The Spanish authorities have arrested three individuals for using DDoSia, a distributed denial of service platform operated by pro-Russian hacktivists, to conduct DDoS attacks against governments and organizations in NATO countries. The arrests were made in the suspects’ homes in Seville, Huelva, and Manacor. The police also confiscated various computer equipment and documents of interest…
Read MoreOur new research paper gives you a roadmap for using Pimcore’s features while preserving security. Enterprises are using Pimcore, an open-source enterprise PHP solution, to streamline data management and experience management across devices. Our new research paper “Auditing Pimcore Enterprise Platform” examines the most common issues with Pimcore and details methods that can be used…
Read MoreAcademySoftwareFoundation–OpenImageIO OpenImageIO is a toolset for reading, writing, and manipulating image files of any image file format relevant to VFX / animation via a format-agnostic API with a feature set, scalability, and robustness needed for feature film production. In affected versions there is a bug in the heif input functionality of OpenImageIO. Specifically, in `HeifInput::seek_subimage()`.…
Read MoreMSPs & MSSPs: How to Increase Engagement with Your Cybersecurity Clients Through vCISO Reporting
by nlqip
As a vCISO, you are responsible for your client’s cybersecurity strategy and risk governance. This incorporates multiple disciplines, from research to execution to reporting. Recently, we published a comprehensive playbook for vCISOs, “Your First 100 Days as a vCISO – 5 Steps to Success”, which covers all the phases entailed in launching a successful vCISO…
Read MoreThe opportunities to use AI in workflow automation are many and varied, but one of the simplest ways to use AI to save time and enhance your organization’s security posture is by building an automated SMS analysis service. Workflow automation platform Tines provides a good example of how to do it. The vendor recently released…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/4-low-priority-online-threats-that-can-inflict-serious-brand-damage” on this server. Reference #18.c4d7ce17.1721651812.86d199fc https://errors.edgesuite.net/18.c4d7ce17.1721651812.86d199fc Source link lol
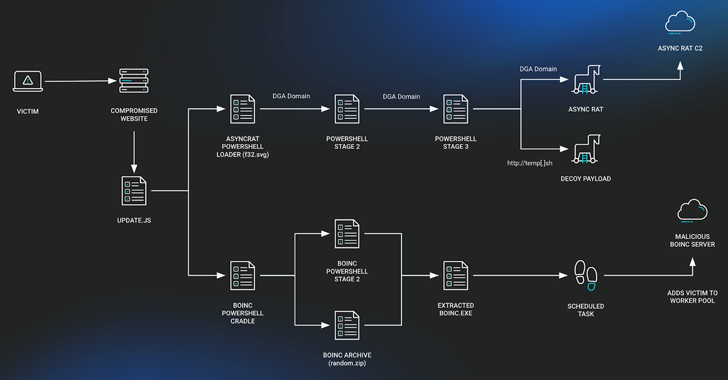
Read MoreJul 22, 2024NewsroomVulnerability / Malware The JavaScript downloader malware known as SocGholish (aka FakeUpdates) is being used to deliver a remote access trojan called AsyncRAT as well as a legitimate open-source project called BOINC. BOINC, short for Berkeley Open Infrastructure Network Computing Client, is an open-source “volunteer computing” platform maintained by the University of California…
Read MoreEmployers should also clearly define the process for the intern and explain what is required of them. If possible, Smith recommends mentoring an intern, not simply ticking off a bureaucratic checklist of their tasks: “I do fervently believe you essentially need a sponsor, someone who’s going to take the intern under his or her wing…
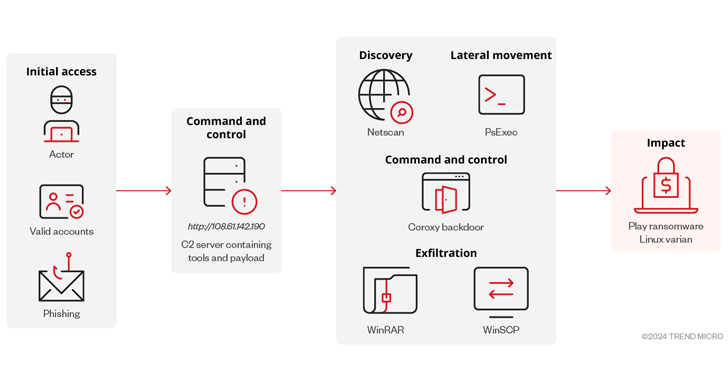
Read MoreCybersecurity researchers have discovered a new Linux variant of a ransomware strain known as Play (aka Balloonfly and PlayCrypt) that’s designed to target VMware ESXi environments. “This development suggests that the group could be broadening its attacks across the Linux platform, leading to an expanded victim pool and more successful ransom negotiations,” Trend Micro researchers…
Read MoreThreat actors are exploiting the massive business disruption from CrowdStrike’s glitchy update on Friday to target companies with data wipers and remote access tools. As businesses are looking for assistance to fix affected Windows hosts, researchers and government agencies have spotted an increase in phishing emails trying to take advantage of the situation. Official channel…
Read MoreRecent Posts
- Safeguarding Healthcare Organizations from IoMT Risks
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks