Category: Viral
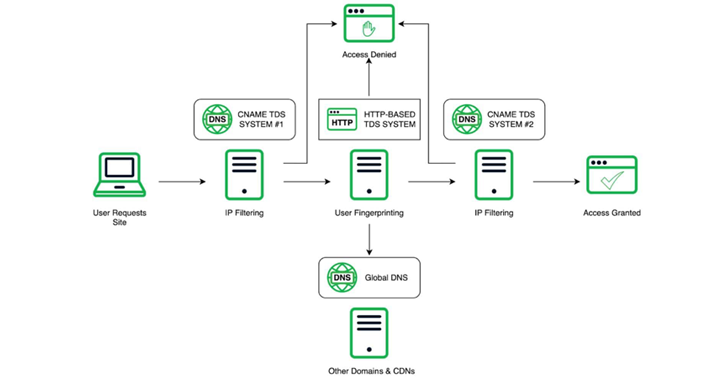
The relationship between various TDSs and DNS associated with Vigorish Viper and the final landing experience for the user A Chinese organized crime syndicate with links to money laundering and human trafficking across Southeast Asia has been using an advanced “technology suite” that runs the whole cybercrime supply chain spectrum to spearhead its operations. Infoblox…
Read More‘As a follow-up to the CrowdStrike Falcon agent issue impacting Windows clients and servers, Microsoft has released an updated recovery tool with two repair options to help IT admins expedite the repair process,’ Microsoft says. Following the faulty CrowdStrike update that caused chaos for millions of Microsoft customers and businesses, the software giant has now…
Read MoreMSPs & MSSPs: How to Increase Engagement with Your Cybersecurity Clients Through vCISO Reporting
by nlqip
As a vCISO, you are responsible for your client’s cybersecurity strategy and risk governance. This incorporates multiple disciplines, from research to execution to reporting. Recently, we published a comprehensive playbook for vCISOs, “Your First 100 Days as a vCISO – 5 Steps to Success”, which covers all the phases entailed in launching a successful vCISO…
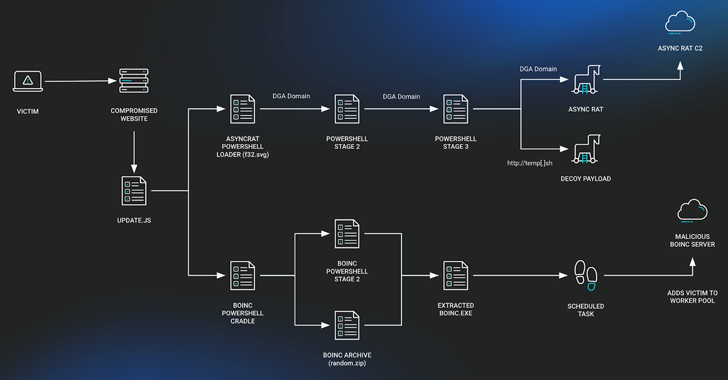
Read MoreJul 22, 2024NewsroomVulnerability / Malware The JavaScript downloader malware known as SocGholish (aka FakeUpdates) is being used to deliver a remote access trojan called AsyncRAT as well as a legitimate open-source project called BOINC. BOINC, short for Berkeley Open Infrastructure Network Computing Client, is an open-source “volunteer computing” platform maintained by the University of California…
Read MoreHow a legitimate and signed driver left the doors open to threats – Week in Security with Tony Anscombe
by nlqip
Video A purported ad blocker marketed as a security solution hides kernel-level malware that inadvertently exposes victims to even more dangerous threats 21 Jul 2024 This week, ESET researchers have released their findings about HotPage, a browser injector that leverages a driver developed by a Chinese company and signed by Microsoft. The malware masquerades as…
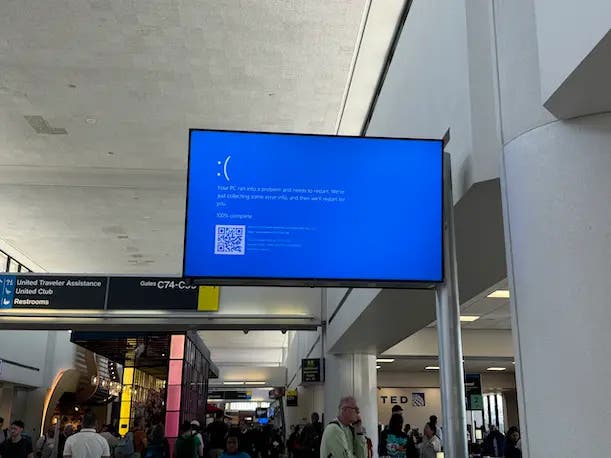
Read MoreMajor airlines reported progress on recovery from the outage Saturday. Microsoft disclosed Saturday that 8.5 million Windows devices were impacted by CrowdStrike’s disastrous update, while major airlines reported progress on recovery from the massive outage. The CrowdStrike Falcon update led to the “blue screen of death” for Windows systems worldwide on Friday and hobbled much…
Read MoreJul 20, 2024NewsroomMalware / IT Outage Cybersecurity firm CrowdStrike, which is facing the heat for causing worldwide IT disruptions by pushing out a flawed update to Windows devices, is now warning that threat actors are exploiting the situation to distribute Remcos RAT to its customers in Latin America under the guise of a providing a…
Read MoreIt remains unclear exactly why the hugely disruptive error occurred, the company says—especially given that such updates are very common. CrowdStrike said the unprecedented Microsoft outage felt worldwide stemmed from a programming error that was triggered as part of a common update process—prompting further questions about how the massively disruptive error could have occurred. The…
Read MoreDigital Security If a software update process fails, it can lead to catastrophic consequences, as seen today with widespread blue screens of death blamed on a bad update by CrowdStrike 19 Jul 2024 • , 2 min. read Cybersecurity is often about speed; a threat actor creates a malicious attack technique or code, cybersecurity companies…
Read MoreDigital Security The widespread IT outages triggered by a faulty CrowdStrike update have put software updates in the spotlight. Here’s why you shouldn’t dread them. 19 Jul 2024 • , 3 min. read In the realm of computing, few things are as unsettling as encountering a blue screen of death (BSOD) on your Windows system.…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm