Jul 25, 2024NewsroomCybercrime / Online Safety Meta Platforms on Wednesday said it took steps to remove around 63,000 Instagram accounts in Nigeria that were found to target people with financial sextortion scams. “These included a smaller coordinated network of around 2,500 accounts that we were able to link to a group of around 20 individuals,”…
Read MoreWhile the specifics for security testing vary for applications, web applications, and APIs, a holistic and proactive applications security strategy is essential for all three types. There are six core types of testing that every security professional should know about to secure their applications, regardless of what phase they are in in development or deployment.…
Read MoreData Wallets Using the Solid Protocol I am the Chief of Security Architecture at Inrupt, Inc., the company that is commercializing Tim Berners-Lee’s Solid open W3C standard for distributed data ownership. This week, we announced a digital wallet based on the Solid architecture. Details are here, but basically a digital wallet is a repository for…
Read MoreJul 25, 2024NewsroomDNS Security /Vulnerability The Internet Systems Consortium (ISC) has released patches to address multiple security vulnerabilities in the Berkeley Internet Name Domain (BIND) 9 Domain Name System (DNS) software suite that could be exploited to trigger a denial-of-service (DoS) condition. “A cyber threat actor could exploit one of these vulnerabilities to cause a…
Read More“I think [dismantling CISA] would be disastrous,” Michael Daniel, CEO of the Cyber Threat Alliance and former Special Assistant to President Obama and Cybersecurity Coordinator on the National Security Council Staff, tells CSO. “Reasonable people can disagree about how effective CISA has been, but we have labored for literally decades to create an effective cyber…
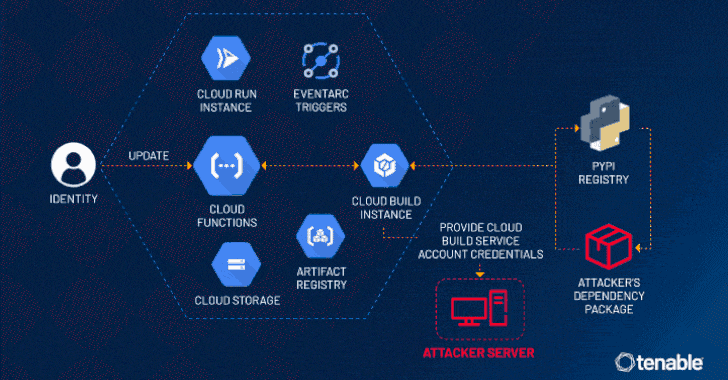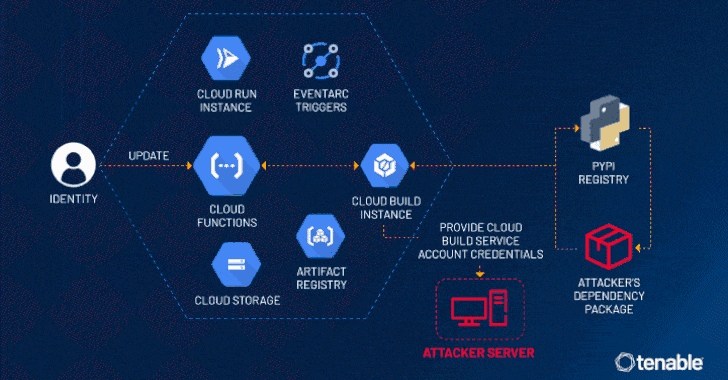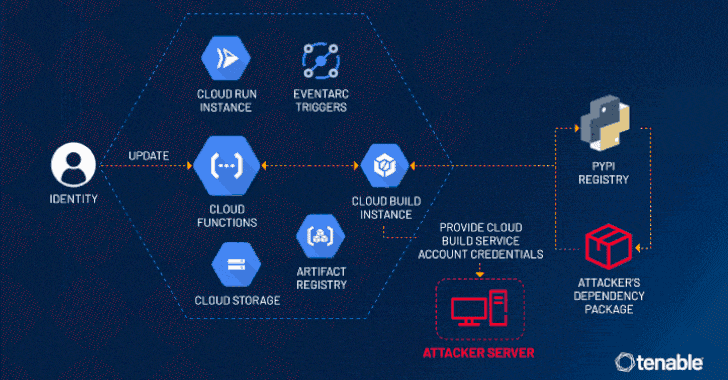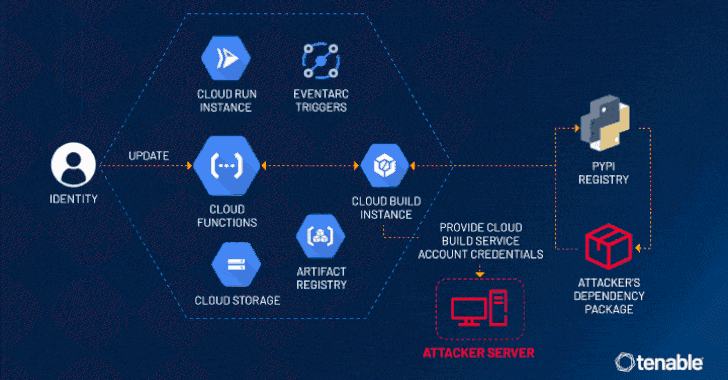
Read MoreJul 25, 2024NewsroomCloud Security / Vulnerability Cybersecurity researchers have disclosed a privilege escalation vulnerability impacting Google Cloud Platform’s Cloud Functions service that an attacker could exploit to access other services and sensitive data in an unauthorized manner. Tenable has given the vulnerability the name ConfusedFunction. “An attacker could escalate their privileges to the Default Cloud…
Read MoreWebinar: Securing the Modern Workspace: What Enterprises MUST Know about Enterprise Browser Security
by nlqip
Jul 25, 2024The Hacker NewsBrowser Security / Enterprise Security The browser is the nerve center of the modern workspace. Ironically, however, the browser is also one of the least protected threat surfaces of the modern enterprise. Traditional security tools provide little protection against browser-based threats, leaving organizations exposed. Modern cybersecurity requires a new approach based…
Read MoreA zero-day security flaw in Telegram’s mobile app for Android called EvilVideo made it possible for attackers to malicious files disguised as harmless-looking videos. The exploit appeared for sale for an unknown price in an underground forum on June 6, 2024, ESET said. Following responsible disclosure on June 26, the issue was addressed by Telegram…
Read MoreFinally, the response stage, which happens after the alert has been confirmed to be a true positive and an incident has been declared, involves the eviction of the threat actor. After determining the scope of the incident (how many systems, users, etc. are involved), security teams have many options to clear the attacker out, ranging…
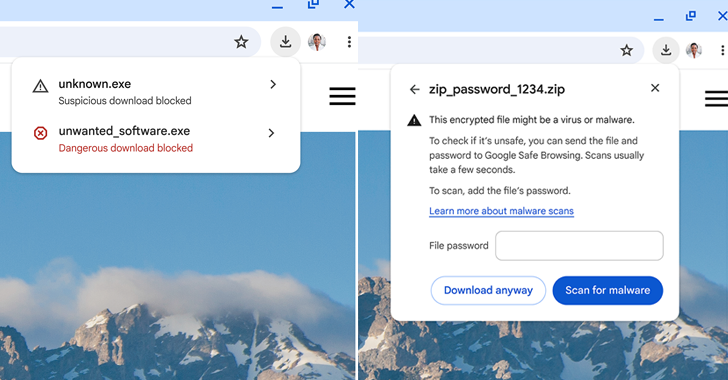
Read MoreJul 25, 2024NewsroomBrowser Security / Data Protection Google said it’s adding new security warnings when downloading potentially suspicious and malicious files via its Chrome web browser. “We have replaced our previous warning messages with more detailed ones that convey more nuance about the nature of the danger and can help users make more informed decisions,”…
Read MoreRecent Posts
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’
- Botnet exploits GeoVision zero-day to install Mirai malware
- FTC reports 50% drop in unwanted call complaints since 2021
- Bitfinex hacker gets 5 years in prison for 120,000 bitcoin heist