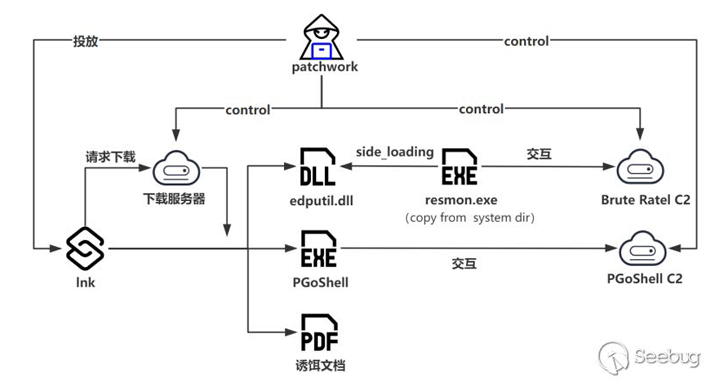
Jul 24, 2024NewsroomCyber Espionage / Threat Intelligence The threat actor known as Patchwork has been linked to a cyber attack targeting entities with ties to Bhutan to deliver the Brute Ratel C4 framework and an updated version of a backdoor called PGoShell. The development marks the first time the adversary has been observed using the…
Read MoreJul 24, 2024The Hacker NewsSaaS Management / IT Governance There is one simple driver behind the modern explosion in SaaS adoption: productivity. We have reached an era where purpose-built tools exist for almost every aspect of modern business and it’s incredibly easy (and tempting) for your workforce to adopt these tools without going through the…
Read MoreMost companies, however, didn’t extend this to its natural next step. Why do we trust our administrative users and software implicitly? Endpoints — whether laptops held by users, servers in the cloud, or embedded devices powering airport displays — are often heavily laden with remote administrator tools in the unified endpoint management (UEM) space. Asset…
Read MoreBlackFog marks the next chapter of growth with Brenda Robb as President, John Sarantakes as CRO, and Mark Griffith as VP of Strategic Sales San Francisco, CA—July 24, 2024– BlackFog, the leader in ransomware protection and anti data exfiltration (ADX), today announced it has made new appointments to strengthen its leadership team as it witnesses…
Read MoreJul 24, 2024NewsroomSoftware Update / IT Outage Cybersecurity firm CrowdStrike on Wednesday blamed an issue in its validation system for causing millions of Windows devices to crash as part of a widespread outage late last week. “On Friday, July 19, 2024 at 04:09 UTC, as part of regular operations, CrowdStrike released a content configuration update…
Read MoreThe DORA doesn’t directly name escrow as a viable proportional component of stressed exit plans, but that doesn’t mean escrow isn’t the solution. “Remember, DORA is technology agnostic and cannot name a solution, but there’s a clear reason why the likes of the PRA, OCC, RBI, and MAS all name escrow: It works,” Scott says.…
Read MoreJul 24, 2024NewsroomVulnerability / Software Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two security flaws to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The vulnerabilities are listed below – CVE-2012-4792 (CVSS score: 9.3) – Microsoft Internet Explorer Use-After-Free Vulnerability CVE-2024-39891 (CVSS score: 5.3) – Twilio Authy…
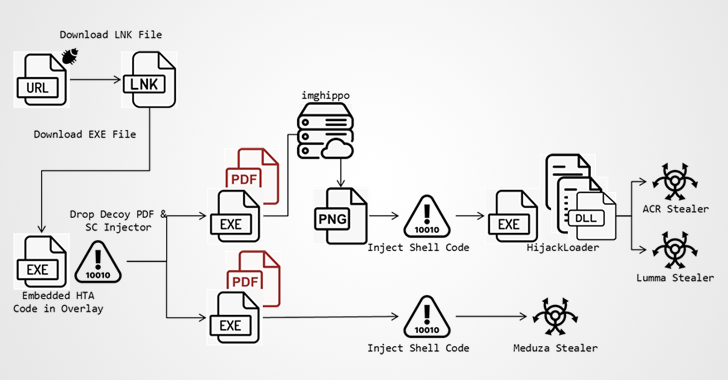
Read MoreJul 24, 2024NewsroomMalvertising / Threat Intelligence A now-patched security flaw in the Microsoft Defender SmartScreen has been exploited as part of a new campaign designed to deliver information stealers such as ACR Stealer, Lumma, and Meduza. Fortinet FortiGuard Labs said it detected the stealer campaign targeting Spain, Thailand, and the U.S. using booby-trapped files that…
Read MoreThe core discovery by the researchers is that connection tracking features don’t always isolate processes from each other, especially with those VPNs that run on top of Linux and make use of Netfilter implementations, a typical internal connection tracking routine. Without this isolation, connections could be shared across other machine resources. “This approach can pose…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-084 DATE(S) ISSUED: 07/23/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Google Chrome, the most severe of which could allow for arbitrary code execution. Successful exploitation of the most severe of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated…
Read More