Category: Viral
Ingram Micro’s Trust X Alliance is the starting point for helping solution providers take their sustainability efforts to new heights. Ingram Micro is ramping up its commitment to sustainability, leveraging its long-standing Trust X Alliance solution provider group in its aim to drive meaningful change across the industry, the community at large and the planet.…
Read MoreNov 06, 2024Ravie LakshmananSaaS Security / Threat Detection An ongoing threat campaign dubbed VEILDrive has been observed taking advantage of legitimate services from Microsoft, including Teams, SharePoint, Quick Assist, and OneDrive, as part of its modus operandi. “Leveraging Microsoft SaaS services — including Teams, SharePoint, Quick Assist, and OneDrive — the attacker exploited the trusted…
Read MoreFrom AI governance platforms and polyfunctional robots to energy-efficient and spatial computing, here are the top 10 technology trends and use cases for 2025, according to Gartner’s new report. IT research firm Gartner predicts the 10 biggest technology trends of 2025, which includes the rise of agentic AI technology, demand for disinformation cybersecurity solutions and…
Read More‘We are asking Nvidia every day [about Blackwell availability]. So I hope their production can go smoothly and go for high volume very soon. And once they have achieved availability, our solutions are fully ready,’ says Supermicro President and CEO Charles Liang. Supermicro is ready to continue the rapid growth in the AI business as…
Read More‘I think a lot of MSPs have been told that their PSA’s project management tool is all they need, but the reality is these tools often don’t cut it. Many MSPs, especially the larger ones, need something much more tailored and capable of handling the complexity of their workflows,’ said Mike Psenka, CEO of Moovila,…
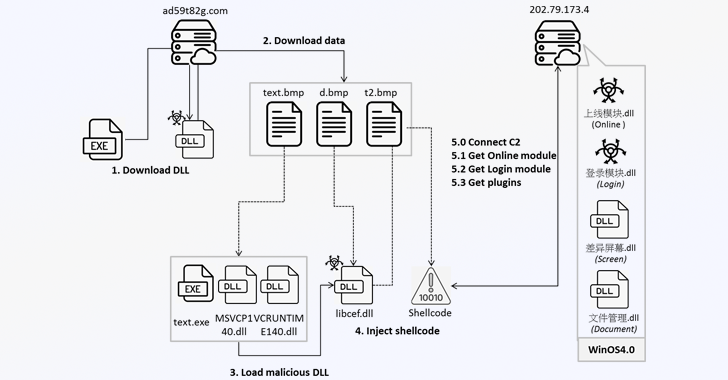
Read MoreNov 06, 2024Ravie LakshmananMalware / Online Security Cybersecurity researchers are warning that a command-and-control (C&C) framework called Winos is being distributed within gaming-related applications like installation tools, speed boosters, and optimization utilities. “Winos 4.0 is an advanced malicious framework that offers comprehensive functionality, a stable architecture, and efficient control over numerous online endpoints to execute…
Read More‘Our acquisition of Adaptive Shield takes us another step forward in giving our customers the best possible protection against modern cyberattacks with the Falcon platform,’ said CrowdStrike President Michael Sentonas. Cybersecurity all-star CrowdStrike is significantly boosting its Falcon platform with the acquisition of SaaS security startup Adaptive Shield. CrowdStrike President Michael Sentonas said the purchase…
Read More‘We are not here to find revenue growth in legacy telco. All of our transformation work is in service to customers who need and want to leverage technology like Gen AI to transform their business. The legacy networks of yesterday just won’t serve tomorrow’s enterprise … the customer experience in legacy telco is neither quick…
Read MoreBudget season is upon us, and everyone in your organization is vying for their slice of the pie. Every year, every department has a pet project that they present as absolutely essential to profitability, business continuity, and quite possibly the future of humanity itself. And no doubt that some of these actually may be mission…
Read MoreNov 06, 2024Ravie LakshmananCyber Threat / Cybercrime INTERPOL on Tuesday said it took down more than 22,000 malicious servers linked to various cyber threats as part of a global operation. Dubbed Operation Synergia II, the coordinated effort ran from April 1 to August 31, 2024, targeting phishing, ransomware, and information stealer infrastructure. “Of the approximately…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA