Category: Viral
Twenty five years after the launch of CVE, the Tenable Security Response Team has handpicked 25 vulnerabilities that stand out for their significance. Background In January 1999, David E. Mann and Steven M. Christey published the paper “Towards a Common Enumeration of Vulnerabilities” describing an effort to create interoperability between multiple vulnerability databases. To achieve…
Read MoreIn an interview with CRN, the Mandiant founder discusses joining the board at Expel and why he believes GenAI is ‘going to help the defender more.’ When it comes to generative AI, cybersecurity luminary Kevin Mandia believes the technology will end up as a bigger asset to cyber defense teams than hackers—even though the benefits…
Read MoreVerizon CEO Hans Vestberg mentioned the pending $20 billion megadeal to acquire Frontier Communications and its recently acquired spectrum from U.S Cellular as part of its plan for fixed wireless, 5G and private networking domination during the company’s third-quarter 2024 earnings and broadband update call Tuesday. Verizon is relying on its strong “foundation” of a…
Read MoreOct 22, 2024Ravie LakshmananDocker Security / Cloud Security Bad actors have been observed targeting Docker remote API servers to deploy the SRBMiner crypto miner on compromised instances, according to new findings from Trend Micro. “In this attack, the threat actor used the gRPC protocol over h2c to evade security solutions and execute their crypto mining…
Read More‘The DACH region, with its high GDP and untapped potential, is the next logical step. We’ve been successful in North America by delivering a high-touch, relationship-driven approach and we believe that will resonate in Germany as well,’ says Climb CEO Dale Foster. Climb Channel Solutions has pushed further into the European market with a focused…
Read MoreOct 22, 2024Ravie LakshmananVulnerability / Software Security Details have emerged about a now-patched security flaw in Styra’s Open Policy Agent (OPA) that, if successfully exploited, could have led to leakage of New Technology LAN Manager (NTLM) hashes. “The vulnerability could have allowed an attacker to leak the NTLM credentials of the OPA server’s local user…
Read MoreOct 22, 2024Ravie LakshmananIdentity Management / Security Automation Service accounts are vital in any enterprise, running automated processes like managing applications or scripts. However, without proper monitoring, they can pose a significant security risk due to their elevated privileges. This guide will walk you through how to locate and secure these accounts within Active Directory…
Read MoreOct 22, 2024Ravie LakshmananVulnerability / Supply Chain Cybersecurity researchers have discovered a number of suspicious packages published to the npm registry that are designed to harvest Ethereum private keys and gain remote access to the machine via the secure shell (SSH) protocol. The packages attempt to “gain SSH access to the victim’s machine by writing…
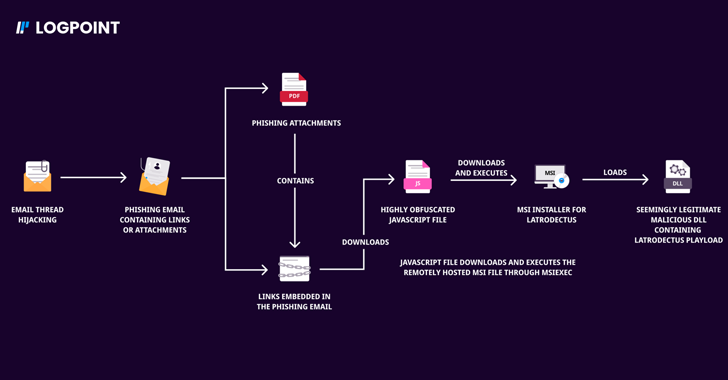
Read MoreOct 22, 2024Ravie LakshmananMalware / Threat Intelligence Two malware families that suffered setbacks in the aftermath of a coordinated law enforcement operation called Endgame have resurfaced as part of new phishing campaigns. Bumblebee and Latrodectus, which are both malware loaders, are designed to steal personal data, along with downloading and executing additional payloads onto compromised…
Read MoreOct 22, 2024Ravie LakshmananVulnerability / Enterprise Security VMware has released software updates to address an already patched security flaw in vCenter Server that could pave the way for remote code execution. The vulnerability, tracked as CVE-2024-38812 (CVSS score: 9.8), concerns a case of heap-overflow vulnerability in the implementation of the DCE/RPC protocol. “A malicious actor…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA