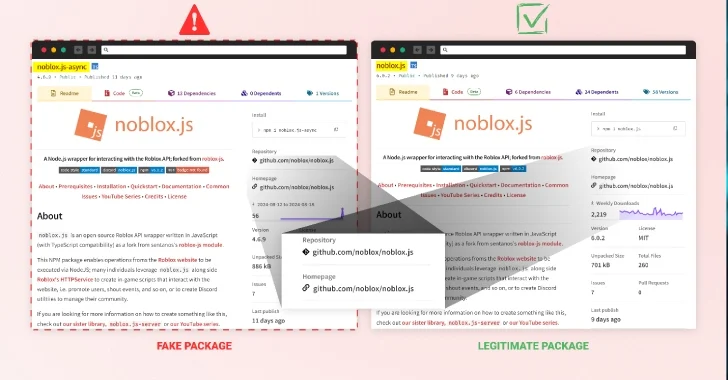
Sep 02, 2024Ravie LakshmananSoftware Security / Malware Roblox developers are the target of a persistent campaign that seeks to compromise systems through bogus npm packages, once again underscoring how threat actors continue to exploit the trust in the open-source ecosystem to deliver malware. “By mimicking the popular ‘noblox.js’ library, attackers have published dozens of packages…
Read MoreImage: Midjourney A new ransomware-as-a-service (RaaS) operation named Cicada3301 has already listed 19 victims on its extortion portal, as it quickly attacked companies worldwide. The new cybercrime operation is named after the mysterious 2012-2014 online/real-world game that involved elaborate cryptographic puzzles and used the same logo for promotion on cybercrime forums. However, it is unlikely…
Read MoreThe popular Docker-OSX project has been removed from Docker Hub after Apple filed a DMCA (Digital Millennium Copyright Act) takedown request, alleging that it violated its copyright. Docker-OSX is an open-source project created by security researcher Sick.Codes that allows for the virtualization of macOS on non-Apple hardware. It can be hosted on any system that…
Read MoreGitHub is being abused to distribute the Lumma Stealer information-stealing malware as fake fixes posted in project comments. The campaign was first reported by a contributor to the teloxide rust library, who noted on Reddit that they received five different comments in their GitHub issues that pretended to be fixes but were instead pushing malware. Further review…
Read MoreAug 31, 2024Ravie LakshmananRootkit / Threat Intelligence A recently patched security flaw in Google Chrome and other Chromium web browsers was exploited as a zero-day by North Korean actors in a campaign designed to deliver the FudModule rootkit. The development is indicative of the persistent efforts made by the nation-state adversary, which had made a…
Read More“You [as a woman] have to have a very thick skin and a spine of steel to last a very long time in this industry,” she said. “Every woman I know who is a leader has the same — very tough skin and a spine of steel.” Women in cybersecurity statistics The ISC2, a nonprofit…
Read MoreFriday Squid Blogging: Economic Fallout from Falklands Halting Squid Fishing Details. Blog moderation policy. Tags: squid Posted on August 30, 2024 at 5:04 PM • Sidebar photo of Bruce Schneier by Joe MacInnis. Source link lol
Read MoreWindows 11’s Spotlight feature is a pretty nice way to jazz up your desktop background with different wallpapers and fun facts when you hover over the image icon. The problem with the current approach is that it takes up a good amount of space on the desktop when you try to learn more about the…
Read MoreSecurity researchers have found a vulnerability in a key air transport security system that allowed unauthorized individuals to potentially bypass airport security screenings and gain access to aircraft cockpits. Researchers Ian Carroll and Sam Curry discovered the vulnerability in FlyCASS, a third-party web-based service that some airlines use to manage the Known Crewmember (KCM) program…
Read MoreFor the week ending Aug. 30, CRN takes a look at the companies that brought their ‘A’ game to the channel including Cribl, Check Point, Intel, Citrix and IBM. The Week Ending Aug. 30 Topping this week’s Came to Win list is data management and observability tech developer Cribl for its very impressive nine-figure funding…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’