have discovered a set of seven packages on the Python Package Index (PyPI) repository that are designed to steal BIP39 mnemonic phrases used for recovering private keys of a cryptocurrency wallet. The software supply chain attack campaign has been codenamed BIPClip by ReversingLabs. The packages were…
Read MoreEmbracing the Cloud: Revolutionizing Privileged Access Management with One Identity PAM Essentials
by nlqip
Mar 11, 2024The Hacker NewsPrivileged Access Management As cyber threats loom around every corner and privileged accounts become prime targets, the significance of implementing a robust Privileged Access Management (PAM) solution can’t be overstated. With organizations increasingly migrating to cloud environments, the PAM Solution Market is experiencing a transformative shift toward cloud-based offerings. One Identity…
Read MoreMar 11, 2024The Hacker NewsCybersecurity / Browser Security As the shift of IT infrastructure to cloud-based solutions celebrates its 10-year anniversary, it becomes clear that traditional on-premises approaches to data security are becoming obsolete. Rather than protecting the endpoint, DLP solutions need to refocus their efforts to where corporate data resides – in the browser.…
Read MoreMar 11, 2024NewsroomZero-Day / Endpoint Security A financially motivated threat actor called Magnet Goblin is swiftly adopting one-day security vulnerabilities into its arsenal in order to opportunistically breach edge devices and public-facing services and deploy malware on compromised hosts. “Threat actor group Magnet Goblin’s hallmark is its ability to swiftly leverage newly disclosed vulnerabilities, particularly…
Read MoreVideo Evasive Panda has been spotted targeting Tibetans in several countries and territories with payloads that included a previously undocumented backdoor ESET has named Nightdoor 08 Mar 2024 This week, ESET researchers released their analysis of how an Advanced Persistent Threat (APT) group targeted Tibetans via watering hole and supply-chain attacks. The cyberespionage campaign –…
Read MoreESET researchers discovered a cyberespionage campaign that, since at least September 2023, has been victimizing Tibetans through a targeted watering hole (also known as a strategic web compromise), and a supply-chain compromise to deliver trojanized installers of Tibetan language translation software. The attackers aimed to deploy malicious downloaders for Windows and macOS to compromise website…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA