The Seattle-Tacoma International Airport has confirmed that a cyberattack is likely behind the ongoing IT systems outage that disrupted reservation check-in systems and delayed flights over the weekend. SEA-TAC is Seattle’s primary international airport and the busiest in the Pacific Northwest region. In 2023, it served almost 51 million passengers. The airport is a major hub…
Read MoreCISA Finding: 90% of Initial Access to Critical Infrastructure Is Gained Via Identity Compromise. What Can You Do About It?
by nlqip
Conventional wisdom suggests the keys to protect critical infrastructure against cyberattacks are network segmentation and OT security. But continued breaches imply those methods alone fall short. In fact, a CISA probe of 121 critical infrastructure networks found that their weakest link is identity compromise. Learn how to leverage an attacker’s perspective to better secure critical…
Read More‘Bringing that kind of AI capability to that kind of enterprise environment – it’s really only something IBM can do,’ IBM VP Tina Tarquinio tells CRN. IBM unveiled its Telum II processor and Spyre accelerator chip during the annual Hot Chips conference, promising partners and solution providers new tools for bringing artificial intelligence use cases…
Read MoreAug 26, 2024The Hacker NewsData Security / Compliance Nowadays, sensitive and critical data is traveling in everyday business channels that offer only the basic level of security and encryption, and companies are often oblivious to the risk. A case in point: Disney suffered a devastating data leak by a hacktivist group known as NullBulge that…
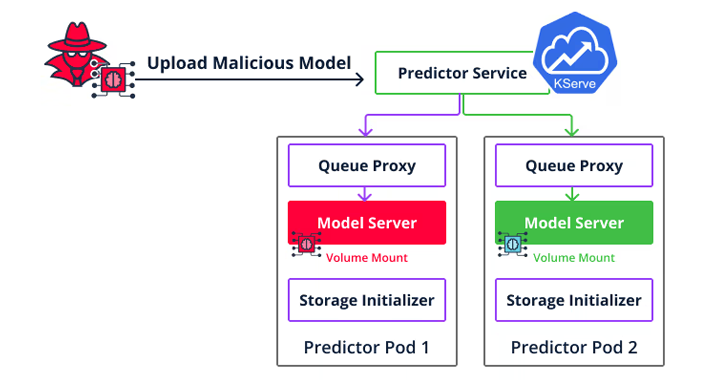
Read MoreCybersecurity researchers are warning about the security risks in the machine learning (ML) software supply chain following the discovery of more than 20 vulnerabilities that could be exploited to target MLOps platforms. These vulnerabilities, which are described as inherent- and implementation-based flaws, could have severe consequences, ranging from arbitrary code execution to loading malicious datasets.…
Read MoreUS Federal Court Rules Against Geofence Warrants This is a big deal. A US Appeals Court ruled that geofence warrants—these are general warrants demanding information about all people within a geographical boundary—are unconstitutional. The decision seems obvious to me, but you can’t take anything for granted. Tags: courts, data privacy, geolocation, laws Posted on August…
Read MoreDie richtigen Fragen im Bewerbungsgespräch können CISO-Kandidaten dabei unterstützen, besser abzuschätzen, was beim neuen Arbeitgeber auf sie zukommen könnte. Foto: N Universe | shutterstock.com Der Bewerbungsprozess ist nicht für Unternehmen eine Gelegenheit, den passenden Kandidaten zu finden. Auch die Job-Aspiranten sollten abwägen, ob die in Aussicht stehende Stelle beziehungsweise das dazugehörige Unternehmen wirklich zu ihnen…
Read More“The biggest issue they had [was] that they couldn’t pay their people, and it was like on a weekly or fortnightly basis. And if you’re not paying your drivers and stuff, that business stops, right?” says Haigh. “The person that was under the most stress was the CFO. [He] could see themselves going into a…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/the-hidden-risks-of-internet-of-bodies-iob-cybersecurity-in-healthcare-devices” on this server. Reference #18.dfd7ce17.1724666536.8852b1b https://errors.edgesuite.net/18.dfd7ce17.1724666536.8852b1b Source link lol
Read MoreAug 26, 2024Ravie LakshmananSoftware Security / Vulnerability Two security vulnerabilities have been disclosed in the open-source Traccar GPS tracking system that could be potentially exploited by unauthenticated attackers to achieve remote code execution under certain circumstances. Both the vulnerabilities are path traversal flaws and could be weaponized if guest registration is enabled, which is the…
Read MoreRecent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher