Register today for mWISE™, the unique cybersecurity conference from Mandiant, now part of Google Cloud. Built by practitioners for practitioners, mWISE runs from September 18 – 19, 2024 in Denver, Colorado. There are just a few days left to get $300 off the standard conference price at mWISE—and the conference itself is just six weeks…
Read MoreHere are the top 25 companies on this year’s CRN Fast Growth 150 list, which ranks solution providers with gross annual sales of at least $1 million by their two-year growth rate. Overachievers These are challenging times for solution providers as they navigate both ongoing economic uncertainty and a rapidly changing technology landscape as artificial…
Read MoreOverall, this year’s Fast Growth 150 recorded an average two-year growth rate of 135 percent. That’s down a bit from the 145 percent average for the 2023 Fast Growth 150 class, but up from the 93 percent growth recorded by the 2022 Fast Growth 150. These are challenging times for solution providers as they navigate…
Read MoreThe cybersecurity vendor says Delta did not accept offers of help amid the multi-day outage that impacted the airline. CrowdStrike is contending that Delta did not accept offers of help amid the multi-day outage that impacted the airline, following the cybersecurity vendor’s defective July 19 update. In a letter sent to an attorney who is…
Read MoreAug 05, 2024Ravie LakshmananNetwork Security / Threat Intelligence Organizations in Kazakhstan are the target of a threat activity cluster dubbed Bloody Wolf that delivers a commodity malware called STRRAT (aka Strigoi Master). “The program selling for as little as $80 on underground resources allows the adversaries to take control of corporate computers and hijack restricted…
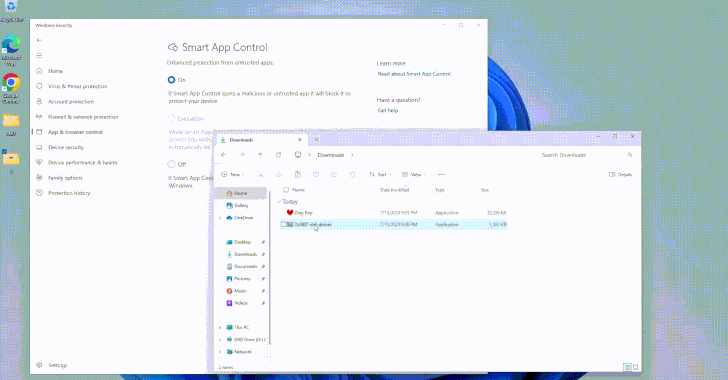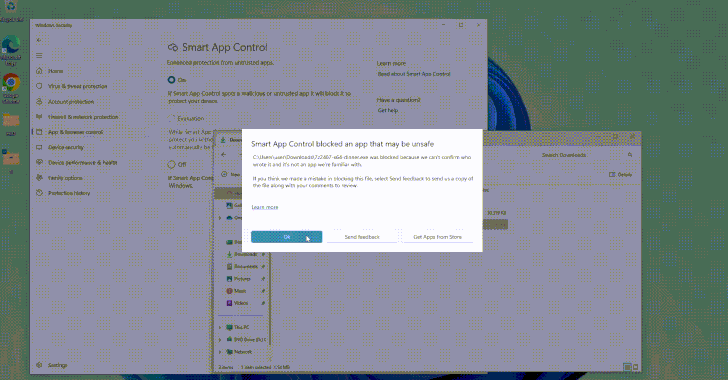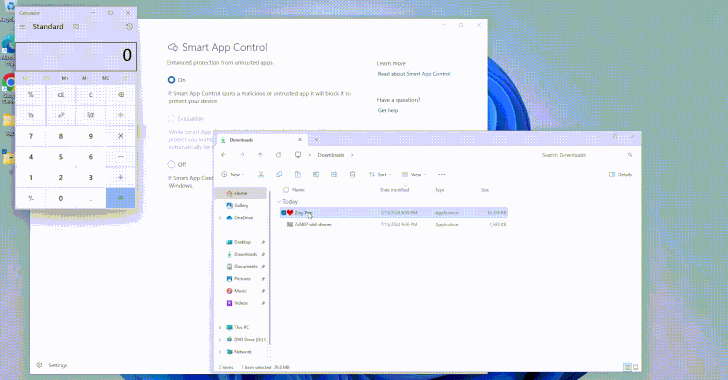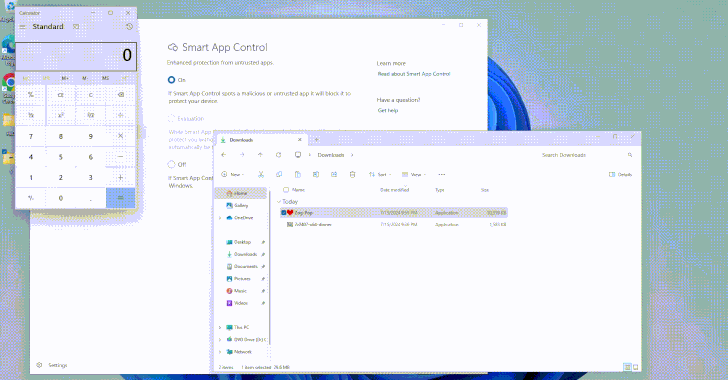
Read MoreAug 05, 2024Ravie LakshmananThreat Intelligence / Vulnerability Cybersecurity researchers have uncovered design weaknesses in Microsoft’s Windows Smart App Control and SmartScreen that could enable threat actors to gain initial access to target environments without raising any warnings. Smart App Control (SAC) is a cloud-powered security feature introduced by Microsoft in Windows 11 to block malicious,…
Read MoreBy employing a timing side channel while exploiting the heap vulnerabilities, which essentially allow attackers to manipulate the kernel’s memory allocation process, the researchers were able to pinpoint the exact moment of memory allocation and de-allocation, making the determination of frequently used caches extremely accurate. These caches are then shown to be reallocated to allow…
Read MoreAt Tenable, our mission is to manage and reduce cyber risk, because cyber risk is business risk. Feedback from dozens of top CISOs is reflected in our latest brand evolution. Tenable is the exposure management company that helps customers know where their weaknesses lie, expose their risk and close the gaps. Welcome to Tenable. Your…
Read MoreTenable Unveils Industry Leading Vulnerability Intelligence Data and Response Capabilities to Expose and Close Priority Threats that Drive Up Risk
by nlqip
Tenable®, the exposure management company, today announced the release of Vulnerability Intelligence and Exposure Response, two powerful context-driven prioritization and response features available in Tenable Vulnerability Management, Tenable One and Tenable Cloud Security. The combined power of these features contextualizes vulnerability data from internal and external sources, enabling organizations to close the exposures that pose…
Read MoreThis “agreement with Google … will allow us to accelerate our progress,” Character.AI said in a blog post. In a deal that might remind some of Microsoft’s March hiring of Inflection CEO and DeepMind co-founder Mustafa Suleyman, Google will hire the co-founders and members of the research team for Character.AI in exchange for an undisclosed…
Read MoreRecent Posts
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher