Category: Viral
Social Media Do you often take to social media to broadcast details from your life? Here’s why this habit may put your privacy and security at risk. 26 Feb 2024 • , 5 min. read Hundreds of millions of us log on to our favorite social media sites every day. We shop, share photos and…
Read MoreAdvisory ID: VMSA-2024-0005 CVSSv3 Range: 5.9 Issue Date: 2024-02-27 Updated On: 2024-02-27 (Initial Advisory) CVE(s): CVE-2024-22251 Synopsis: VMware Workstation and Fusion updates address an out-of-bounds read vulnerability (CVE-2024-22251) Source link ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde…
Read MoreFeb 27, 2024The Hacker NewsMalware / Network Security An “intricately designed” remote access trojan (RAT) called Xeno RAT has been made available on GitHub, making it available to other actors at no extra cost. Written in C# and compatible with Windows 10 and Windows 11 operating systems, the open-source RAT comes with a “comprehensive set…
Read MoreFeb 27, 2024NewsroomSupply Chain Attack / Data Security Cybersecurity researchers have found that it’s possible to compromise the Hugging Face Safetensors conversion service to ultimately hijack the models submitted by users and result in supply chain attacks. “It’s possible to send malicious pull requests with attacker-controlled data from the Hugging Face service to any repository…
Read MoreProcessing alerts quickly and efficiently is the cornerstone of a Security Operations Center (SOC) professional’s role. Threat intelligence platforms can significantly enhance their ability to do so. Let’s find out what these platforms are and how they can empower analysts. The Challenge: Alert Overload The modern SOC faces a relentless barrage of security alerts generated…
Read MoreFeb 27, 2024NewsroomWebsite Security / Cryptojacking A critical security flaw has been disclosed in a popular WordPress plugin called Ultimate Member that has more than 200,000 active installations. The vulnerability, tracked as CVE-2024-1071, carries a CVSS score of 9.8 out of a maximum of 10. Security researcher Christiaan Swiers has been credited with discovering and…
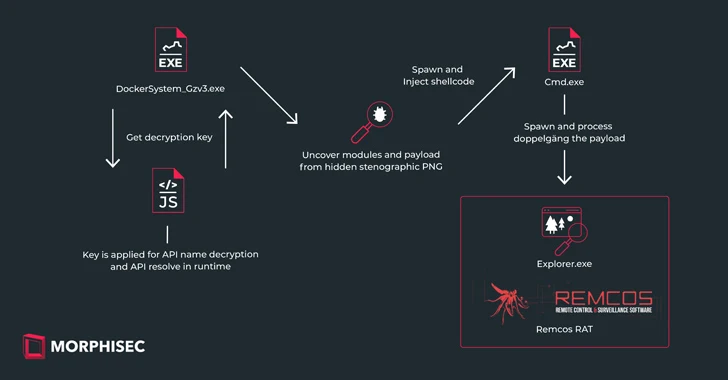
Read MoreFeb 26, 2024The Hacker NewsSteganography / Malware Ukrainian entities based in Finland have been targeted as part of a malicious campaign distributing a commercial remote access trojan known as Remcos RAT using a malware loader called IDAT Loader. The attack has been attributed to a threat actor tracked by the Computer Emergency Response Team of…
Read MoreHow SVR-Attributed Actors are Adapting to the Move of Government and Corporations to Cloud Infrastructure OVERVIEW This advisory details recent tactics, techniques, and procedures (TTPs) of the group commonly known as APT29, also known as Midnight Blizzard, the Dukes, or Cozy Bear. The UK National Cyber Security Centre (NCSC) and international partners assess that APT29…
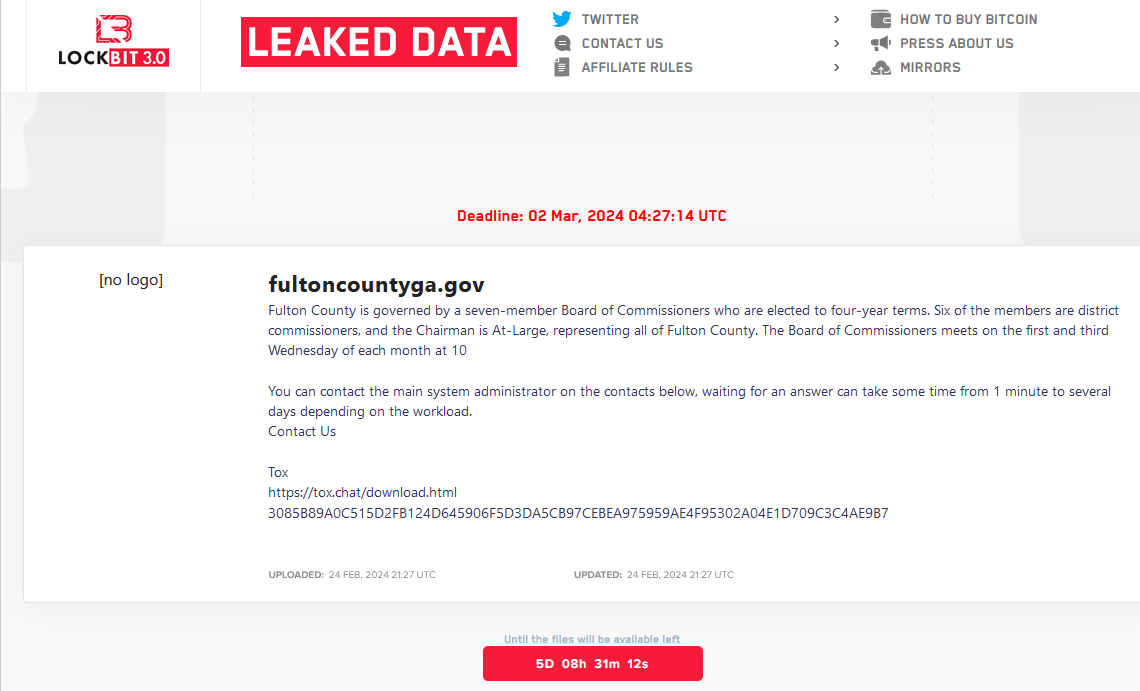
Read MoreFBI’s Lockbit Takedown Postponed a Ticking Time Bomb in Fulton County, Ga. – Krebs on Security
by nlqip
The FBI’s takedown of the LockBit ransomware group last week came as LockBit was preparing to release sensitive data stolen from government computer systems in Fulton County, Ga. But LockBit is now regrouping, and the gang says it will publish the stolen Fulton County data on March 2 unless paid a ransom. LockBit claims the…
Read MoreFeb 24, 2024NewsroomActive Directory / Data Protection Microsoft has expanded free logging capabilities to all U.S. federal agencies using Microsoft Purview Audit irrespective of the license tier, more than six months after a China-linked cyber espionage campaign targeting two dozen organizations came to light. “Microsoft will automatically enable the logs in customer accounts and increase…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA