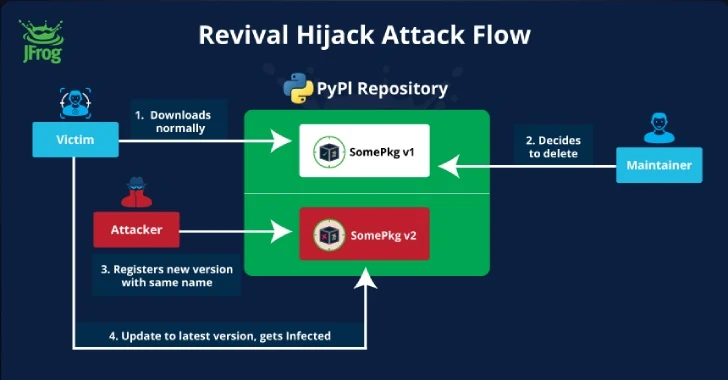
Sep 04, 2024Ravie Lakshmanan A new supply chain attack technique targeting the Python Package Index (PyPI) registry has been exploited in the wild in an attempt to infiltrate downstream organizations. It has been codenamed Revival Hijack by software supply chain security firm JFrog, which said the attack method could be used to hijack 22,000 existing…
Read MoreTenable®, the exposure management company, today announced new risk prioritization and compliance features for Tenable Nessus, the #1 vulnerability assessment solution in accuracy, coverage and adoption. Nessus supports new and updated vulnerability scoring systems – Exploit Prediction Scoring System (EPSS) and Common Vulnerability Scoring System (CVSS) v4 – to help customers implement more effective prioritization…
Read More“We’ve been working closely with customers to evaluate and test these new devices, and the feedback has been incredible,” Microsoft GM Nancie Gaskill said in a blog post. Microsoft will make several new Surface devices aimed at business users available this month, including the Surface Laptop 7th Edition, Surface Pro 11th Edition and Surface Pro…
Read MoreSep 04, 2024Ravie LakshmananVulnerability / Network Security Zyxel has released software updates to address a critical security flaw impacting certain access point (AP) and security router versions that could result in the execution of unauthorized commands. Tracked as CVE-2024-7261 (CVSS score: 9.8), the vulnerability has been described as a case of operating system (OS) command…
Read MoreSep 04, 2024The Hacker NewsSaaS Security / Browser Security Account takeover attacks have emerged as one of the most persistent and damaging threats to cloud-based SaaS environments. Yet despite significant investments in traditional security measures, many organizations continue to struggle with preventing these attacks. A new report, “Why Account Takeover Attacks Still Succeed, and Why…
Read MoreSecurity Researcher Sued for Disproving Government Statements This story seems straightforward. A city is the victim of a ransomware attack. They repeatedly lie to the media about the severity of the breach. A security researcher repeatedly proves their statements to be lies. The city gets mad and sues the researcher. Let’s hope the judge throws…
Read MoreHuman error remains a significant risk for organizations when it comes to cyber threats. In fact, according to Proofpoint’s 2024 Voice of the CISO report, 74% of CISOs view human error as their organization’s biggest cyber vulnerability. However, 86% of CISOs believe employees understand their role in protecting the organization, which gives them hope for…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/cybersecurity-in-a-cycle-balancing-repair-and-replacement-for-optimal-security” on this server. Reference #18.ded7ce17.1725444493.836f6e1b https://errors.edgesuite.net/18.ded7ce17.1725444493.836f6e1b Source link lol
Read MoreSep 04, 2024Ravie LakshmananGDPR / Privacy The Dutch Data Protection Authority (Dutch DPA) has imposed a fine of €30.5 million ($33.7 million) against facial recognition firm Clearview AI for violating the General Data Protection Regulation (GDPR) in the European Union (E.U.) by building an “illegal database with billions of photos of faces,” including those of…
Read MoreGranted, such low-level activities don’t produce the same worker anxiety or organizational confusion that downsizing and M&As do — and, thus, don’t present the same opportunities for hackers. However, Carruthers says they still create changes that hackers can use to their advantage. “They all breed opportunities for attackers.” Carruthers knows firsthand how effective such hacker…
Read MoreRecent Posts
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’
- Botnet exploits GeoVision zero-day to install Mirai malware
- FTC reports 50% drop in unwanted call complaints since 2021