An ongoing and widespread malware campaign force-installed malicious Google Chrome and Microsoft Edge browser extensions in over 300,000 browsers, modifying the browser’s executables to hijack homepages and steal browsing history. The installer and extensions, which are usually undetected by antivirus tools, are designed to steal data and execute commands on infected devices. ReasonLabs researchers identified the campaign…
Read More‘Together with Acqueon, we can intelligently combine the preferences of the customer with the increasing variety of outreach channels to help enterprises grow their revenue and delight customers, while aligning to compliance standards,’ says Five9 CEO Mike Burkland. Contact center specialist Five9 plans to acquire revenue generation platform provider Acqueon in a move to boost…
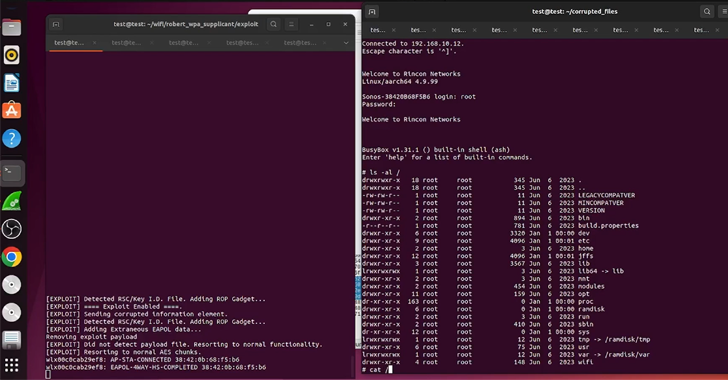
Read MoreAug 09, 2024Ravie LakshmananIoT Security / Wireless Security Cybersecurity researchers have uncovered weaknesses in Sonos smart speakers that could be exploited by malicious actors to clandestinely eavesdrop on users. The vulnerabilities “led to an entire break in the security of Sonos’s secure boot process across a wide range of devices and remotely being able to…
Read MoreThe cybersecurity vendor is reportedly mulling a buyout deal by investors. Trend Micro is reportedly exploring an acquisition deal by potential buyers including private equity investors. CRN has reached out to Trend Micro for comment. [Related: 10 Security Vendors Making Moves At Black Hat 2024] According to a Reuters report Thursday, Trend Micro is considering…
Read MorePeople-Search Site Removal Services Largely Ineffective Consumer Reports has a new study of people-search site removal services, concluding that they don’t really work: As a whole, people-search removal services are largely ineffective. Private information about each participant on the people-search sites decreased after using the people-search removal services. And, not surprisingly, the removal services did…
Read MoreCybersecurity Snapshot: New Report Ranks Top Cloud Threats, while Guide Helps Assess Whether SW Products Are Built Securely
by nlqip
The Cloud Security Alliance has released its list of top cloud threats for 2024. Plus, CISA and the FBI published a guide for determining if a software product was built “secure by design.” Meanwhile, find out how AI can transform offensive security. And the latest on the Royal ransomware gang, the CIS Benchmarks and TikTok’s…
Read MoreCritical vulnerability in Cisco Smart Software Manager On-Prem exposes systems to unauthorized password changes, exploit code now available. Background On July 17, 2024, Cisco published an advisory for a for a critical vulnerability in Cisco’s Smart Software Manager On-Prem (SSM On-Prem): CVE Description CVSSv3 CVE-2024-20419 Cisco Smart Software Manager On-Prem Password Change Vulnerability 10 Analysis…
Read MoreWhat it does: FAIR provides a model for understanding, analyzing, and quantifying cyber risk and operational risk in financial terms, according to the Fair Institute. It’s unlike risk assessment frameworks that focus their output on qualitative color charts or numerical weighted scales. Instead it builds a foundation for developing a robust approach to information risk…
Read MoreAction1’s expertise in patch management aligns well with CrowdStrike’s current need to enhance its update mechanisms. By integrating Action1’s technology into its platform, CrowdStrike could significantly improve the testing and deployment of updates, something it faced widespread criticism for in the months following the Falcon goof-up. Implications for customers The $1 billion valuation is a…
Read MoreAug 09, 2024Ravie LakshmananNational Security / Identity Theft The U.S. Department of Justice (DoJ) on Thursday charged a 38-year-old individual from Nashville, Tennessee, for allegedly running a “laptop farm” to help get North Koreans remote jobs with American and British companies. Matthew Isaac Knoot is charged with conspiracy to cause damage to protected computers, conspiracy…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’