Category: Viral
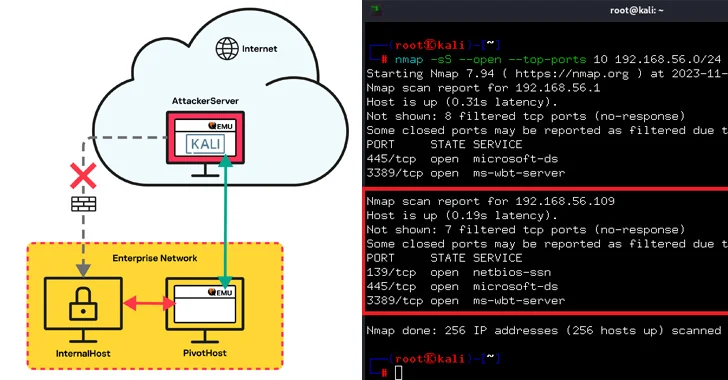
Mar 08, 2024NewsroomEndpoint Security / Network Security Threat actors have been observed leveraging the QEMU open-source hardware emulator as tunneling software during a cyber attack targeting an unnamed “large company” to connect to their infrastructure. While a number of legitimate tunneling tools like Chisel, FRP, ligolo, ngrok, and Plink have been used by adversaries to…
Read MoreMar 08, 2024NewsroomVulnerability / Threat Intelligence The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical security flaw impacting JetBrains TeamCity On-Premises software to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The vulnerability, tracked as CVE-2024-27198 (CVSS score: 9.8), refers to an authentication bypass bug that allows…
Read MoreScams The internet can be a wonderful place. But it’s also awash with fraudsters targeting people who are susceptible to fraud. 06 Mar 2024 • , 5 min. read We’re all getting older. That’s good news for digital fraudsters, who see rich pickings to be had in a rapidly ageing society. They’re increasingly targeting senior…
Read MoreMar 07, 2024NewsroomCyber Espionage / Software Security The China-linked threat actor known as Evasive Panda orchestrated both watering hole and supply chain attacks targeting Tibetan users at least since September 2023. The end of the attacks is to deliver malicious downloaders for Windows and macOS that deploy a known backdoor called MgBot and a previously…
Read MoreIn today’s rapidly evolving SaaS environment, the focus is on human users. This is one of the most compromised areas in SaaS security management and requires strict governance of user roles and permissions, monitoring of privileged users, their level of activity (dormant, active, hyperactive), their type (internal/ external), whether they are joiners, movers, or leavers,…
Read MoreThe U.S. Department of Justice (DoJ) announced the indictment of a 38-year-old Chinese national and a California resident of allegedly stealing proprietary information from Google while covertly working for two China-based tech companies. Linwei Ding (aka Leon Ding), a former Google engineer who was arrested on March 6, 2024, “transferred sensitive Google trade secrets and…
Read MoreAdvisory ID: VMSA-2024-0007 CVSSv3 Range: 4.3 Issue Date: 2024-03-07 Updated On: 2024-03-07 (Initial Advisory) CVE(s): CVE-2024-22256 Synopsis: VMware Cloud Director updates address a partial information disclosure vulnerability (CVE-2024-22256). Source link ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde…
Read MoreHow often do you go somewhere without your phone? And how do you feel when you go somewhere with no signal? Let’s be honest, the majority of us would admit that going without our beloved devices close at hand causes a lot of stress. And the stats show it: studies show that nomophobia, the fear…
Read MoreMar 06, 2024NewsroomServer Security / Cryptocurrency Threat actors are targeting misconfigured and vulnerable servers running Apache Hadoop YARN, Docker, Atlassian Confluence, and Redis services as part of an emerging malware campaign designed to deliver a cryptocurrency miner and spawn a reverse shell for persistent remote access. “The attackers leverage these tools to issue exploit code,…
Read MoreAn in-depth look into a proactive website security solution that continuously detects, prioritizes, and validates web threats, helping to mitigate security, privacy, and compliance risks. [Reflectiz shields websites from client-side attacks, supply chain risks, data breaches, privacy violations, and compliance issues] You Can’t Protect What You Can’t See Today’s websites are connected to dozens of…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA