Category: Viral
Unless there’s a concerted effort by a lot more tech industry vendors than just CrowdStrike, it’s unlikely to be the last incident of this kind. Within the software industry, it has long been a cliche´ to point out the inevitability of bugs. As the thinking goes, the world of software is insanely complex, and the…
Read MoreThe email security vendor will add 175 employees with the acquisition of 23-year-old Code42, the company says. Email security vendor Mimecast will add 175 employees with the acquisition of longtime cybersecurity vendor Code42, the company announced Wednesday. Mimecast did not disclose the terms of the acquisition. Joe Payne (pictured), Code42’s president and CEO since 2015,…
Read MoreIn the past few months, the Telegram clicker game Hamster Kombat has taken the world of cryptocurrency game enthusiasts by storm. Even though the gameplay, which mostly entails repeatedly tapping the screen of one’s mobile device, might be rather simple, players are after something more: the possibility of earning big once Hamster Kombat’s creators unveil…
Read MoreDigital Security Organizations, including those that weren’t struck by the CrowdStrike incident, should resist the temptation to attribute the IT meltdown to exceptional circumstances 23 Jul 2024 • , 3 min. read As the dust settles on the cyber-incident caused by CrowdStrike releasing a corrupted update, many businesses will, or should, conduct a thorough post-mortem…
Read More‘Year-to-date, our AI infrastructure and generative AI solutions for Cloud customers have already generated billions in revenues and are being used by more than 2 million developers,’ said Google CEO Sundar Pichai during the company’s recent Q2 2024 earnings report. Google CEO Sundar Pichai during the company’s second quarter 2024 earnings call spoke bullishly about…
Read MoreHere’s everything you need to know about the new VMware Cloud Foundation on Google Cloud VMware Engine offering, incentives, price cuts and how it relates to Microsoft Azure and AWS’ VMware cloud solutions. Google Cloud is putting the full court press on urging VMware Cloud Foundation customers to migrate their VMware workloads over to Google…
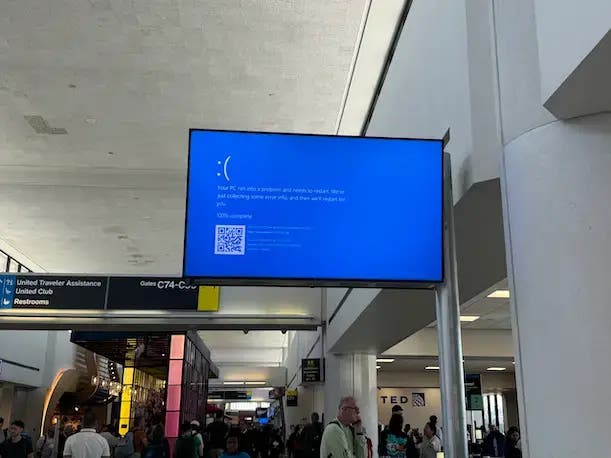
Read MoreThe CrowdStrike-Microsoft Outage Is Likely To Curtail Auto-Updates. That May Not Be A Good Thing.
by nlqip
If customers opt to forgo automatic security updates going forward to ensure greater testing, the ‘whole IT environment is exposed’ during that testing period, a CrowdStrike partner tells CRN. The massively disruptive CrowdStrike-Microsoft outage will undoubtedly lead more customers to forgo automatic updates to reduce the chances of a similar event occurring again. But this…
Read MoreThe HashiCorp acquisition, GenAI and Red Hat taking on VMware are likely to come up. Updates on the HashiCorp acquisition. Details on IBM’s approach to the artificial intelligence gold rush. And IBM subsidiary Red Hat taking on VMware and legacy virtualization vendors. These are just some of the topics analysts will likely bring up Wednesday…
Read MoreA bug in CrowdStrike’s content approval system ‘passed validation despite containing problematic content data,’ leading to the outage that caused global disruptions. A bug in CrowdStrike’s validation process for security configuration updates resulted in the Microsoft Windows outage that led to global disruptions starting Friday, the company said Wednesday. The widely felt snafu involved what…
Read MoreVC investor Nadav Zafrir will replace Gil Shwed as Check Point CEO in December. Check Point Software Technologies said Wednesday that venture capitalist Nadav Zafrir will replace Gil Shwed as CEO of the cybersecurity vendor in December, in a major transition following Shwed’s three decades at the helm of the company. Shwed played a chief…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm