DICK’S Sporting Goods, the largest chain of sporting goods retail stores in the United States, disclosed that confidential information was exposed in a cyberattack detected last Wednesday. Founded in 1948, DICK’S operates 857 stores across the United States and has reported $12.98 billion in revenue in 2023. As of February 2024, the Fortune 500 company…
Read MoreAI PCs, traditional PCs and printers are subjects likely to come up on the company’s earnings call. Sales of new PCs crafted for the artificial intelligence era. A potential recovery in the traditional PC market. And possible continued troubles for printers. These are some of the major subjects expected to come up Wednesday when Palo…
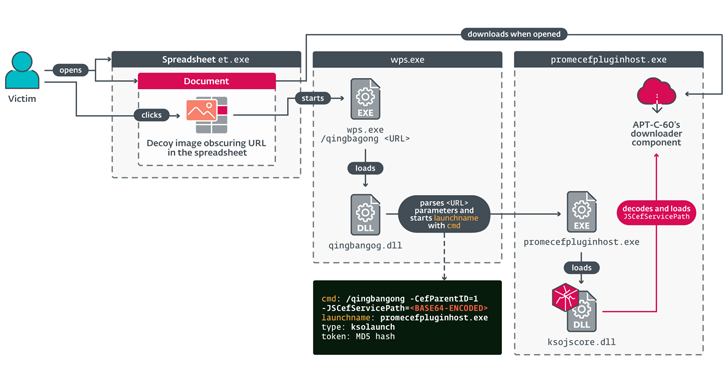
Read MoreAug 28, 2024Ravie LakshmananCyber Attack / Vulnerability A South Korea-aligned cyber espionage has been linked to the zero-day exploitation of a now-patched critical remote code execution flaw in Kingsoft WPS Office to deploy a bespoke backdoor dubbed SpyGlace. The activity has been attributed to a threat actor dubbed APT-C-60, according to cybersecurity firms ESET and…
Read More‘For every $1 spent on an Nvidia GPU chip there is an $8 to $10 multiplier across the tech sector,’ according to an August report by investment firm Wedbush. Blackwell delays. Hopper demand. And the state of the emerging artificial intelligence market. Nvidia’s earnings report Wednesday for the second quarter ended July 28 of its…
Read MoreVersa Networks Releases Advisory for a Vulnerability in Versa Director, CVE-2024-39717 | CISA
by nlqip
Versa Networks has released an advisory for a vulnerability (CVE-2024-39717) in Versa Director, a key component in managing SD-WAN networks, used by some Internet Service Providers (ISPs) and Managed Service Providers (MSPs). A cyber threat actor could exploit this vulnerability to take control of an affected system. CISA urges organizations to apply necessary updates, hunt…
Read MoreCISA and Partners Release Advisory on Iran-based Cyber Actors Enabling Ransomware Attacks on US Organizations | CISA
by nlqip
Today, CISA—in partnership with the Federal Bureau of Investigation (FBI) and the Department of Defense Cyber Crime Center (DC3)—released Iran-based Cyber Actors Enabling Ransomware Attacks on U.S. Organizations. This joint advisory warns of cyber actors, known in the private sector as Pioneer Kitten, UNC757, Parisite, Rubidium, and Lemon Sandstorm, targeting and exploiting U.S. and foreign…
Read MoreAA24-241A : Joint Cybersecurity Advisory on Iran-based Cyber Actors Targeting US Organizations
by nlqip
A joint Cybersecurity Advisory highlights Iran-based cyber actor ransomware activity targeting U.S. organizations. The advisory includes CVEs exploited, alongside techniques, tactics and procedures used by the threat actors. Background On August 28, the Cybersecurity and Infrastructure Security Agency (CISA) published a joint Cybersecurity advisory (CSA) in coordination with The Federal Bureau of Investigation (FBI) and…
Read MoreDSPM solutions provide a comprehensive, up-to-date view into cloud-based data and risk. An integrated CNAPP and DSPM solution elevates this analysis to expose toxic combinations and security gaps across cloud environments. As organizations ramp up their use of cloud-native applications, the amount of sensitive data stored in the cloud grows – as does the difficulty…
Read MoreBy ARC Labs contributor, Dylan Michalak, Threat Research Intern Sleep obfuscation is a term encompassing malware that waits for some time period to avoid detection. It could include extended sleeping, where malware will wait an extended time (10+ minutes) to start executing to evade shorter sandbox analysis. It could also encompass logic bombs, malicious code that is…
Read MoreSummary The Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Defense Cyber Crime Center (DC3) are releasing this joint Cybersecurity Advisory (CSA) to warn network defenders that, as of August 2024, a group of Iran-based cyber actors continues to exploit U.S. and foreign organizations. This includes organizations across…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’