Access Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/why-dcap-is-essential-for-modern-data-security-a-closer-look” on this server. Reference #18.ef7dead.1723457074.785a211 https://errors.edgesuite.net/18.ef7dead.1723457074.785a211 Source link lol
Read MoreA notorious ransomware group has demanded more than half a billion dollars from victims in less than two years. That staggering statistic has been made public in an update to a joint advisory issued by the US Cybersecurity and Infrastructure Agency (CISA) and the FBI, warning organisations about the threat posed by the BlackSuit gang.…
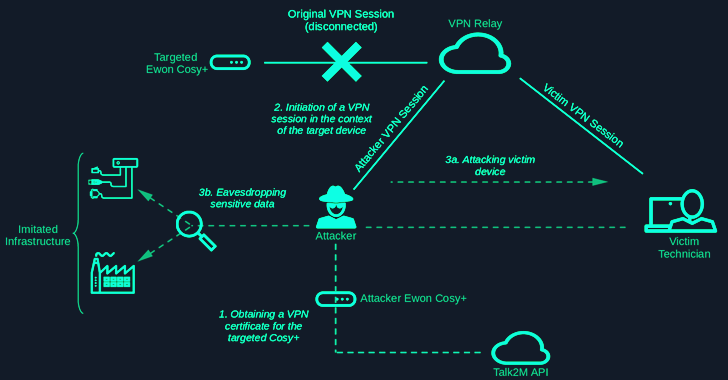
Read MoreAug 12, 2024Ravie LakshmananOperational Technology / Network Security Security vulnerabilities have been disclosed in the industrial remote access solution Ewon Cosy+ that could be abused to gain root privileges to the devices and stage follow-on attacks. The elevated access could then be weaponized to decrypt encrypted firmware files and encrypted data such as passwords in…
Read MoreBooker, a former CISO at UnitedHealth Group, says the attack also serves as a blaring reminder to healthcare organizations to “make sure you focus on the basics and essential security measures, like multifactor authentication, have them where you need them, which is everywhere, and have a way to know that what you’re doing is right,…
Read MoreAug 12, 2024Ravie LakshmananCloud Security / Malware The Russian government and IT organizations are the target of a new campaign that delivers a number of backdoors and trojans as part of a spear-phishing campaign codenamed EastWind. The attack chains are characterized by the use of RAR archive attachments containing a Windows shortcut (LNK) file that,…
Read MoreAlmost 2.7 billion records of personal information for people in the United States were leaked on a hacking forum, exposing names, social security numbers, all known physical addresses, and possible aliases. The data allegedly comes from National Public Data, a company that collects and sells access to personal data for use in background checks, to obtain criminal records,…
Read MoreX has always had a bot problem, but now scammers are utilizing the Ukraine war and earthquake warnings in Japan to entice users into clicking on fake content warnings and videos that lead to scam adult sites, malicious browser extensions, and shady affiliate sites. For months, X has been flooded with posts that contain what…
Read MoreA series of targeted cyberattacks that started at the end of July 2024, targeting dozens of systems used in Russian government organizations and IT companies, are linked to Chinese hackers of the APT31 and APT 27 groups. Kaspersky, who discovered the activity, dubbed the campaign “EastWind,” reporting that it employs an updated version of the…
Read MoreFor the 39th year, solution providers scored vendors across 27 technology categories based on their performance in product innovation, support, partnership, and managed and cloud services. Here’s a roundup of the companies with the highest overall scores. Making The Grade For the 39th year, CRN offered solution providers in North America the opportunity to grade…
Read MoreAug 11, 2024Ravie LakshmananSupply Chain / Software Security Cybersecurity researchers have discovered a new malicious package on the Python Package Index (PyPI) repository that masquerades as a library from the Solana blockchain platform but is actually designed to steal victims’ secrets. “The legitimate Solana Python API project is known as ‘solana-py’ on GitHub, but simply…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’