CrowdStrike released a Preliminary Post Incident Review (PIR) on the faulty Falcon update explaining that a bug allowed bad data to pass its Content Validator and cause millions of Windows systems to crash on July 19, 2024. The cybersecurity company explained that the issue was caused by a problematic content configuration update meant to gather…
Read MoreThe HashiCorp acquisition, GenAI and Red Hat taking on VMware are likely to come up. Updates on the HashiCorp acquisition. Details on IBM’s approach to the artificial intelligence gold rush. And IBM subsidiary Red Hat taking on VMware and legacy virtualization vendors. These are just some of the topics analysts will likely bring up Wednesday…
Read MoreA bug in CrowdStrike’s content approval system ‘passed validation despite containing problematic content data,’ leading to the outage that caused global disruptions. A bug in CrowdStrike’s validation process for security configuration updates resulted in the Microsoft Windows outage that led to global disruptions starting Friday, the company said Wednesday. The widely felt snafu involved what…
Read MoreOnce the HTA script, a Windows standalone program written in HTML is executed, it initiates PowerShell code that eventually establishes C2, downloads decoy PDF files for evasion, and a malicious shell injector. “These files aim to inject the final stealer into legitimate processes, initiating malicious activities and sending the stolen data back to a C2…
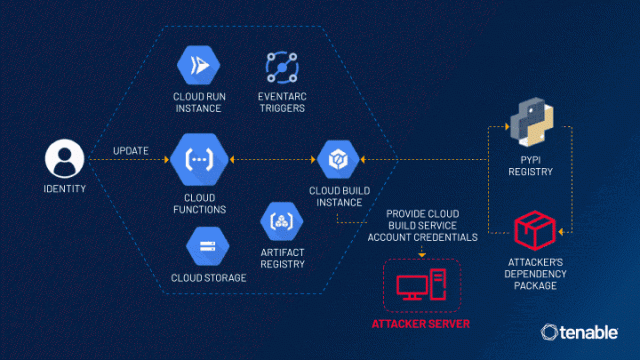
Read MoreOrganizations that have used Google Cloud Platform’s Cloud Functions – a serverless execution environment – could be impacted by a privilege escalation vulnerability discovered by Tenable and dubbed as “ConfusedFunction.” Read on to learn all about the vulnerability and what your organization needs to do to protect itself. Tenable Research has discovered a vulnerability in…
Read More“Based on the testing performed before the initial deployment of the Template Type (on March 05, 2024), trust in the checks performed in the Content Validator, and previous successful IPC Template Instance deployments, these instances were deployed into production,” CrowdStrike explained in its review. “When received by the sensor and loaded into the Content Interpreter,…
Read MoreSecurity questionnaires aren’t just an inconvenience — they’re a recurring problem for security and sales teams. They bleed time from organizations, filling the schedules of professionals with monotonous, automatable work. But what if there were a way to reduce or even altogether eliminate security questionnaires? The root problem isn’t a lack of great questionnaire products…
Read MoreVC investor Nadav Zafrir will replace Gil Shwed as Check Point CEO in December. Check Point Software Technologies said Wednesday that venture capitalist Nadav Zafrir will replace Gil Shwed as CEO of the cybersecurity vendor in December, in a major transition following Shwed’s three decades at the helm of the company. Shwed played a chief…
Read MoreLeidos serves prominent clients including the US Department of Defense (DOD), the Department of Homeland Security (DHS), NASA, and various other US and foreign agencies, as well as commercial businesses. The leak has raised significant concerns given the sensitive nature of the information involved. The report reviewed some of the leaked files posted on a…
Read MoreThe entire database for the notorious BreachForums v1 hacking forum was released on Telegram Tuesday night, exposing a treasure trove of data, including members’ information, private messages, cryptocurrency addresses, and every post on the forum. This data comes from a database backup allegedly sold by Conor Fitzpatrick, aka Pompompurin. In 2022, after the RaidForums hacking…
Read MoreRecent Posts
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’
- Botnet exploits GeoVision zero-day to install Mirai malware
- FTC reports 50% drop in unwanted call complaints since 2021
- Bitfinex hacker gets 5 years in prison for 120,000 bitcoin heist
- Here Are The Stellar Startup Edge Computing/IoT Vendors To Know In 2024