Category: Viral
‘We’ve taken some important steps to secure your snapshots and then put you in complete control,’ Microsoft Consumer CMO Yusuf Mehdi says. Microsoft has a new security architecture for its controversial Recall feature powering improved search on artificial intelligence PCs, set to become available for Windows Insider Program members in October. In a video announcing…
Read MoreSep 27, 2024Ravie LakshmananSoftware Security / Vulnerability Progress Software has released another round of updates to address six security flaws in WhatsUp Gold, including two critical vulnerabilities. The issues, the company said, have been resolved in version 24.0.1 released on September 20, 2024. The company has yet to release any details about what the flaws…
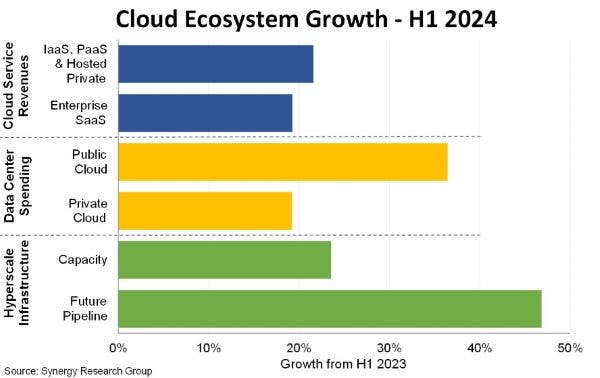
Read More‘Over the last 10 years ODMs have continued to eat up server market share, and now we see Nvidia’s explosive growth, which is largely fueled by sales to hyperscalers—either directly or indirectly,’ said John Dinsdale, Synergy Research Group’s chief analyst. Cloud revenues reached $427 billion in the first half of 2024, up 23 percent year…
Read MoreCleaning Up A Cybersecurity Mess: Blue Mantis Details The ‘Aftermath’ Of A Ransomware Attack
by nlqip
The Russian hacker group BlackCat got the password from the dark web and proceeded to breach the company’s core Microsoft Active Directory environment, said Blue Mantis Chief Operating Officer Jay Pasteris. The nightmare ransomware attack on a privately held national call center provider for some of the largest companies in the world started with a…
Read MoreBlue Mantis COO Jay Pasteris says he is determined to help customers turn back the increasingly sophisticated global cybersecurity threats. Source link lol
Read MoreCyberespionage the Gamaredon way: Analysis of toolset used to spy on Ukraine in 2022 and 2023
by nlqip
ESET Research ESET Research has conducted a comprehensive technical analysis of Gamaredon’s toolset used to conduct its cyberespionage activities focused in Ukraine 26 Sep 2024 • , 5 min. read The war in Ukraine, which started in February 2014 and intensified with Russia’s invasion of the country on February 24th, 2022, exemplifies a multifaceted war,…
Read MoreThe developer of the high-performance database looks to balance new capabilities like AI vector search while also meeting the mission-critical demands of customers migrating off legacy database systems. Cockroach Labs has debuted a new release of its high-performance distributed database with next-generation AI capabilities and a new service tier for its CockroachDB Cloud offering. The…
Read MoreSep 27, 2024Ravie LakshmananLinux / Vulnerability A new set of security vulnerabilities has been disclosed in the OpenPrinting Common Unix Printing System (CUPS) on Linux systems that could permit remote command execution under certain conditions. “A remote unauthenticated attacker can silently replace existing printers’ (or install new ones) IPP urls with a malicious one, resulting…
Read MoreThe threat actor known as Storm-0501 has targeted government, manufacturing, transportation, and law enforcement sectors in the U.S. to stage ransomware attacks. The multi-stage attack campaign is designed to compromise hybrid cloud environments and perform lateral movement from on-premises to cloud environment, ultimately resulting in data exfiltration, credential theft, tampering, persistent backdoor access, and ransomware…
Read MoreAs security technology and threat awareness among organizations improves so do the adversaries who are adopting and relying on new techniques to maximize speed and impact while evading detection. Ransomware and malware continue to be the method of choice by big game hunting (BGH) cyber criminals, and the increased use of hands-on or “interactive intrusion”…
Read More