‘What’s really special about this is the opportunity to work with some really great people,’ says Tim Conkle, CEO of The 20 MSP. ‘If I’ve learned anything in my career, it’s that getting smart and [having] driven people together in the same room is a recipe for magic.’ The 20 MSP has made its ninth…
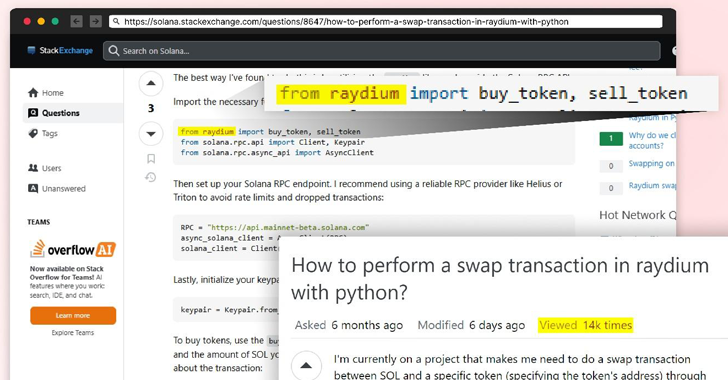
Read MoreIn yet another sign that threat actors are always looking out for new ways to trick users into downloading malware, it has come to light that the question-and-answer (Q&A) platform known as Stack Exchange has been abused to direct unsuspecting developers to bogus Python packages capable of draining their cryptocurrency wallets. “Upon installation, this code…
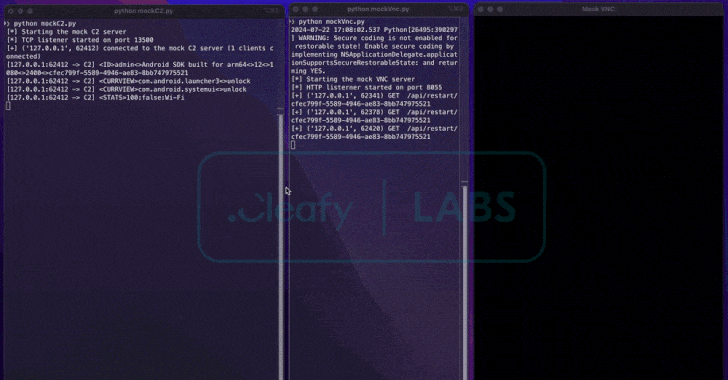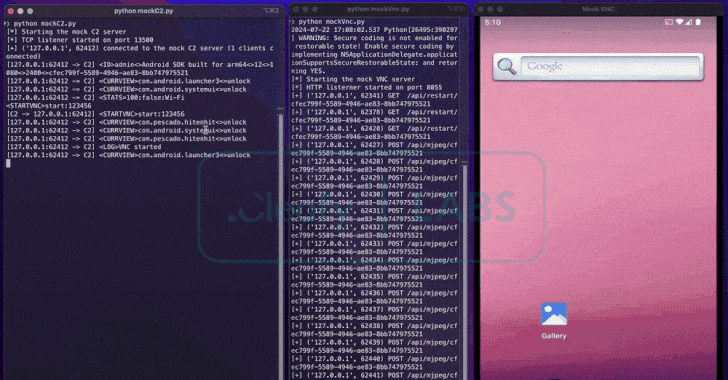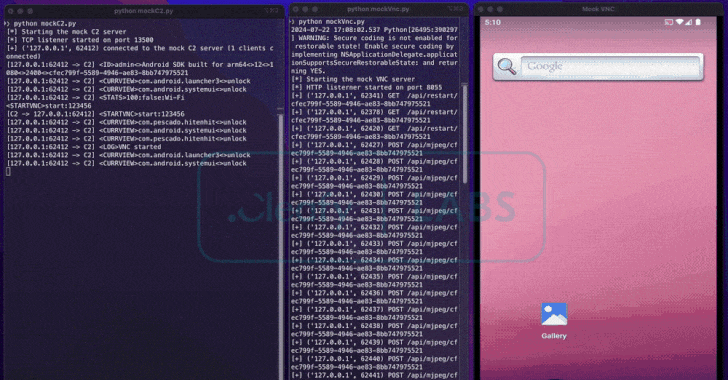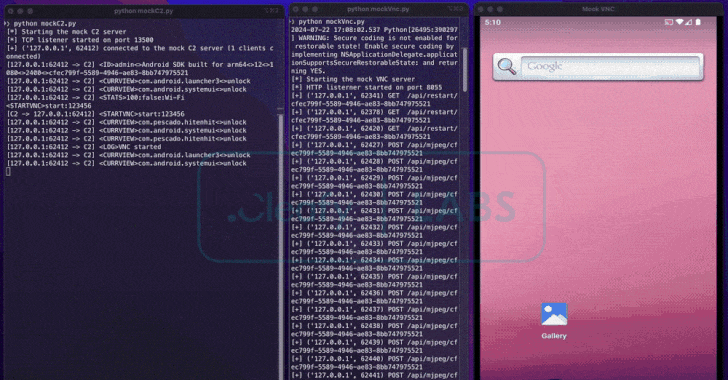
Read MoreAug 01, 2024Ravie LakshmananBanking Trojan / Cyber Fraud Cybersecurity researchers have uncovered a new Android remote access trojan (RAT) called BingoMod that not only performs fraudulent money transfers from the compromised devices but also wipes them in an attempt to erase traces of the malware. Italian cybersecurity firm Cleafy, which discovered the RAT towards the…
Read More‘Cautious customer behavior once again elongated sales cycles, then drove prioritization of needs over wants and cost savings over expansion. Capital investment in complex solutions, particularly those tied to data center and network modernization, continued to be downsized or put on hold. And there was growing refresh activity in client devices,’ says CDW Chair and…
Read More“Through thorough investigation and leveraging sensitive sources, CloudSEK has confirmed that the ransomware group responsible for this attack is RansomEXX,” CloudSEK said. “Our extensive engagement with the affected banking sector in India facilitated this determination.” The AI-powered, threat intelligence firm said the attack happened through a misconfigured Jenkins server, an open-source automation tool for developers…
Read MoreHow to detect and prevent attackers from using these various techniques Obfuscation is an important technique for protecting software that also carries risks, especially when used by malware authors. In this article, we examine obfuscation, its effects, and responses to it. What Is Obfuscation? Obfuscation is the technique of intentionally making information difficult to read,…
Read MoreEducation in Secure Software Development The Linux Foundation and OpenSSF released a report on the state of education in secure software development. …many developers lack the essential knowledge and skills to effectively implement secure software development. Survey findings outlined in the report show nearly one-third of all professionals directly involved in development and deployment …
Read MoreAug 01, 2024Ravie LakshmananData Encryption / Browser Security Google has announced that it’s adding a new layer of protection to its Chrome browser through what’s called app-bound encryption to prevent information-stealing malware from grabbing cookies on Windows systems. “On Windows, Chrome uses the Data Protection API (DPAPI) which protects the data at rest from other…
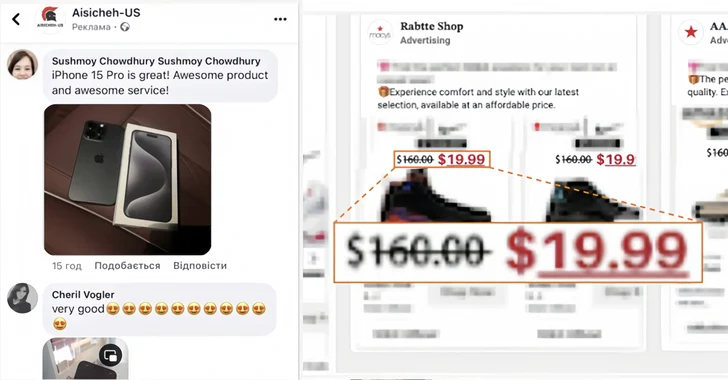
Read MoreAug 01, 2024Ravie LakshmananOnline Fraud / Malvertising Facebook users are the target of a scam e-commerce network that uses hundreds of fake websites to steal personal and financial data using brand impersonation and malvertising tricks. Recorded Future’s Payment Fraud Intelligence team, which detected the campaign on April 17, 2024, has given it the name ERIAKOS…
Read More4. Test your incident response plans thoroughly Organizations must have designated people and formal processes in place to determine the “material impact” of an incident and to communicate with relevant authorities by the stipulated deadlines. Testing and preparedness of incident response plans will be crucial. Sometimes when groups are brought together from a diverse set…
Read MoreRecent Posts
- Everything That You Need to Know About the Dark Web and Cybercrime | BlackFog
- Security plugin flaw in millions of WordPress sites gives admin access
- Phishing emails increasingly use SVG attachments to evade detection
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches