In the digital realm, secrets (API keys, private keys, username and password combos, etc.) are the keys to the kingdom. But what if those keys were accidentally left out in the open in the very tools we use to collaborate every day? A Single Secret Can Wreak Havoc Imagine this: It’s a typical Tuesday in…
Read MoreOn the other hand, risk tolerance needs to be a guided discussion around a particular objective or a risk scenario, where a CISO can develop a hypothesis. “If you can be explicit, if you can describe it well, then you can really have a good conversation to get everyone on the same page as to…
Read MoreEight vulnerabilities have been uncovered in Microsoft applications for macOS that an adversary could exploit to gain elevated privileges or access sensitive data by circumventing the operating system’s permissions-based model, which revolves around the Transparency, Consent, and Control (TCC) framework. “If successful, the adversary could gain any privileges already granted to the affected Microsoft applications,”…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-094 DATE(S) ISSUED: 09/03/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated…
Read MoreSep 03, 2024Ravie LakshmananInsider Threat / Network Security A 57-year-old man from the U.S. state of Missouri has been arrested in connection with a failed data extortion campaign that targeted his former employer. Daniel Rhyne of Kansas City, Missouri, has been charged with one count of extortion in relation to a threat to cause damage…
Read MoreTransport for London (TfL), the city’s transport authority, is investigating an ongoing cyberattack that has yet to impact its services. The agency also added that there was no evidence that customer information was compromised during the incident. “We are currently dealing with an ongoing cyber security incident,” TfL’s Customer Information Team warned customers over email…
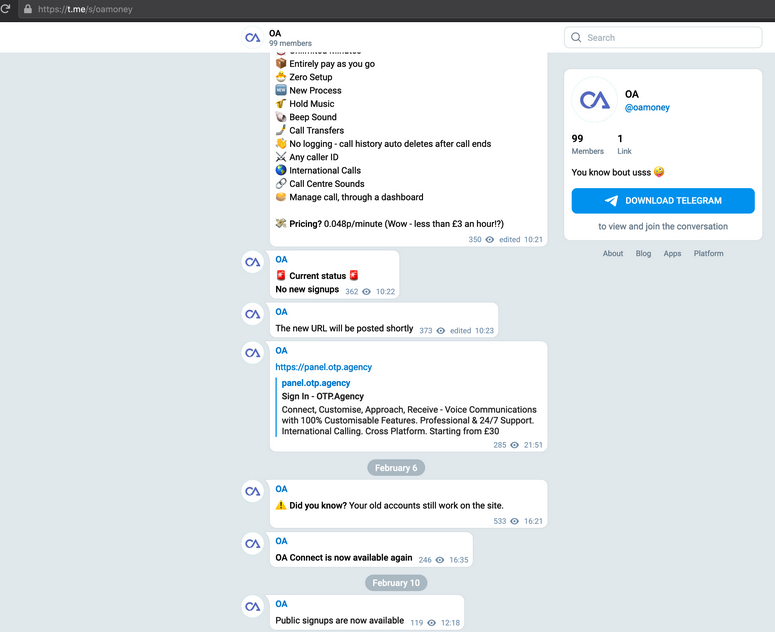
Read MoreThree men have pleaded guilty to running OTP.Agency, an online platform that provided social engineering help to obtain one-time passcodes from customers of various banks and services in the U.K. The codes – temporary passwords also known as OTPs, were part of multi-factor authentication protections and criminals subscribing to the illegal service could use them to access…
Read MoreThree men in the United Kingdom have pleaded guilty to operating otp[.]agency, a once popular online service that helped attackers intercept the one-time passcodes (OTPs) that many websites require as a second authentication factor in addition to passwords. Launched in November 2019, OTP Agency was a service for intercepting one-time passwords needed to log in…
Read MoreThe Federal Trade Commission (FTC) proposes a $2.95 million penalty on security camera vendor Verkada for multiple security failures that enabled hackers to access live video feeds from 150,000 internet-connected cameras. Many of the cameras were located in sensitive environments, such as women’s health clinics, psychiatric hospitals, prisons, and schools. FTC alleges that Verkada not only failed…
Read MoreImage: Midjourney A new ransomware-as-a-service (RaaS) operation is impersonating the legitimate Cicada 3301 organization and has already listed 19 victims on its extortion portal, as it quickly attacked companies worldwide. The new cybercrime operation is named after and uses the same logo as the mysterious 2012-2014 online/real-world game named Circada 3301 that involved elaborate cryptographic puzzles.…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’