Category: Viral
Shadow apps, a segment of Shadow IT, are SaaS applications purchased without the knowledge of the security team. While these applications may be legitimate, they operate within the blind spots of the corporate security team and expose the company to attackers. Shadow apps may include instances of software that the company is already using. For…
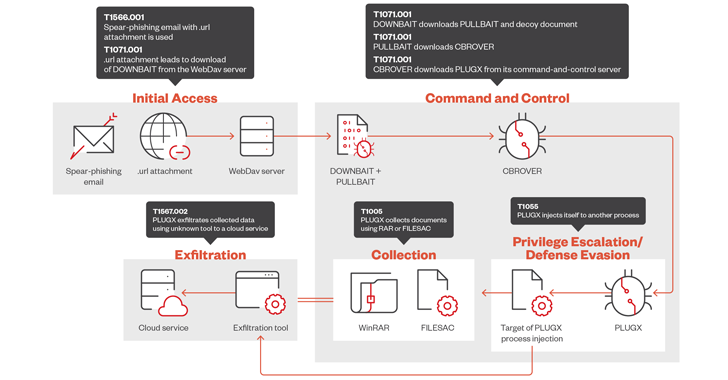
Read MoreSep 10, 2024Ravie LakshmananCyber Attack / Malware The threat actor tracked as Mustang Panda has refined its malware arsenal to include new tools in order to facilitate data exfiltration and the deployment of next-stage payloads, according to new findings from Trend Micro. The cybersecurity firm, which is monitoring the activity cluster under the name Earth…
Read MoreThe iPhone 16 series is arriving ahead of its much-hyped Apple Intelligence set of AI features, which will debut in beta next month with an initial set of features for the iPhone 15 Pro or higher as well as Macs and iPads with an M1 or newer system-on-chip. Apple said its newly revealed iPhone 16…
Read MoreSep 09, 2024Ravie LakshmananVulnerability / Hardware Security A novel side-channel attack has been found to leverage radio signals emanated by a device’s random access memory (RAM) as a data exfiltration mechanism, posing a threat to air-gapped networks. The technique has been codenamed RAMBO by Dr. Mordechai Guri, the head of the Offensive Cyber Research Lab…
Read MoreFrom a new Business Outcomes Xcelerator partner program to increasing incentives for MSPs, here are six new partner launches from AWS that every channel partner needs to know about. Amazon Web Services has unleashed a slew of new incentives, programs and AWS Marketplace benefits with the goal of streamlining partners’ go-to-market capabilities and drive faster…
Read MoreSep 09, 2024Ravie LakshmananCyber Espionage / Malware The China-linked advanced persistent threat (APT) group known as Mustang Panda has been observed weaponizing Visual Studio Code software as part of espionage operations targeting government entities in Southeast Asia. “This threat actor used Visual Studio Code’s embedded reverse shell feature to gain a foothold in target networks,”…
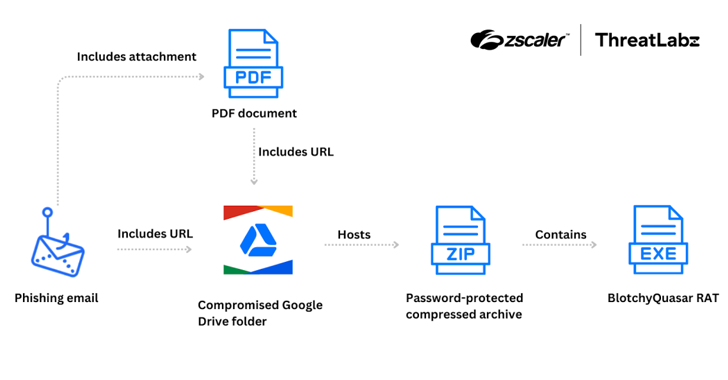
Read MoreSep 09, 2024Ravie LakshmananFinancial Security / Malware The Colombian insurance sector is the target of a threat actor tracked as Blind Eagle with the end goal of delivering a customized version of a known commodity remote access trojan (RAT) known as Quasar RAT since June 2024. “Attacks have originated with phishing emails impersonating the Colombian…
Read MoreSep 09, 2024The Hacker NewsData Protection / Threat Detection The proliferation of cybersecurity tools has created an illusion of security. Organizations often believe that by deploying a firewall, antivirus software, intrusion detection systems, identity threat detection and response, and other tools, they are adequately protected. However, this approach not only fails to address the fundamental…
Read More‘We saw the paradigm shift happening in telecom,’ LabLabee CEO Samir Tahraoui tells CRN in an interview. LabLabee, a startup that provides a platform for training workers at solution providers and vendors in the latest technology for networking, telecommunications and 5G use cases, has raised a $3.4 million seed round of funding as it prepares…
Read MoreWebinar: How to Protect Your Company from GenAI Data Leakage Without Losing It’s Productivity Benefits
by nlqip
Sep 09, 2024The Hacker NewsData Security / GenAI Security GenAI has become a table stakes tool for employees, due to the productivity gains and innovative capabilities it offers. Developers use it to write code, finance teams use it to analyze reports, and sales teams create customer emails and assets. Yet, these capabilities are exactly the…
Read More