The DORA doesn’t directly name escrow as a viable proportional component of stressed exit plans, but that doesn’t mean escrow isn’t the solution. “Remember, DORA is technology agnostic and cannot name a solution, but there’s a clear reason why the likes of the PRA, OCC, RBI, and MAS all name escrow: It works,” Scott says.…
Read MoreJul 24, 2024NewsroomVulnerability / Software Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two security flaws to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The vulnerabilities are listed below – CVE-2012-4792 (CVSS score: 9.3) – Microsoft Internet Explorer Use-After-Free Vulnerability CVE-2024-39891 (CVSS score: 5.3) – Twilio Authy…
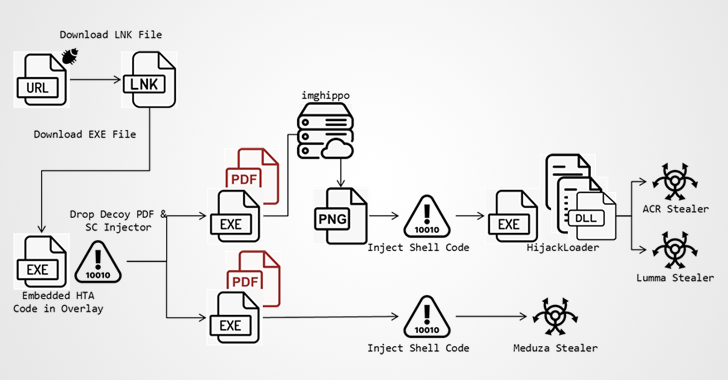
Read MoreJul 24, 2024NewsroomMalvertising / Threat Intelligence A now-patched security flaw in the Microsoft Defender SmartScreen has been exploited as part of a new campaign designed to deliver information stealers such as ACR Stealer, Lumma, and Meduza. Fortinet FortiGuard Labs said it detected the stealer campaign targeting Spain, Thailand, and the U.S. using booby-trapped files that…
Read MoreThe core discovery by the researchers is that connection tracking features don’t always isolate processes from each other, especially with those VPNs that run on top of Linux and make use of Netfilter implementations, a typical internal connection tracking routine. Without this isolation, connections could be shared across other machine resources. “This approach can pose…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-084 DATE(S) ISSUED: 07/23/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated…
Read More‘I think we are in this phase where we have to deeply work and make sure on these use cases and these work flows we are driving deeper progress in unlocking value, which I’m bullish will happen. But these things take time,’ says Alphabet CEO Sundar Pichai. Google parent company Alphabet is uniquely well-positioned for…
Read MoreThe Chinese hacking group tracked as ‘Evasive Panda’ was spotted using new versions of the Macma backdoor and the Nightdoor Windows malware. Symantec’s threat hunting team spotted the cyber espionage attacks targeting organizations in Taiwan and an American non-governmental organization in China. In the latter case, Evasive Panda (aka ‘Daggerfly’ or ‘Bronze Highland’) exploited a…
Read MoreThreat actors are taking advantage of the massive popularity of the Hamster Kombat game, targeting players with fake Android and Windows software that install spyware and information-stealing malware. Hamster Kombat is a clicker mobile game for Android where players earn fictional currency by completing simple tasks, primarily by tapping the screen. Launched in March 2024,…
Read MoreAs Jim Jackson, a 26-year HPE and HP veteran, prepares to retire August 1, his responsibilities will be combined with HPE’s chief communications officer under Jennifer Temple, who going forward will be HPE’s executive vice president and chief marketing and communications officer. Hewlett Packard Enterprise Tuesday said it will combine its chief marketing officer and…
Read MoreMicrosoft has released the July 2024 preview update for Windows 10, version 22H2, with fixes for Windows Defender Application Control (WDAC) issues causing app crashes and system memory exhaustion. KB5040525 is a monthly optional cumulative update that helps Windows administrators test fixes and improvements that will be included with the August 2024 Patch Tuesday release.…
Read MoreRecent Posts
- Analysis: Intel’s AI Chip Efforts Stall As AMD Gets A Boost Against Nvidia
- CRN In Depth: Cisco 360 at Cisco Partner Summit 2024
- The 25 Hottest IoT And 5G Services Companies: 2024 Edge Computing 100
- Google Cloud to make MFA mandatory by the end of 2025
- LevelBlue: Driving Cyber Resilience in October (and Beyond)