‘We received an investment this year. The idea was to make sure we could expand towards the US and become a global company. We had two main objectives. One was to get into the U.S. market as a global company and establish ourselves here. … And we realized that we needed to establish ourselves as…
Read MoreAn Equinix spokesperson tells CRN in a statement that the company is ‘fully committed’ to its facilities in Hong Kong. ‘As a platform company, all assets are important to the success of the platform and Equinix Hong Kong serves as a key interconnection hub for our global customer base,’ the spokesperson says. Data center provider…
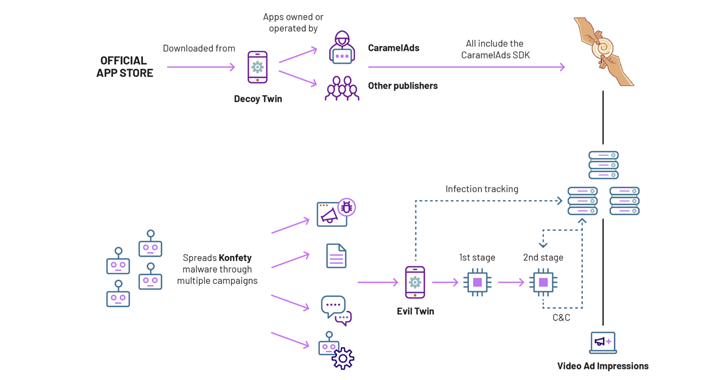
Read MoreJul 16, 2024NewsroomMobile Security / Online Security ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt…
Read MoreImage: MidjourneyMicrosoft says the Scattered Spider cybercrime gang has added Qilin ransomware to its arsenal and is now using it in attacks. “In the second quarter of 2024, financially motivated threat actor Octo Tempest, our most closely tracked ransomware threat actor, added RansomHub and Qilin to its ransomware payloads in campaigns,” Microsoft said Monday. After surfacing…
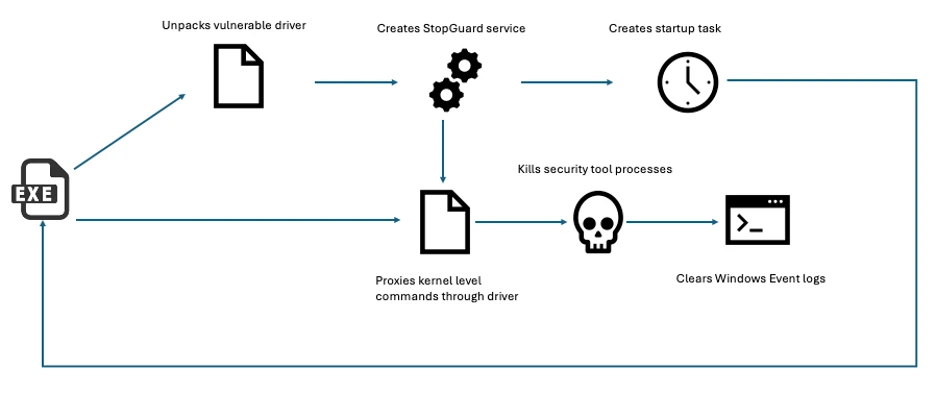
Read MoreTechnical Analysis: Killer Ultra Malware Targeting EDR Products in Ransomware Attacks | Binary Defense
by nlqip
This post was written by John Dwyer, Director of Security Research at Binary Defense, and made possible through the contributions of TrustedSec Senior Research Analyst Kevin Haubris and Eric Gonzalez of Binary Defense. ARC Labs recently recovered a tool leveraged in Qilin ransomware attacks aimed at impairing defenses by disabling popular endpoint detection and response…
Read MoreMicrosoft has finally fixed a known Outlook issue, confirmed in February, which was triggering incorrect security alerts after installing the December security updates for Outlook Desktop. The company acknowledged the bug in early February after many Microsoft 365 users reported seeing unexpected warnings that “This location may be unsafe” and “Microsoft Office has identified a…
Read MoreAs a CIO, I often wish for a world where the threat landscape is less expansive and complicated than it is today. Unfortunately, the reality is quite different. This month, I find myself particularly focused on the idea that our digital business would come to a grinding halt without the technology ecosystem that supports it.…
Read MoreHarrell tells CRN that managed security services and advisory services—leveraging Dataminr’s AI platform—represent massive opportunities for partners. AI platform provider Dataminr announced Tuesday it has hired former Cloudflare channel chief Matt Harrell as its new chief partner officer, with the company looking to intensify its push with partners around security services. Speaking with CRN, Harrell…
Read MoreIdentity-based threats on SaaS applications are a growing concern among security professionals, although few have the capabilities to detect and respond to them. According to the US Cybersecurity and Infrastructure Security Agency (CISA), 90% of all cyberattacks begin with phishing, an identity-based threat. Throw in attacks that use stolen credentials, over-provisioned accounts, and insider threats,…
Read MoreSpeculations on the method Cybersecurity experts pointed out that in recent incidents, hackers have breached Slack accounts by exploiting stolen or leaked API keys. “Developers often integrate Slack into their automation tools, and in the process, sometimes accidentally leak these keys on code-sharing sites like GitHub or API platforms like Postman,” said Rahul Sasi, CEO…
Read More