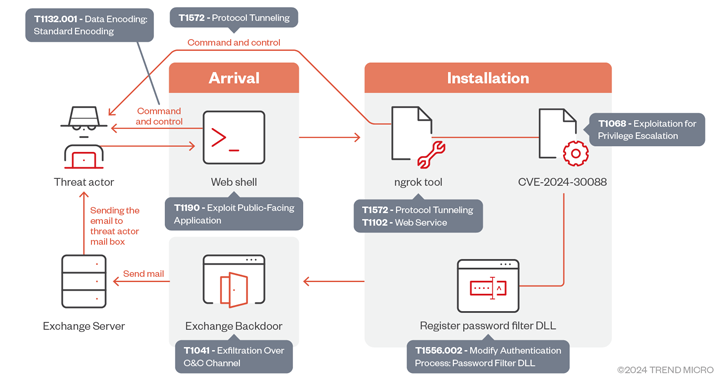
Category: Viral
Cybersecurity researchers have found that entry points could be abused across multiple programming ecosystems like PyPI, npm, Ruby Gems, NuGet, Dart Pub, and Rust Crates to stage software supply chain attacks. “Attackers can leverage these entry points to execute malicious code when specific commands are run, posing a widespread risk in the open-source landscape,” Checkmarx…
Read MoreOct 14, 2024The Hacker NewsCloud Security / Vulnerability The link between detection and response (DR) practices and cloud security has historically been weak. As global organizations increasingly adopt cloud environments, security strategies have largely focused on “shift-left” practices—securing code, ensuring proper cloud posture, and fixing misconfigurations. However, this approach has led to an over-reliance on…
Read MoreOct 14, 2024Ravie LakshmananNetwork Security / Vulnerability A suspected nation-state adversary has been observed weaponizing three security flaws in Ivanti Cloud Service Appliance (CSA) a zero-day to perform a series of malicious actions. That’s according to findings from Fortinet FortiGuard Labs, which said the vulnerabilities were abused to gain unauthenticated access to the CSA, enumerate…
Read MoreOct 14, 2024Ravie LakshmananRansomware / Vulnerability Threat actors are actively attempting to exploit a now-patched security flaw in Veeam Backup & Replication to deploy Akira and Fog ransomware. Cybersecurity vendor Sophos said it has been tracking a series of attacks in the past month leveraging compromised VPN credentials and CVE-2024-40711 to create a local account…
Read MoreOct 13, 2024Ravie Lakshmanan The Iranian threat actor known as OilRig has been observed exploiting a now-patched privilege escalation flaw impacting the Windows Kernel as part of a cyber espionage campaign targeting the U.A.E. and the broader Gulf region. “The group utilizes sophisticated tactics that include deploying a backdoor that leverages Microsoft Exchange servers for…
Read MoreVideo ESET research dives deep into a series of attacks that leveraged bespoke toolsets to compromise air-gapped systems belonging to governmental and diplomatic entities 11 Oct 2024 This week, ESET researchers published the results of their probe into a series of attacks that leveraged bespoke toolsets to compromise air-gapped systems belonging to governmental and diplomatic…
Read MoreOct 12, 2024Ravie LakshmananCryptocurrency / Cybercrime The U.S. Department of Justice (DoJ) has announced arrests and charges against several individuals and entities in connection with allegedly manipulating digital asset markets as part of a widespread fraud operation. The law enforcement action – codenamed Operation Token Mirrors – is the result of the U.S. Federal Bureau…
Read More“Seamlessly integrated into your experience, the AI assistant continues your conversation as you navigate through Partner Center,” according to Microsoft. Microsoft is previewing an artificial intelligence-powered assistant in its Partner Center with capabilities ranging from support ticket creation to quick answers. The Partner Center AI assistant – notably not called a “copilot,” Microsoft’s typical name…
Read MoreIn addition to launching a new Copilot AI engine to assist with data analytic workflows, dbt Labs is expanding the capabilities of its popular dbt Cloud platform with cross-platform data mesh capabilities, support for the Apache Iceberg data table format, and new low-code visual editing tools. Dbt Labs is expanding its dbt Cloud data management…
Read MoreA new tax-themed malware campaign targeting insurance and finance sectors has been observed leveraging GitHub links in phishing email messages as a way to bypass security measures and deliver Remcos RAT, indicating that the method is gaining traction among threat actors. “In this campaign, legitimate repositories such as the open-source tax filing software, UsTaxes, HMRC,…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA