Jul 17, 2024The Hacker NewsInsider Threats / Cybersecurity Attacks on your network are often meticulously planned operations launched by sophisticated threats. Sometimes your technical fortifications provide a formidable challenge, and the attack requires assistance from the inside to succeed. For example, in 2022, the FBI issued a warning1 that SIM swap attacks are growing: gain…
Read More“Internet Explorer (IE) has officially ended support on June 15, 2022,” the researchers explain. “Additionally, IE has been officially disabled through later versions of Windows 10, including all versions of Windows 11. Disabled, however, does not mean IE was removed from the system. The remnants of IE exist on the modern Windows system, though it…
Read MoreAccess Denied You don’t have permission to access “http://cybersecurity.att.com/blogs/security-essentials/proactive-cyber-defense-the-essential-role-of-internal-penetration-testing-in-the-age-of-ai” on this server. Reference #18.dbd7ce17.1721210865.10e331b9 https://errors.edgesuite.net/18.dbd7ce17.1721210865.10e331b9 Source link lol
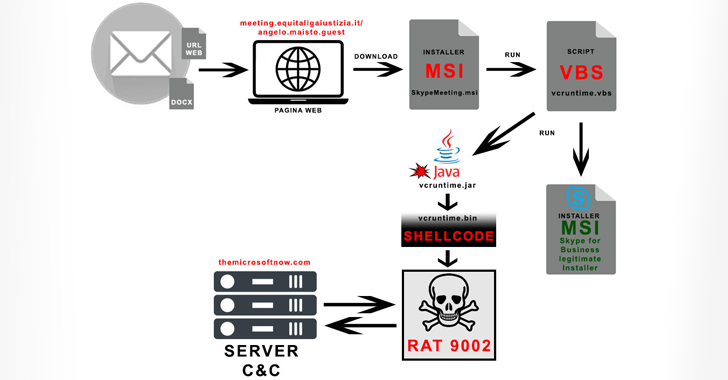
Read MoreJul 17, 2024NewsroomCyber Espionage / Threat Intelligence A China-linked threat actor called APT17 has been observed targeting Italian companies and government entities using a variant of a known malware referred to as 9002 RAT. The two targeted attacks took place on June 24 and July 2, 2024, Italian cybersecurity company TG Soft said in an…
Read MoreJul 17, 2024NewsroomCybercrime / Ransomware The infamous cybercrime group known as Scattered Spider has incorporated ransomware strains such as RansomHub and Qilin into its arsenal, Microsoft has revealed. Scattered Spider is the designation given to a threat actor that’s known for its sophisticated social engineering schemes to breach targets and establish persistence for follow-on exploitation…
Read MoreWrong! In theory, API connectivity sounds good, but it is extremely limited in practice. For it to work well, vendors have to open their APIs to other vendors. Sometimes they do, opening some APIs and not others, sometimes they refuse to do so. Even if they open their APIs, there are still problems. Suppose a…
Read MoreJul 17, 2024NewsroomVulnerability / Data Security Threat actors are actively exploiting a recently disclosed critical security flaw impacting Apache HugeGraph-Server that could lead to remote code execution attacks. Tracked as CVE-2024-27348 (CVSS score: 9.8), the vulnerability impacts all versions of the software before 1.3.0. It has been described as a remote command execution flaw in…
Read MoreKaspersky is offering free security products for six months and tips for staying safe as a parting gift to consumers in the United States. The company decided to close its business and lay off employees in the U.S. after the U.S. government added Kaspersky to the Entity List, a catalog of “foreign individuals, companies, and…
Read MoreCISA is warning that a critical GeoServer GeoTools remote code execution flaw tracked as CVE-2024-36401 is being actively exploited in attacks. GeoServer is an open-source server that allows users to share, process, and modify geospatial data. On June 30th, GeoServer disclosed a critical 9.8 severity remote code execution vulnerability in its GeoTools plugin caused by…
Read MoreOracle addresses 175 CVEs in its third quarterly update of 2024 with 386 patches, including 26 critical updates. Background On July 16, Oracle released its Critical Patch Update (CPU) for July 2024, the third quarterly update of the year. This CPU contains fixes for 175 CVEs in 386 security updates across 29 Oracle product families.…
Read MoreRecent Posts
- Fraud network uses 4,700 fake shopping sites to steal credit cards
- CISA warns of more Palo Alto Networks bugs exploited in attacks
- New Glove infostealer malware bypasses Chrome’s cookie encryption
- New Glove Stealer malware bypasses Chrome’s cookie encryption
- Stellar Startup Data Center Tech Vendors To Know In 2024