Category: Viral
AT&T Corp. disclosed today that a new data breach has exposed phone call and text message records for roughly 110 million people — nearly all of its customers. AT&T said it delayed disclosing the incident in response to “national security and public safety concerns,” noting that some of the records included data that could be…
Read MoreHere’s a look at 10 open-source software tools – many for building AI applications or managing huge volumes of data – that are either already widely used or are gaining in popularity. A Software Free-For-All Open-source software tools continue to increase in popularity because of the multiple advantages they provide including lower upfront software and…
Read More‘Everyone wants to get off of VMware and get into the cloud,’ Microsoft Chief Commercial Officer Judson Althoff says. Microsoft’s new fiscal year has kicked off with hundreds of millions of dollars in partner incentives around security, Copilot and more – and one Microsoft executive took time to thank virtualization and desktop-as-a-service rival VMware for…
Read More‘Microsoft achieves reach, scale and success because of you,’ says Nicole Dezen, Microsoft chief partner officer. Microsoft plans more than $150 million in pre-sales and post-sales investments for its Azure Innovate offering, an incremental $90 million “to accelerate security growth” with partners and a tenfold increase to its Copilot partner investment as part of a…
Read MoreAdvance Auto Parts disclosed that data belonging to 2.3 million customers was exposed in an April attack targeting its Snowflake deployment. More details have emerged on what appears to have been another serious data breach linked to a campaign targeting Snowflake customers, with Advance Auto Parts disclosing that data belonging to more than 2 million…
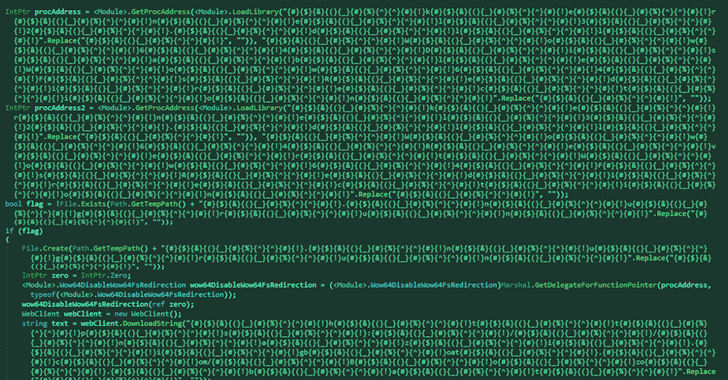
Read MoreJul 11, 2024NewsroomSoftware Security / Threat Intelligence Threat actors have been observed publishing a new wave of malicious packages to the NuGet package manager as part of an ongoing campaign that began in August 2023, while also adding a new layer of stealth to evade detection. The fresh packages, about 60 in number and spanning…
Read MoreCISA Red Team’s Operations Against a Federal Civilian Executive Branch Organization Highlights the Necessity of Defense-in-Depth | CISA
by nlqip
EXECUTIVE SUMMARY In early 2023, the Cybersecurity and Infrastructure Security Agency (CISA) conducted a SILENTSHIELD red team assessment against a Federal Civilian Executive Branch (FCEB) organization. During SILENTSHIELD assessments, the red team first performs a no-notice, long-term simulation of nation-state cyber operations. The team mimics the techniques, tradecraft, and behaviors of sophisticated threat actors and…
Read MoreGartner recognized nine vendors in the latest edition of its Magic Quadrant ranking for single-vendor SASE. SASE Magic Quadrant As organizations continue to prioritize providing remote access to distributed teams in 2024, demand for security and networking capabilities to enable hybrid teams continues to surge. And increasingly, customers are looking for a unified technology platform—and…
Read MoreVideo, Internet of Things As security challenges loom large on the IoT landscape, how can we effectively counter the risks of integrating our physical and digital worlds? 10 Jul 2024 Imagine all traffic lights in a city turning green simultaneously, much like in Die Hard 4. Could a movie plot become a reality? Does it…
Read MoreJul 11, 2024NewsroomSoftware Security / Vulnerability ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm