

Despite losing its North America channel chief for a second year in a row, AMD says its commitment to the channel has ‘only strengthened’ as the chip designer bets its next phase of growth on the promise of AI to compete with Intel, Nvidia and others. AMD said its commitment to the channel has “only…
Read MoreMicrosoft has confirmed that July’s security updates break remote desktop connections in organizations where Windows servers are configured to use the legacy RPC over HTTP protocol in the Remote Desktop Gateway. “Windows Servers might affect Remote Desktop Connectivity across an organization if legacy protocol (Remote Procedure Call over HTTP) is used in Remote Desktop Gateway.…
Read MoreOperational expenses and loss to business would differ greatly from organization to organization, and segment to segment. Parametrix, using its service monitoring sensors, estimated healthcare suffering the most at $1.94 billion in direct losses from the incident, with banking and transportation closely behind at $1.15 billion and $0.86 billion, respectively. It estimated the loss per…
Read MoreImage: MidjourneyAcronis warned customers to patch a critical Cyber Infrastructure security flaw that lets attackers bypass authentication on vulnerable servers using default credentials. Acronis Cyber Protect (ACI) is a unified multi-tenant platform that combines remote endpoint management, backup, and virtualization capabilities and helps run disaster recovery workloads and store enterprise backup data securely. Over 20,000 service providers use…
Read MoreCompromising the Secure Boot Process This isn’t good: On Thursday, researchers from security firm Binarly revealed that Secure Boot is completely compromised on more than 200 device models sold by Acer, Dell, Gigabyte, Intel, and Supermicro. The cause: a cryptographic key underpinning Secure Boot on those models that was compromised in 2022. In a public…
Read MoreFrom the editors of our sister publication Computerworld, this enterprise buyer’s guide helps IT staff understand what the various unified endpoint management (UEM) platforms can do for their organizations and how to choose the right solution. Source link lol
Read MoreRussian-speaking threat actors accounted for at least 69% of all crypto proceeds linked to ransomware throughout the previous year, exceeding $500,000,000. This number is from TRM Labs, a blockchain intelligence and analytics firm specializing in crypto-assisted money laundering and financial crime. North Korea is the leader in stealing cryptocurrency through exploits and breaches, having stolen over…
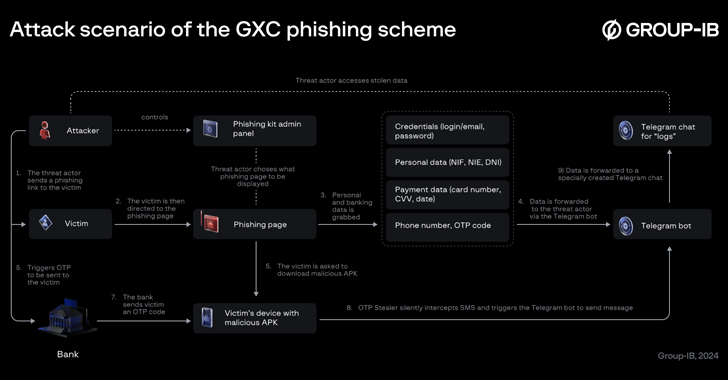
Read MoreA Spanish-speaking cybercrime group named GXC Team has been observed bundling phishing kits with malicious Android applications, taking malware-as-a-service (MaaS) offerings to the next level. Singaporean cybersecurity company Group-IB, which has been tracking the e-crime actor since January 2023, described the crimeware solution as a “sophisticated AI-powered phishing-as-a-service platform” capable of targeting users of more…
Read MoreServiceNow, which has been building out its GenAI-powered search capabilities for years, has acquired Raytion which the company said will give it the ability to search across all of a company’s enterprise knowledge systems including ServiceNow, Salesforce, and Atlassian. ServiceNow Wednesday unveiled the acquisition of Raytion as a way to expand its Now platform’s GenAI-powered…
Read MoreCybersecurity Snapshot: North Korea’s Cyber Spies Hunt for Nuclear Secrets, as Online Criminals Ramp Up AI Use in the EU
by nlqip
Check out a CISA-FBI advisory about North Korean cyber espionage on critical infrastructure orgs. Plus, what Europol found about the use of AI for cybercrime. Meanwhile, the risk concerns that healthcare leaders have about generative AI. And a poll on water plant cybersecurity. And much more! Dive into six things that are top of mind…
Read MoreRecent Posts
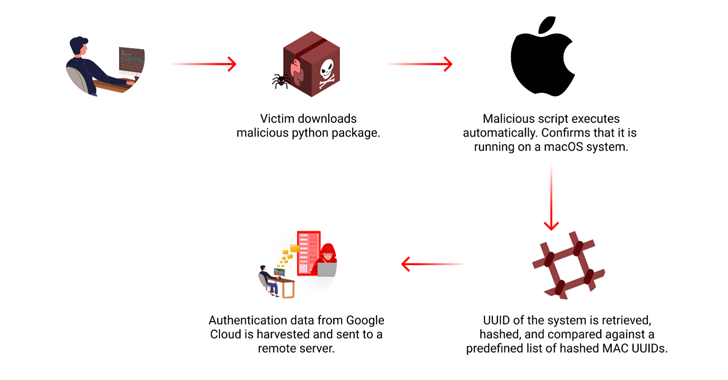
- Malicious PyPI Package Targets macOS to Steal Google Cloud Credentials
- Secure Boot no more? Leaked key, faulty practices put 900 PC/server models in jeopardy
- Crooks Bypassed Google’s Email Verification to Create Workspace Accounts, Access 3rd-Party Services – Krebs on Security
- Friday Squid Blogging: Sunscreen from Squid Pigments
- Here Are The 8 Biggest IT Services M&A Deals In Q2 2024