Aug 22, 2024Ravie LakshmananVulnerability / Network Security SolarWinds has issued patches to address a new security flaw in its Web Help Desk (WHD) software that could allow remote unauthenticated users to gain unauthorized access to susceptible instances. “The SolarWinds Web Help Desk (WHD) software is affected by a hardcoded credential vulnerability, allowing [a] remote unauthenticated…
Read MoreAug 22, 2024Ravie LakshmananHardware Security / Supply Chain Attack Cybersecurity researchers have uncovered a hardware backdoor within a particular model of MIFARE Classic contactless cards that could allow authentication with an unknown key and open hotel rooms and office doors. The attacks have been demonstrated against FM11RF08S, a new variant of MIFARE Classic that was…
Read MoreMicrosoft has confirmed and fixed a known issue causing performance issues, boot problems, and freezes on Windows Server 2019 systems after installing the August 2024 security updates. The company acknowledged the issue following widespread reports from Windows admins saying that servers on their environments were experiencing performance issues and massive lags, becoming unusable after installing…
Read MoreA new Android malware named NGate can steal money from payment cards by relaying to an attacker’s device the data read by the near-field communication (NFC) chip. Specifically, NGate enables attackers to emulate victims’ cards and make unauthorized payments or withdrawal cash from ATMs.. The campaign has been active since November 2023 and is linked to a recent…
Read MoreMicrosoft has confirmed the August 2024 Windows security updates are causing Linux booting issues on dual-boot systems with Secure Boot enabled. The issue is caused by a Secure Boot Advanced Targeting (SBAT) update applied to block Linux boot loaders unpatched against the CVE-2022-2601 GRUB2 Secure Boot bypass vulnerability. “Resulting from this issue, your device might fail…
Read MoreAug 22, 2024Ravie LakshmananNetwork Security / Zero-Day Details have emerged about a China-nexus threat group’s exploitation of a recently disclosed, now-patched security flaw in Cisco switches as a zero-day to seize control of the appliance and evade detection. The activity, attributed to Velvet Ant, was observed early this year and involved the weaponization of CVE-2024-20399…
Read MoreThe evolving threat environment and growing regulatory pressures are prompting more organizations to begin measuring their cyber risk from a financial perspective, according to Optiv’s James Turgal. Amid a convergence of factors including the intensification of both cyberthreats and regulatory pressures, more organizations are focusing on quantifying their cyber risk from a financial perspective, executives…
Read MoreCEO Sridhar Ramaswamy dives into Cortex AI and Iceberg customer momentum, the impact of Snowflake’s recent cyberattack and how AI will ‘c ontribute materially to revenue’ in 2025 . CEO Sridhar Ramaswamy was bullish about his company’s AI future during Snowflake’s Q2 earnings report on Wednesday, while also downplaying his company’s recent cyberattack and unveiling…
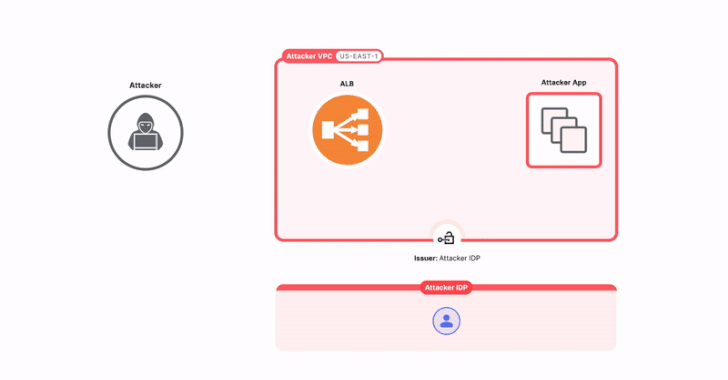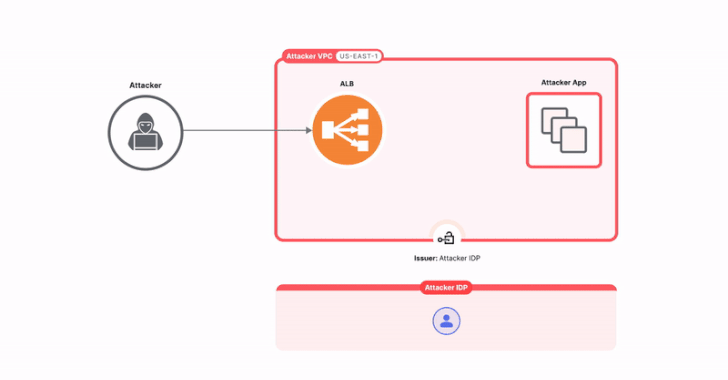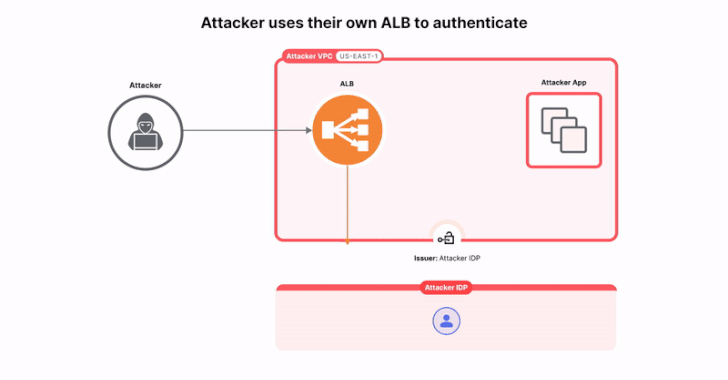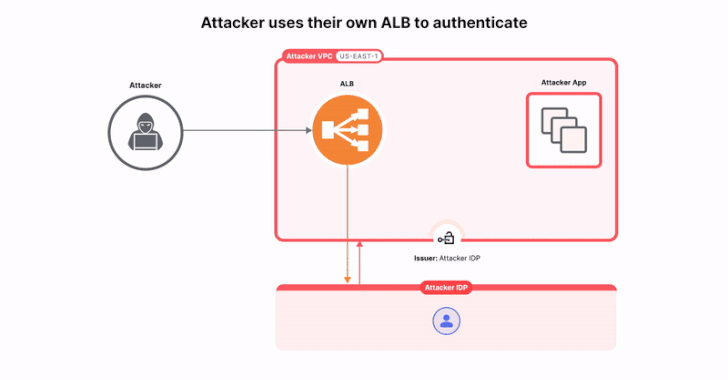
Read MoreAug 22, 2024Ravie LakshmananCloud Security / Application Security As many as 15,000 applications using Amazon Web Services’ (AWS) Application Load Balancer (ALB) for authentication are potentially susceptible to a configuration-based issue that could expose them to sidestep access controls and compromise applications. That’s according to findings from Israeli cybersecurity company Miggo, which dubbed the problem…
Read MoreToday, Google released a new Chrome emergency security update to patch a zero-day vulnerability tagged as exploited in attacks. “Google is aware that an exploit for CVE-2024-7971 exists in the wild,” the company said in an advisory published on Wednesday. This high-severity zero-day vulnerability is caused by a type confusion weakness in Chrome’s V8 JavaScript…
Read MoreRecent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher