Scams Your phone number is more than just a way to contact you – scammers can use it to target you with malicious messages and even exploit it to gain access to your bank account or steal corporate data 13 Aug 2024 • , 5 min. read Last month, we looked at how scammers can…
Read MoreTwo critical vulnerabilities Of the two critical vulnerabilities addressed in the patch day, the more severe is an authentication bypass flaw (CVE-2024-41730) with a CVSS score of 9.8/10 affecting SAP’s BusinessObjects business intelligence platform, while the other is a server-side request forgery (SSRF) vulnerability in applications built with SAP Build Apps. CVE-2024-41730, as described by…
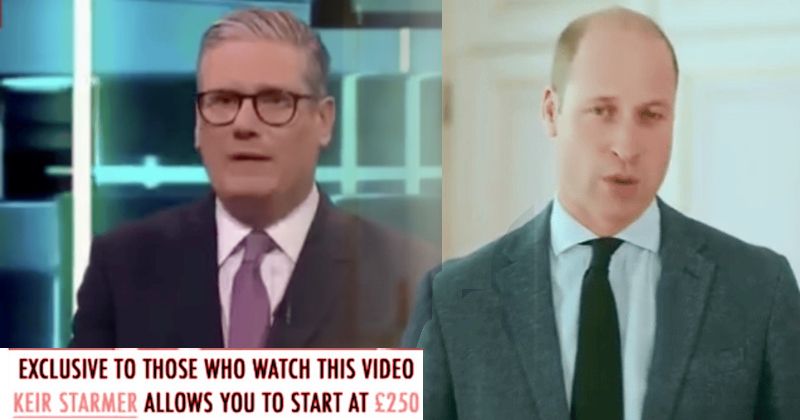
Read MoreScammers are once again using deepfake technology to dupe unwary internet Facebook and Instagram users into making unwise cryptocurrency investments. AI-generated videos promoting fraudulent cryptocurrency trading platform Immediate Edge have used deepfake footage of British Prime Minister Sir Keir Starmer and His Royal Highness Prince William to reach an estimated 890,000 people via Meta’s social…
Read MoreIvanti released a patch for a critical severity authentication bypass vulnerability and a warning that exploit code is publicly available Background On August 13, Ivanti released a security advisory to address a critical severity authentication bypass vulnerability in its Virtual Traffic Manager (vTM) product, a software-based application delivery controller (ADC). CVE Description CVSSv3 CVE-2024-7593 Ivanti…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. Welcome to the world of Linux! This blog will take you on a step-by-step journey on how to get familiar with Linux if…
Read MoreMonitoring evolving DDoS trends is essential for anticipating threats and adapting defensive strategies. The comprehensive Gcore Radar Report for the first half of 2024 provides detailed insights into DDoS attack data, showcasing changes in attack patterns and the broader landscape of cyber threats. Here, we share a selection of findings from the full report. Key…
Read MoreAug 14, 2024Ravie LakshmananThreat Intelligence / Cyber Attack The China-backed threat actor known as Earth Baku has diversified its targeting footprint beyond the Indo-Pacific region to include Europe, the Middle East, and Africa starting in late 2022. Newly targeted countries as part of the activity include Italy, Germany, the U.A.E., and Qatar, with suspected attacks…
Read MoreSimultaneously, organizations must adopt a more discerning approach to cybersecurity investment, recognizing that true security is not a commodity that can be purchased off the shelf. Leaders should prioritize allocating resources toward building robust internal capabilities, including skilled security teams, comprehensive security policies, and the implementation of continuous monitoring and improvement practices. By doing so,…
Read MoreAug 14, 2024Ravie LakshmananVulnerability / Network Security Ivanti has rolled out security updates for a critical flaw in Virtual Traffic Manager (vTM) that could be exploited to achieve an authentication bypass and create rogue administrative users. The vulnerability, tracked as CVE-2024-7593, has a CVSS score of 9.8 out of a maximum of 10.0. “Incorrect implementation…
Read MoreAug 14, 2024Ravie LakshmananWindows Security / Vulnerability Microsoft on Tuesday shipped fixes to address a total of 90 security flaws, including 10 zero-days, of which six have come under active exploitation in the wild. Of the 90 bugs, seven are rated Critical, 79 are rated Important, and one is rated Moderate in severity. This is…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’