Cisco CEO Chuck Robbins says his team is “shifting hundreds of millions of dollars into AI,” including AI networking for cloud, AI infrastructure, silicon and cybersecurity. Cisco Systems crossed $1 billion to date in AI orders with webscale customers and predicts another $1 billion in AI product orders this fiscal year. On the San Jose,…
Read MoreAug 15, 2024Ravie LakshmananRansomware / Cybercrime A cybercrime group with links to the RansomHub ransomware has been observed using a new tool designed to terminate endpoint detection and response (EDR) software on compromised hosts, joining the likes of other similar programs like AuKill (aka AvNeutralizer) and Terminator. The EDR-killing utility has been dubbed EDRKillShifter by…
Read MoreAug 15, 2024The Hacker NewsIdentity Security / Threat Detection The Emergence of Identity Threat Detection and Response Identity Threat Detection and Response (ITDR) has emerged as a critical component to effectively detect and respond to identity-based attacks. Threat actors have shown their ability to compromise the identity infrastructure and move laterally into IaaS, Saas, PaaS…
Read MoreAs Rodgers puts it, “What got you here won’t get you there. You know how to configure a firewall, but now you have to communicate to executives. You have to know the business and be able to talk about your technology, your security, the solution through the language of the business. Being able to have…
Read MoreAug 15, 2024Ravie LakshmananCyber Espionage / Data Theft A previously unknown threat actor has been attributed to a spate of attacks targeting Azerbaijan and Israel with an aim to steal sensitive data. The attack campaign, detected by NSFOCUS on July 1, 2024, leveraged spear-phishing emails to single out Azerbaijani and Israeli diplomats. The activity is…
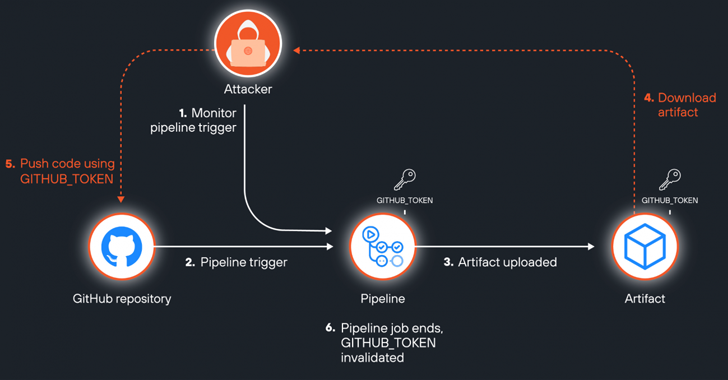
Read MoreAug 15, 2024Ravie LakshmananCloud Security / DevOps A newly discovered attack vector in GitHub Actions artifacts dubbed ArtiPACKED could be exploited to take over repositories and gain access to organizations’ cloud environments. “A combination of misconfigurations and security flaws can make artifacts leak tokens, both of third party cloud services and GitHub tokens, making them…
Read MoreAug 15, 2024Ravie LakshmananNetwork Security / Cybercrime Cybersecurity researchers have discovered a new variant of the Gafgyt botnet that’s targeting machines with weak SSH passwords to ultimately mine cryptocurrency on compromised instances using their GPU computational power. This indicates that the “IoT botnet is targeting more robust servers running on cloud native environments,” Aqua Security…
Read MoreGeorgy Kavzharadze, a 27-year-old Russian national, has been sentenced to 40 months in prison for selling login credentials for over 300,000 accounts on Slilpp, the largest online marketplace of stolen logins, until its seizure in June 2021. In a Wednesday press release, the U.S. Department of Justice said that Kavzharadze (also known as TeRorPP, Torqovec,…
Read MoreMicrosoft warned customers this Tuesday to patch a critical TCP/IP remote code execution (RCE) vulnerability with an increased likelihood of exploitation that impacts all Windows systems using IPv6, which is enabled by default. Tracked as CVE-2024-38063, this security bug is caused by an Integer Underflow weakness, which attackers could exploit to trigger buffer overflows that…
Read MoreCisco will spend between $700 million and $800 million in the first quarter of its 2025 fiscal year. Cisco Systems confirmed massive layoffs Wednesday with plans to cut about 7 percent of its global workforce, which should cost up to $1 billion. The San Jose, Calif.-based networking giant said in a regulatory filing that the…
Read MoreRecent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher