Jul 16, 2024NewsroomVulnerability / Infrastructure Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a critical security flaw impacting OSGeo GeoServer GeoTools to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. GeoServer is an open-source software server written in Java that allows users to share and edit geospatial…
Read MoreJul 16, 2024NewsroomNational Security / Data Security Russian security vendor Kaspersky has said it’s exiting the U.S. market nearly a month after the Commerce Department announced a ban on the sale of its software in the country citing a national security risk. News of the closure was first reported by journalist Kim Zetter. The company…
Read MoreShifting from Compliance to Cyber Readiness: A Critical Evolution for the Department of the Navy – CnSight.io – Cybersecurity Performance Improvement
by nlqip
The new Department of the Navy Cyber Strategy, published in November, mandates a comprehensive reevaluation of the Navy’s approach to technology and cybersecurity. This inaugural version of the cyber strategy draws on the National Defense Strategy (NDS) and the Department of Defense Cyber Strategy as key precedents, setting the stage for a more resilient and…
Read MoreGenerative AI in cybersecurity presents both significant benefits and serious risks. Popular AI tools like ChatGPT and DALL-E2 enhance data analytics, customer service, and threat detection, simplifying complex tasks and addressing talent shortages. However, they also empower hackers to automate attacks, create advanced malware, and evade traditional defenses. Experts stress the need for robust data…
Read MoreRussian cybersecurity company and antivirus software provider Kaspersky Lab will start shutting down operations in the United States on July 20. In a statement to BleepingComputer, the company also confirmed that it will lay off its U.S.-based employees. Independent cybersecurity journalist Kim Zetter first reported that this will affect “less than 50 employees in the…
Read More‘The more willingness to have conversations and to do research, [that will] help sellers down the line as they think about the right fit for them,’ says Sydney Hockett, vice president of Evergreen Services Group. When it comes to selling an MSP business, owners have a lot of options. Merging or selling to a holding…
Read MoreThe Iranian-backed MuddyWatter hacking group has partially switched to using a new custom-tailored malware implant to steal files and run commands on compromised systems. Dubbed BugSleep, this new backdoor is still actively being developed and was discovered by analysts at Check Point Research while being distributed via well-crafted phishing lures. The campaign pushes the malware…
Read MoreHacking Scientific Citations Some scholars are inflating their reference counts by sneaking them into metadata: Citations of scientific work abide by a standardized referencing system: Each reference explicitly mentions at least the title, authors’ names, publication year, journal or conference name, and page numbers of the cited publication. These details are stored as metadata, not…
Read MoreAdobe–Bridge Bridge versions 14.0.4, 13.0.7, 14.1 and earlier are affected by an Integer Overflow or Wraparound vulnerability that could result in arbitrary code execution in the context of the current user. Exploitation of this issue requires user interaction in that a victim must open a malicious file. 2024-07-09 7.8 CVE-2024-34139psirt@adobe.com Adobe–InDesign Desktop InDesign Desktop versions…
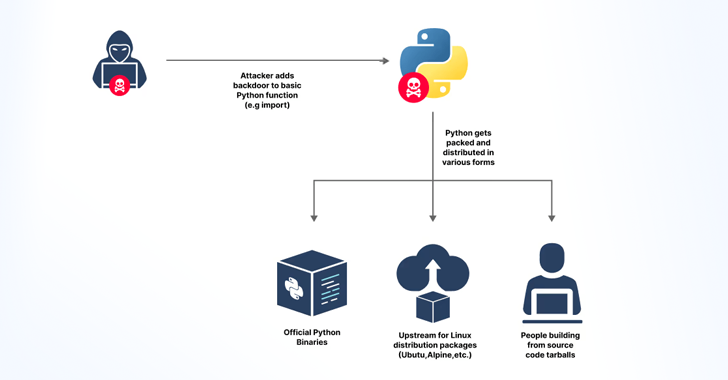
Read MoreJul 15, 2024NewsroomSupply Chain Attack / Cyber Threat Cybersecurity researchers said they discovered an accidentally leaked GitHub token that could have granted elevated access to the GitHub repositories of the Python language, Python Package Index (PyPI), and the Python Software Foundation (PSF) repositories. JFrog, which found the GitHub Personal Access Token, said the secret was…
Read MoreRecent Posts
- LevelBlue Cybersecurity Awareness Month Recap
- Red Hat Updates Present ‘Huge’ Partner Opportunities in OpenShift, Edge
- US govt officials’ communications compromised in recent telecom hack
- Microsoft patches Windows zero-day exploited in attacks on Ukraine
- Leaked info of 122 million linked to B2B data aggregator breach