Brett Solomon on Digital Rights Brett Solomon is retiring from AccessNow after fifteen years as its Executive Director. He’s written a blog post about what he’s learned and what comes next. Tags: history of security, human rights Posted on July 19, 2024 at 12:02 PM • 0 Comments Sidebar photo of Bruce Schneier by Joe…
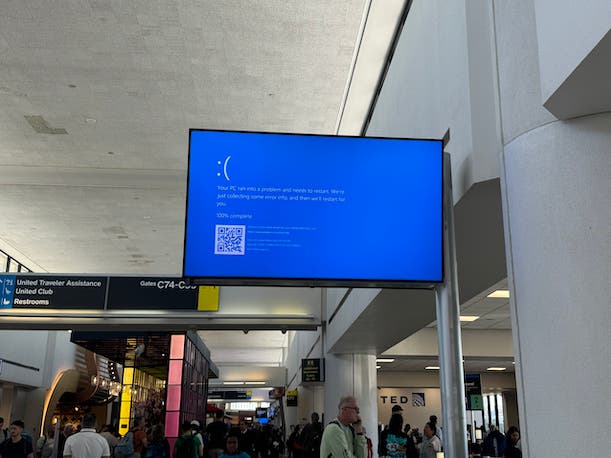
Read MoreIn terms of recovering from the outage, ‘it could be some time for some systems that just won’t automatically recover,’ Kurtz said in a televised interview. After a CrowdStrike software update caused a massive Microsoft outage with impacts worldwide, “it could be some time” before a full recovery is possible, CrowdStrike CEO George Kurtz said…
Read More‘We’re helping by offering community support, helping with recovery plans, offering up our staff to augment the MSSPs and helping wherever we can,’ says Marc Menzies, president and CTO of Overview Technology Solutions. ‘We’re saying, “Hey, I know that everyone’s morning is messed up, ours is now messed up too but we’re here to help…
Read MoreTry Tenable Web App Scanning Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.…
Read MoreUS software development company Solarwinds has sent out important security fixes that close a number of critical vulnerabilities in its Access Rights Manager software. Six of the vulnerabilities scored 9.6 out of 10 on the Common Vulnerability Scoring Scale (CVSS), which means hackers can attack unprotected systems without having to gain administrator rights to gain…
Read MoreAfter a defective CrowdStrike software update caused massive impacts to flights, medical services and 911 systems, CrowdStrike will likely take a hit to its strong brand in the cybersecurity market, according to Wedbush Securities’ Daniel Ives. After CrowdStrike’s Falcon software update caused a Microsoft outage and led to massive impacts to flights, medical services and…
Read MoreCrowdStrike says that it has deployed a fix after a defective software update led to widespread outages and massive real-world impacts to flights, health-care services and 911 systems. Microsoft tech outages reported Friday led to widespread disruptions worldwide in an incident stemming from a defective software update from cybersecurity giant CrowdStrike. The update led to…
Read MoreA faulty software update from cybersecurity vendor Crowdstrike crippled countless Microsoft Windows computers across the globe today, disrupting everything from airline travel and financial institutions to hospitals and businesses online. Crowdstrike said a fix has been deployed, but experts say the recovery from this outage could take some time, as Crowdstrike’s solution needs to be…
Read MoreCrowdStrike Falcon Issue ‘Fix Has Been Deployed;’ Microsoft Identifies ‘Root Cause’ Of Outage
by nlqip
The massive Microsoft Azure and CrowdStrike outage reportedly was caused by a recent update to CrowdStrike Falcon Sensor software. Here’s where everything stands as of Friday morning. From emergency 911 call centers to national health-care services to the largest airlines, the Microsoft Azure and CrowdStrike outage is causing chaos around the world. As of Friday…
Read MoreJul 19, 2024NewsroomRansomware / Cybercrime Two Russian nationals have pleaded guilty in a U.S. court for their participation as affiliates in the LockBit ransomware scheme and helping facilitate ransomware attacks across the world. The defendants include Ruslan Magomedovich Astamirov, 21, of Chechen Republic, and Mikhail Vasiliev, 34, a dual Canadian and Russian national of Bradford,…
Read MoreRecent Posts
- Safeguarding Healthcare Organizations from IoMT Risks
- Broadcom’s VMware Issues ‘Top of Mind’ For Partners, Nutanix Channel Chief Says
- Microsoft just killed the Windows 10 Beta Channel again
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks