Category: Viral
“This is a massive game changer, providing us for the first time a SOC (Security Operations Center) and high-quality security talent that is 24/7 responding to threats and managing customer cyber environments,” said Fulcrum IT Partners President Kyle Lanzinger. Fulcrum IT Partners, the $1 billion international solution provider behemoth, is adding more security services muscle…
Read More‘I didn’t make the decision to retire lightly,’ says Kirk Robinson, Ingram Micro executive vice president and president of North America. ‘But I’m beyond excited to spend more quality time with my family and friends, and paddle board on weekdays.’ Ingram Micro Executive Vice President and President of North America Kirk Robinson, a 31-year Ingram…
Read MoreNew partner program investments, AI innovation and cloud outages are among the biggest headlines so far. New partner program investments. Innovation in the artificial intelligence portfolio. And cloud outages and concerns around security. These are some of the ways Microsoft has captured headlines in 2024 so far as the Redmond, Wash.-based tech giant rides high…
Read More‘Amazon’s collaboration with Anthropic does not raise any competition concerns or meet the CMA’s own threshold for review,’ says an Amazon spokesperson regarding the investigation by the U.K. Competition and Markets Authority. A U.K. antitrust watchdog agency said it has “sufficient information” to start an investigation into whether Amazon’s $4 billion investment and partnership with…
Read MoreAug 08, 2024The Hacker NewsCyber Threat Management The last few years have seen more than a few new categories of security solutions arise in hopes of stemming a never-ending tidal wave of risks. One of these categories is Automated Security Validation (ASV), which provides the attacker’s perspective of exposures and equips security teams to continuously…
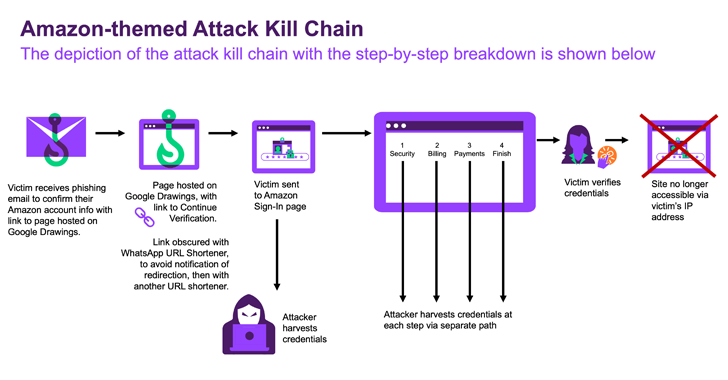
Read MoreAug 08, 2024Ravie LakshmananNetwork Security / Cloud Security Cybersecurity researchers have discovered a novel phishing campaign that leverages Google Drawings and shortened links generated via WhatsApp to evade detection and trick users into clicking on bogus links designed to steal sensitive information. “The attackers chose a group of the best-known websites in computing to craft…
Read MoreAug 08, 2024Ravie LakshmananCritical Infrastructure / Malware The ransomware strain known as BlackSuit has demanded as much as $500 million in ransoms to date, with one individual ransom demand hitting $60 million. That’s according to an updated advisory from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI). “BlackSuit…
Read MoreBusiness Security Having knowledgeable leaders at the helm is crucial for protecting the organization and securing the best possible cyber insurance coverage 07 Aug 2024 • , 4 min. read The board does not understand cybersecurity – that’s not so anymore. Prior to the pandemic, the CISO and cybersecurity team were seen as the geeks…
Read MoreIn addition to major product launches, cybersecurity vendors also announced fundings, acquisitions and key hires this week in Las Vegas. Big Moves At Black Hat Along with an abundance of product launches this week in Las Vegas, numerous cybersecurity vendors have announced other major moves in connection with the Black Hat 2024 conference. Security giant…
Read MoreSolution provider silver and gold benefits “remain in effect for one year after your last purchase or renewal, but they will not undergo the January 2025 update,” Microsoft said. Microsoft revealed that it plans to no longer sell its Action Pack, Learning Action Pack or legacy silver and gold benefits starting Jan. 22 – and…
Read MoreRecent Posts
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’
- Botnet exploits GeoVision zero-day to install Mirai malware
- FTC reports 50% drop in unwanted call complaints since 2021
- Bitfinex hacker gets 5 years in prison for 120,000 bitcoin heist