10up–Simple Local Avatars Cross-Site Request Forgery (CSRF) vulnerability in 10up Simple Local Avatars.This issue affects Simple Local Avatars: from n/a through 2.7.10. 2024-08-26 4.3 CVE-2024-43116audit@patchstack.com advancedformintegration — advanced_form_integration Cross-Site Request Forgery (CSRF) vulnerability in Nasirahmed Advanced Form Integration.This issue affects Advanced Form Integration: from n/a through 1.89.4. 2024-08-26 4.3 CVE-2024-43340audit@patchstack.com Analytify–Analytify Cross-Site Request Forgery (CSRF)…
Read MoreCISA released one Industrial Control Systems (ICS) advisory on September 3, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. CISA encourages users and administrators to review newly released ICS advisories for technical details and mitigations. Source link lol
Read MoreSep 03, 2024Ravie LakshmananEndpoint Security / Malware Cybersecurity researchers have unpacked the inner workings of a new ransomware variant called Cicada3301 that shares similarities with the now-defunct BlackCat (aka ALPHV) operation. “It appears that Cicada3301 ransomware primarily targets small to medium-sized businesses (SMBs), likely through opportunistic attacks that exploit vulnerabilities as the initial access vector,”…
Read MoreSep 03, 2024Ravie LakshmananRansomware / Malware A hacktivist group known as Head Mare has been linked to cyber attacks that exclusively target organizations located in Russia and Belarus. “Head Mare uses more up-to-date methods for obtaining initial access,” Kaspersky said in a Monday analysis of the group’s tactics and tools. “For instance, the attackers took…
Read MoreThree men have pleaded guilty to running OTP.Agency, an online platform that provided social engineering help to obtain one-time passcodes from customers of various banks and services in the U.K. The codes – temporary passwords also known as OTPs, were part of multi-factor authentication protections and criminals subscribing to the illegal service could use them to access…
Read MoreOil and gas giant Halliburton has confirmed in a filing today to the Securities and Exchange Commission (SEC) that data was stolen in the recent attack linked to the RansomHub ransomware gang. The form 8-K filing mentions that an unauthorized third party accessed and exfiltrated sensitive information from Halliburton systems, and the company is now…
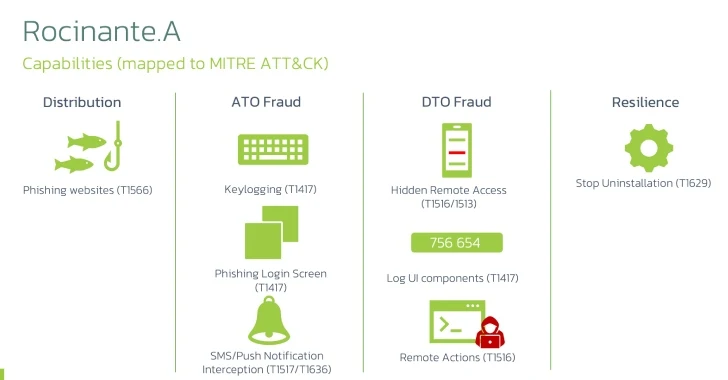
Read MoreRocinante Trojan Poses as Banking Apps to Steal Sensitive Data from Brazilian Android Users
by nlqip
Mobile users in Brazil are the target of a new malware campaign that delivers a new Android banking trojan named Rocinante. “This malware family is capable of performing keylogging using the Accessibility Service, and is also able to steal PII from its victims using phishing screens posing as different banks,” Dutch security company ThreatFabric said.…
Read MoreBackwards compatibility takes us … backwards Unfortunately, once you keep support for old, vulnerable versions of your software, people will continue to use old, vulnerable versions of your software. Vendors shrugged their shoulders, and pundits blamed software users for choosing to use a working-but-vulnerable version instead of a broken-but-patched version (as if that was a…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/the-human-factor-in-cybersecurity-behavioral-insights-and-mitigation-strategies” on this server. Reference #18.ead7ce17.1725358051.c5c0dfce https://errors.edgesuite.net/18.ead7ce17.1725358051.c5c0dfce Source link lol
Read MoreIn the digital realm, secrets (API keys, private keys, username and password combos, etc.) are the keys to the kingdom. But what if those keys were accidentally left out in the open in the very tools we use to collaborate every day? A Single Secret Can Wreak Havoc Imagine this: It’s a typical Tuesday in…
Read MoreRecent Posts
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’
- Botnet exploits GeoVision zero-day to install Mirai malware