From zero-day exploits to polymorphic malware, today’s organizations must protect themselves against increasingly sophisticated cyber threats. But while these types of complex attack vectors may be making the news, the reality is that your organization can’t afford to neglect the persistent threat of brute force attacks. What brute force methods lack in finesse, they make up for in sheer…
Read More3ds — 3dexperience A stored Cross-site Scripting (XSS) vulnerability affecting 3DDashboard in 3DSwymer Release on 3DEXPERIENCE R2024x allows an attacker to execute arbitrary script code in user’s browser session. 2024-09-02 5.4 CVE-2024-7932 3DS.Information-Security@3ds.com 3ds — 3dexperience A stored Cross-site Scripting (XSS) vulnerability affecting 3DDashboard in 3DSwymer from Release 3DEXPERIENCE R2023x through Release 3DEXPERIENCE R2024x allows…
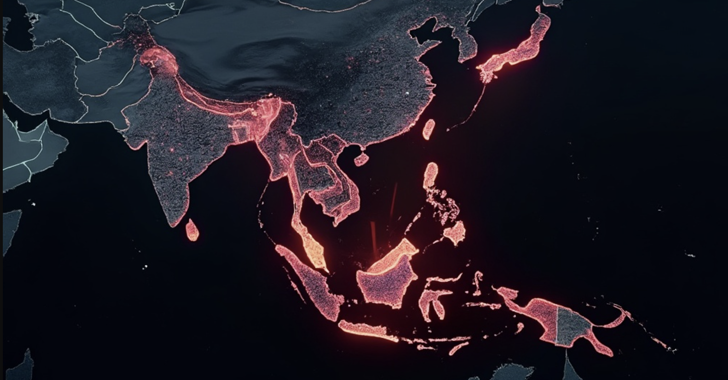
Read MoreSep 09, 2024Ravie LakshmananCyber Espionage / Malware The China-linked advanced persistent threat (APT) group known as Mustang Panda has been observed weaponizing Visual Studio Code software as part of espionage operations targeting government entities in Southeast Asia. “This threat actor used Visual Studio Code’s embedded reverse shell feature to gain a foothold in target networks,”…
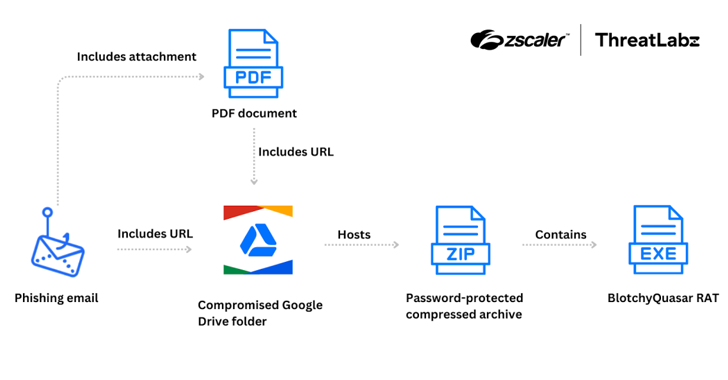
Read MoreSep 09, 2024Ravie LakshmananFinancial Security / Malware The Colombian insurance sector is the target of a threat actor tracked as Blind Eagle with the end goal of delivering a customized version of a known commodity remote access trojan (RAT) known as Quasar RAT since June 2024. “Attacks have originated with phishing emails impersonating the Colombian…
Read MoreSep 09, 2024The Hacker NewsData Protection / Threat Detection The proliferation of cybersecurity tools has created an illusion of security. Organizations often believe that by deploying a firewall, antivirus software, intrusion detection systems, identity threat detection and response, and other tools, they are adequately protected. However, this approach not only fails to address the fundamental…
Read More‘We saw the paradigm shift happening in telecom,’ LabLabee CEO Samir Tahraoui tells CRN in an interview. LabLabee, a startup that provides a platform for training workers at solution providers and vendors in the latest technology for networking, telecommunications and 5G use cases, has raised a $3.4 million seed round of funding as it prepares…
Read MoreWebinar: How to Protect Your Company from GenAI Data Leakage Without Losing It’s Productivity Benefits
by nlqip
Sep 09, 2024The Hacker NewsData Security / GenAI Security GenAI has become a table stakes tool for employees, due to the productivity gains and innovative capabilities it offers. Developers use it to write code, finance teams use it to analyze reports, and sales teams create customer emails and assets. Yet, these capabilities are exactly the…
Read More‘We are super excited to scale and become a North America superpower,’ says Blue Mantis CEO Josh Dinneen, who is already in discussions with three potential acquisition targets. Blue Mantis is stepping up its fast growth security-first, next-generation technology service provider sales offensive under a new private equity majority owner, Recognize. The New York-headquartered Recognize,…
Read MoreSep 09, 2024Ravie LakshmananVulnerability / Enterprise Security Progress Software has released security updates for a maximum-severity flaw in LoadMaster and Multi-Tenant (MT) hypervisor that could result in the execution of arbitrary operating system commands. Tracked as CVE-2024-7591 (CVSS score: 10.0), the vulnerability has been described as an improper input validation bug that results in OS…
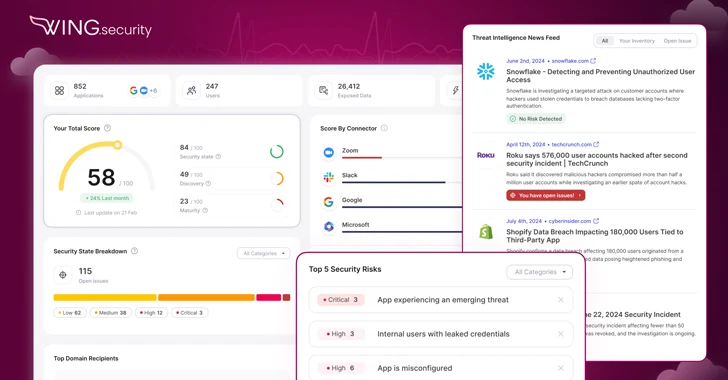
Read MoreSep 09, 2024The Hacker NewsSaaS Security / Risk Management Designed to be more than a one-time assessment— Wing Security’s SaaS Pulse provides organizations with actionable insights and continuous oversight into their SaaS security posture—and it’s free! Introducing SaaS Pulse: Free Continuous SaaS Risk Management Just like waiting for a medical issue to become critical before…
Read MoreRecent Posts
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’
- Botnet exploits GeoVision zero-day to install Mirai malware
- FTC reports 50% drop in unwanted call complaints since 2021
- Bitfinex hacker gets 5 years in prison for 120,000 bitcoin heist