The Internet Systems Consortium (ISC) released security advisories to address vulnerabilities affecting multiple versions of ISC’s Berkeley Internet Name Domain (BIND) 9. A cyber threat actor could exploit one of these vulnerabilities to cause a denial-of-service condition. CISA encourages users and administrators to review the following advisories and apply the necessary updates: CVE-2024-4076: Assertion failure…
Read MoreRobot Dog Internet Jammer Supposedly the DHS has these: The robot, called “NEO,” is a modified version of the “Quadruped Unmanned Ground Vehicle” (Q-UGV) sold to law enforcement by a company called Ghost Robotics. Benjamine Huffman, the director of DHS’s Federal Law Enforcement Training Centers (FLETC), told police at the 2024 Border Security Expo in…
Read MoreThe CrowdStrike-Microsoft Outage Is Likely To Curtail Auto-Updates. That May Not Be A Good Thing.
by nlqip
If customers opt to forgo automatic security updates going forward to ensure greater testing, the ‘whole IT environment is exposed’ during that testing period, a CrowdStrike partner tells CRN. The massively disruptive CrowdStrike-Microsoft outage will undoubtedly lead more customers to forgo automatic updates to reduce the chances of a similar event occurring again. But this…
Read MoreRegister today for mWISE™, the unique cybersecurity conference from Mandiant, now part of Google Cloud. Built by practitioners for practitioners, mWISE runs from September 18 – 19, 2024 in Denver, Colorado. Now that the mWISE session catalog is out, it’s time to take a closer look at the topics. Organizers have posted the session catalog,…
Read MoreCrowdStrike released a Preliminary Post Incident Review (PIR) on the faulty Falcon update explaining that a bug allowed bad data to pass its Content Validator and cause millions of Windows systems to crash on July 19, 2024. The cybersecurity company explained that the issue was caused by a problematic content configuration update meant to gather…
Read MoreThe HashiCorp acquisition, GenAI and Red Hat taking on VMware are likely to come up. Updates on the HashiCorp acquisition. Details on IBM’s approach to the artificial intelligence gold rush. And IBM subsidiary Red Hat taking on VMware and legacy virtualization vendors. These are just some of the topics analysts will likely bring up Wednesday…
Read MoreA bug in CrowdStrike’s content approval system ‘passed validation despite containing problematic content data,’ leading to the outage that caused global disruptions. A bug in CrowdStrike’s validation process for security configuration updates resulted in the Microsoft Windows outage that led to global disruptions starting Friday, the company said Wednesday. The widely felt snafu involved what…
Read MoreOnce the HTA script, a Windows standalone program written in HTML is executed, it initiates PowerShell code that eventually establishes C2, downloads decoy PDF files for evasion, and a malicious shell injector. “These files aim to inject the final stealer into legitimate processes, initiating malicious activities and sending the stolen data back to a C2…
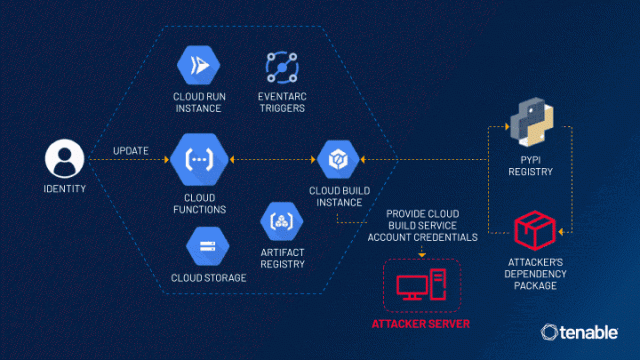
Read MoreOrganizations that have used Google Cloud Platform’s Cloud Functions – a serverless execution environment – could be impacted by a privilege escalation vulnerability discovered by Tenable and dubbed as “ConfusedFunction.” Read on to learn all about the vulnerability and what your organization needs to do to protect itself. Tenable Research has discovered a vulnerability in…
Read More“Based on the testing performed before the initial deployment of the Template Type (on March 05, 2024), trust in the checks performed in the Content Validator, and previous successful IPC Template Instance deployments, these instances were deployed into production,” CrowdStrike explained in its review. “When received by the sensor and loaded into the Content Interpreter,…
Read MoreRecent Posts
- Analysis: Intel’s AI Chip Efforts Stall As AMD Gets A Boost Against Nvidia
- CRN In Depth: Cisco 360 at Cisco Partner Summit 2024
- The 25 Hottest IoT And 5G Services Companies: 2024 Edge Computing 100
- Google Cloud to make MFA mandatory by the end of 2025
- LevelBlue: Driving Cyber Resilience in October (and Beyond)