
‘Today marks the beginning of a new era for Windows,’ Microsoft CEO Satya Nadella wrote on LinkedIn. Microsoft’s Copilot+ PCs are now available for purchase on the tech giant’s website, bringing artificial intelligence processing to the machine as partners and their customers assess the value of new AI technologies. Billed by Microsoft as “the fastest,…
Read MoreWhile maintaining separate partner programs for the moment, Cisco is taking steps to build links between the Cisco and Splunk partner bases and help them leverage the combined Cisco-Splunk technology portfolio. Cisco Systems and its recently acquired Splunk business unit are taking the first steps to build links between their partners and the channel programs…
Read MoreThe Santa Clara, Calif.-based Flash storage-focused technology developer is focusing on three major sets of capabilities to the Pure storage platform, said one of the firm’s executives. Flash storage-focused technology developer Pure Storage Wednesday unveiled AI and security enhancements aimed at making it easier to manage and protect individual arrays and fleets of arrays. With…
Read MoreWhile AMD confirmed that it is investigating the alleged breach, IntelBroker has posted previews of stolen data that include employee database, customer database, source codes, and firmware data. Sensitive data offered in exchange for crypto In the post on Breach Forums, IntelBroker outlined the extent of the data breach, claiming to have accessed various types…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/labs-research/highly-evasive-squidloader-targets-chinese-organizations” on this server. Reference #18.c5d7ce17.1718798440.9a45b707 https://errors.edgesuite.net/18.c5d7ce17.1718798440.9a45b707 Source link lol
Read MoreJun 19, 2024The Hacker NewsGDPR Compliance / Data Privacy Are your tags really safe with Google Tag Manager? If you’ve been thinking that using GTM means that your tracking tags and pixels are safely managed, then it might be time to think again. In this article we look at how a big-ticket seller that does…
Read MoreThe Hacking of Culture and the Creation of Socio-Technical Debt Culture is increasingly mediated through algorithms. These algorithms have splintered the organization of culture, a result of states and tech companies vying for influence over mass audiences. One byproduct of this splintering is a shift from imperfect but broad cultural narratives to a proliferation of…
Read MoreJun 19, 2024NewsroomCybercrime / Cryptocurrency A threat actor who goes by alias markopolo has been identified as behind a large-scale cross-platform scam that targets digital currency users on social media with information stealer malware and carries out cryptocurrency theft. The attack chains involve the use of a purported virtual meeting software named Vortax (and 23…
Read MoreJun 19, 2024NewsroomMalware / Cyber Attack Chinese-speaking users are the target of a never-before-seen threat activity cluster codenamed Void Arachne that employs malicious Windows Installer (MSI) files for virtual private networks (VPNs) to deliver a command-and-control (C&C) framework called Winos 4.0. “The campaign also promotes compromised MSI files embedded with nudifiers and deepfake pornography-generating software,…
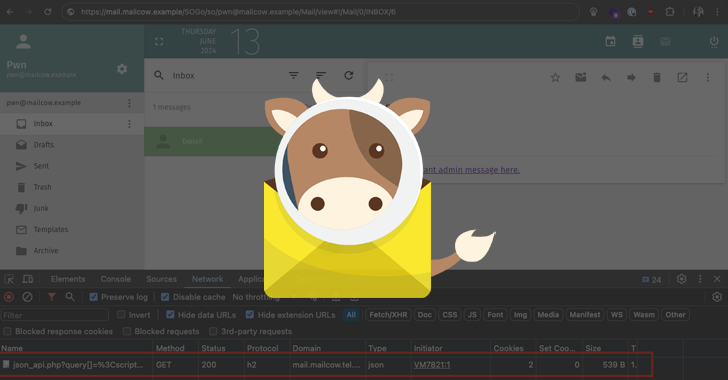
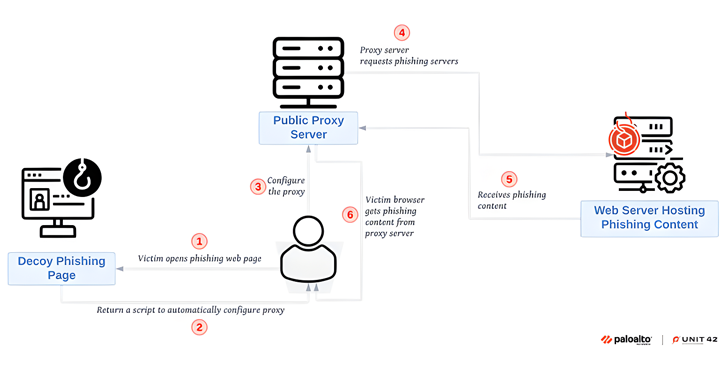
Read MoreJun 19, 2024NewsroomEmail Security / Vulnerability Two security vulnerabilities have been disclosed in the Mailcow open-source mail server suite that could be exploited by malicious actors to achieve arbitrary code execution on susceptible instances. Both shortcomings impact all versions of the software prior to version 2024-04, which was released on April 4, 2024. The issues…
Read MoreRecent Posts
- Free Sniper Dz Phishing Tools Fuel 140,000+ Cyber Attacks Targeting User Credentials
- New Cryptojacking Attack Targets Docker API to Create Malicious Swarm Botnet
- U.K. Hacker Charged in $3.75 Million Insider Trading Scheme Using Hacked Executive Emails
- The Playstation Network is down in a global outage
- The Playstation Network is suffering a global outage