Category: Viral
Data center veteran Jim Buie – whose resume includes stops at Flexential and AT&T – was named CEO of Tonaquint ,which has 140,000 square feet of data center space under management in facilities across the U.S. Data center veteran Jim Buie – whose resume includes stops at Flexential and AT&T – was named CEO of…
Read MoreCRN showcases the hottest 100 edge computing companies, including the top 25 cybersecurity companies, 25 IoT and 5G vendors, and 50 hardware, software and services edge companies. Companies at the forefront of the global edge computing market range from cloud giants and cybersecurity superstars to hybrid work specialists and AI startups. With market research firm…
Read MoreCRN’s list of the 50 hottest hardware, software and services companies in edge computing this year ranges from innovative startups like Reskube to edge specialists such as Scale Computing to market leaders like Cisco Systems, Dell Technologies and Microsoft. Today’s innovative software and hardware companies continue to invest in edge computing technologies in 2024 as…
Read MoreNov 04, 2024Ravie LakshmananVulnerability / Cyber Threat Cybersecurity researchers have disclosed six security flaws in the Ollama artificial intelligence (AI) framework that could be exploited by a malicious actor to perform various actions, including denial-of-service, model poisoning, and model theft. “Collectively, the vulnerabilities could allow an attacker to carry out a wide-range of malicious actions…
Read MoreNov 04, 2024The Hacker NewsWeekly Recap / Cybersecurity This week was a total digital dumpster fire! Hackers were like, “Let’s cause some chaos!” and went after everything from our browsers to those fancy cameras that zoom and spin. (You know, the ones they use in spy movies? 🕵️♀️) We’re talking password-stealing bots, sneaky extensions that…
Read MoreNov 04, 2024Mohit KumarDDoS Attack / Cybercrime German law enforcement authorities have announced the disruption of a criminal service called dstat[.]cc that made it possible for other threat actors to easily mount distributed denial-of-service (DDoS) attacks. “The platform made such DDoS attacks accessible to a wide range of users, even those without any in-depth technical…
Read MoreNov 04, 2024Ravie LakshmananArtificial Intelligence / Vulnerability Google said it discovered a zero-day vulnerability in the SQLite open-source database engine using its large language model (LLM) assisted framework called Big Sleep (formerly Project Naptime). The tech giant described the development as the “first real-world vulnerability” uncovered using the artificial intelligence (AI) agent. “We believe this…
Read MoreCyber Threats That Could Impact the Retail Industry This Holiday Season (and What to Do About It)
by nlqip
As the holiday season approaches, retail businesses are gearing up for their annual surge in online (and in-store) traffic. Unfortunately, this increase in activity also attracts cybercriminals looking to exploit vulnerabilities for their gain. Imperva, a Thales company, recently published its annual holiday shopping cybersecurity guide. Data from the Imperva Threat Research team’s six-month analysis…
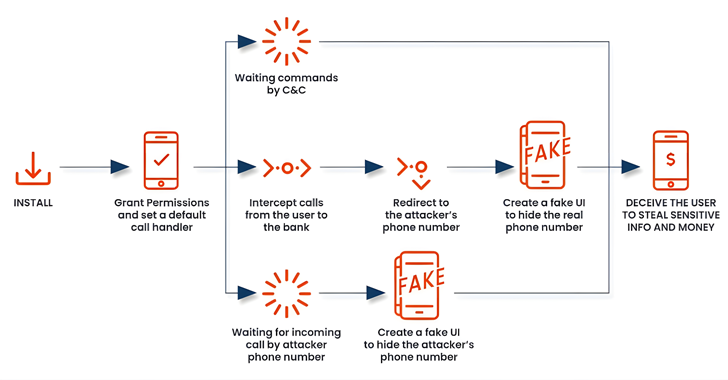
Read MoreNov 04, 2024Ravie LakshmananMobile Security / Financial Fraud Cybersecurity researchers have discovered a new version of a well-known Android malware family dubbed FakeCall that employs voice phishing (aka vishing) techniques to trick users into parting with their personal information. “FakeCall is an extremely sophisticated Vishing attack that leverages malware to take almost complete control of…
Read MoreThe change is meant ‘to ensure a more representative exposure to the semiconductors industry,’ according to S&P. A changing of the guard will happen before trading opens Nov. 8 among publicly traded chipmakers, with graphics processing unit and artificial intelligence heavyweight Nvidia taking Intel’s spot in the Dow Jones Industrial Average. S&P Dow Jones Indices,…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA




![German Police Disrupt DDoS-for-Hire Platform dstat[.]cc; Suspects Arrested](https://kartwheelnewz.info/wp-content/uploads/2024/11/German-Police-Disrupt-DDoS-for-Hire-Platform-dstatcc-Suspects-Arrested.png)