IT admins usually know what to watch out for when end users are creating weak, easy-to-guess passwords. However, a common yet overlooked type of weak password are keyboard walk patterns. A keyboard walk password typically refers to a password created by moving sequentially over the keyboard keys in a pattern that resembles walking. These are…
Read MoreImage: MidjourneyCISA warned on Thursday that attackers are exploiting a recently patched critical vulnerability in SolarWinds’ Web Help Desk solution for customer support. Web Help Desk (WHD) is IT help desk software widely used by large corporations, government agencies, and healthcare and education organizations worldwide to centralize, automate, and streamline help desk management tasks. Tracked…
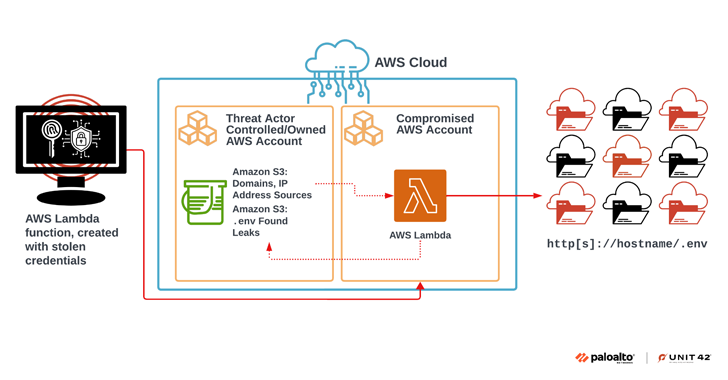
Read MoreAug 16, 2024Ravie LakshmananCloud Security / Application Security A large-scale extortion campaign has compromised various organizations by taking advantage of publicly accessible environment variable files (.env) that contain credentials associated with cloud and social media applications. “Multiple security missteps were present in the course of this campaign, including the following: Exposing environment variables, using long-lived…
Read MoreCisco CEO Chuck Robbins cited ‘several $100 million-plus transactions in the quarter.’ Deep cuts at Cisco Systems appear aimed at readying the 40-year-old networking giant for increased customer demand to modernize technology for improved security and artificial intelligence growth – areas where Cisco partners can see business gains in the new fiscal year. These are…
Read More‘You need to strengthen your client relationships, your team collaboration and your service consistency. That’s going to increase your efficiency, your operational maturity and, ultimately, your sales, your revenue and your profitability,’ says Ray Mann, channel development manager at ScalePad. Ray Mann, channel development manager at ScalePad, told an audience of MSPs at XChange August…
Read More‘There is a certain amount of cloud repatriation that is happening, and that’s happening purely from a cost perspective,’ Cognizant’s Naveen Sharma tells CRN in an interview. Naveen Sharma compares the classic public cloud vendor business model to buying wine. The seller loves for a customer to try a glass, and then maybe drink another,…
Read More‘The pace of change is relentless,’ says Pax8 CEO Scott Chasin. ‘We’re on the cusp of AI reaching human-level intelligence and beyond.’ AI tools are evolving at a rapid pace, with new capabilities coming out every four to six months, and will completely change how IT businesses operate over the next 10 years. “The genie…
Read MoreScanSource has acquired long-time mobility partner Advantix and is using it as the base for its new Integrated Solutions and Services Group to expand mobility technology and management capabilities to its solution provider partners. ScanSource, which distributes specialty technology and modern cloud and communications services, is looking to expand its technology management and wireless connectivity…
Read MoreAug 16, 2024Ravie LakshmananDark Web / Data Breach A 27-year-old Russian national has been sentenced to over three years in prison for peddling financial information, login credentials, and other personally identifying information (PII) on a now-defunct dark web marketplace called Slilpp. Georgy Kavzharadze, 27, of Moscow, Russia, pleaded guilty to one count of conspiracy to…
Read MoreAug 16, 2024Ravie LakshmananMalware / Data Theft Cybersecurity researchers have shed light on a sophisticated information stealer campaign that impersonates legitimate brands to distribute malware like DanaBot and StealC. The activity cluster, orchestrated by Russian-speaking cybercriminals and collectively codenamed Tusk, is said to encompass several sub-campaigns, leveraging the reputation of the platforms to trick users…
Read MoreRecent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher