CISA has added five new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-27348 Apache HugeGraph-Server Improper Access Control Vulnerability CVE-2020-0618 Microsoft SQL Server Reporting Services Remote Code Execution Vulnerability Microsoft Windows Task Scheduler Privilege Escalation Vulnerability CVE-2022-21445 Oracle JDeveloper Remote Code Execution Vulnerability CVE-2020-14644 Oracle WebLogic Server Remote Code Execution Vulnerability…
Read More‘I want to see more entrepreneurial thinking and a limitless mindset among MSP leaders. Many small to midsize MSPs are the backbone of our economy, and I believe they can achieve great things by thinking beyond their immediate environments and embracing innovative strategies,’ says Sunny Kaila, CEO of IT By Design. Sunny Kaila wants to…
Read MoreChinese Engineer Charged in U.S. for Years-Long Cyber Espionage Targeting NASA and Military
by nlqip
A Chinese national has been indicted in the U.S. on charges of conducting a “multi-year” spear-phishing campaign to obtain unauthorized access to computer software and source code created by the National Aeronautics and Space Administration (NASA), research universities, and private companies. Song Wu, 39, has been charged with 14 counts of wire fraud and 14…
Read MoreESET Research ESET researchers discuss how they uncovered a zero-day Telegram for Android exploit that allowed attackers to send malicious files posing as videos 17 Sep 2024 • , 1 min. read Telegram, with nearly a billion monthly users, is a juicy target for cybercriminals, especially if they can exploit a zero-day vulnerability to spread…
Read MoreConfluent Launches OEM Program To Help ISV And MSP Partners Build Data Streaming Into Their Offerings
by nlqip
Confluent also discloses investments in two regional systems integration partners who are developing leading-edge data integration and migration expertise and practices. Data streaming tech developer Confluent has launched an OEM channel program to recruit managed service providers, cloud service providers and independent software vendors to build the Confluent platform within their software and service offerings.…
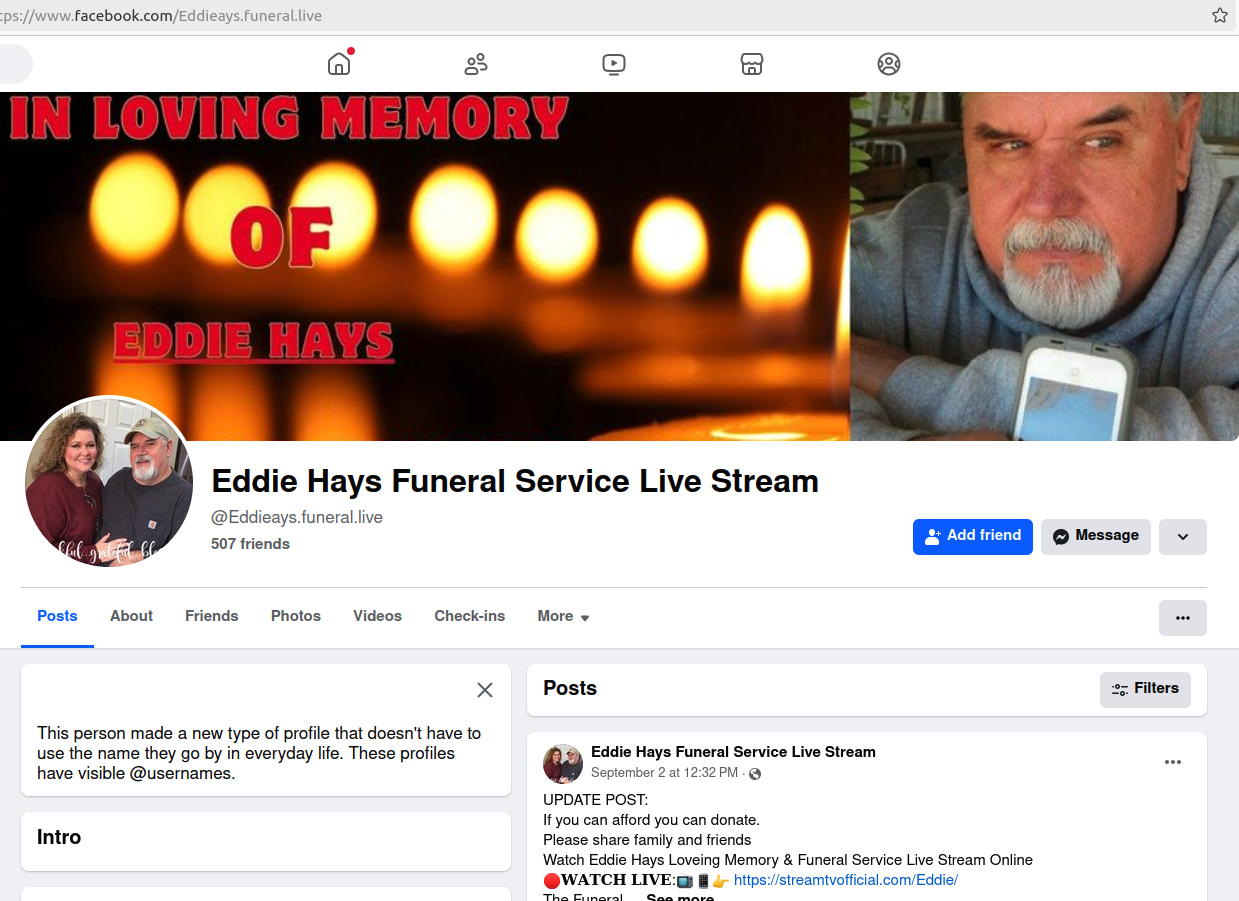
Read MoreScammers are flooding Facebook with groups that purport to offer video streaming of funeral services for the recently deceased. Friends and family who follow the links for the streaming services are then asked to cough up their credit card information. Recently, these scammers have branched out into offering fake streaming services for nearly any kind…
Read MoreA New Edge For HPE: Why The Nvidia AI-Ready ProLiant DL145 Gen11 Server Is A ‘Big Breakthrough’
by nlqip
Hewlett Packard Enterprise is pushing the edge computing price performance envelope with a 2U Nvidia AI Ready ProLiant DL145 Gen11 server priced starting at just $2,065 for a configure to order chassis. A ‘Big Breakthrough’ At The Edge Hewlett Packard Enterprise’s new 2U Nvidia AI ready ProLiant DL145 is aimed at once and for all…
Read More“We’re going to do ourselves a disservice … as an industry if we push people too fast into AI and we don’t give real solutions,” Insight SVP Stephen Moss tells CRN. Artificial intelligence as a service. Managed AI. AI assurance. Solution providers are at work sorting through new practices and new ways to not only…
Read More6 Big Intel Changes, Wins Outlined By CEO: AWS Chip Deal, Independent Foundry, Factory Delays
by nlqip
In a Monday letter to employees, Intel CEO Pat Gelsinger outlined changes that will help the beleaguered chipmaker save billions of dollars and bounce back financially while highlighting a new multibillion-dollar chip deal with Amazon Web Services. Intel CEO Pat Gelsinger said the company plans to turn its contract chip manufacturing business into an independent…
Read MoreThe evolution of software always catches us by surprise. I remember betting against the IBM computer Deep Blue during its chess match against the grandmaster Garry Kasparov in 1997, only to be stunned when the machine claimed victory. Fast forward to today, would we have imagined just three years ago that a chatbot could write…
Read MoreRecent Posts
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption
- New Glove Stealer malware bypasses Chrome’s cookie encryption