Microsoft has provided a temporary workaround for a known issue preventing the Microsoft Photos app from launching on some Windows 11 systems. The company says this bug impacts devices running Windows 11 22H2 and 23H2, on which the “Prevent non-admin users from installing packaged Windows apps” or the BlockNonAdminUserInstall Configuration Service provider (CSP) policies are…
Read MoreCISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog…
Read MoreThe SEXi ransomware operation, known for targeting VMware ESXi servers, has rebranded under the name APT INC and has targeted numerous organizations in recent attacks. The threat actors started attacking organizations in February 2024 using the leaked Babuk encryptor to target VMware ESXi servers and the leaked LockBit 3 encryptor to target Windows. The cybercriminals…
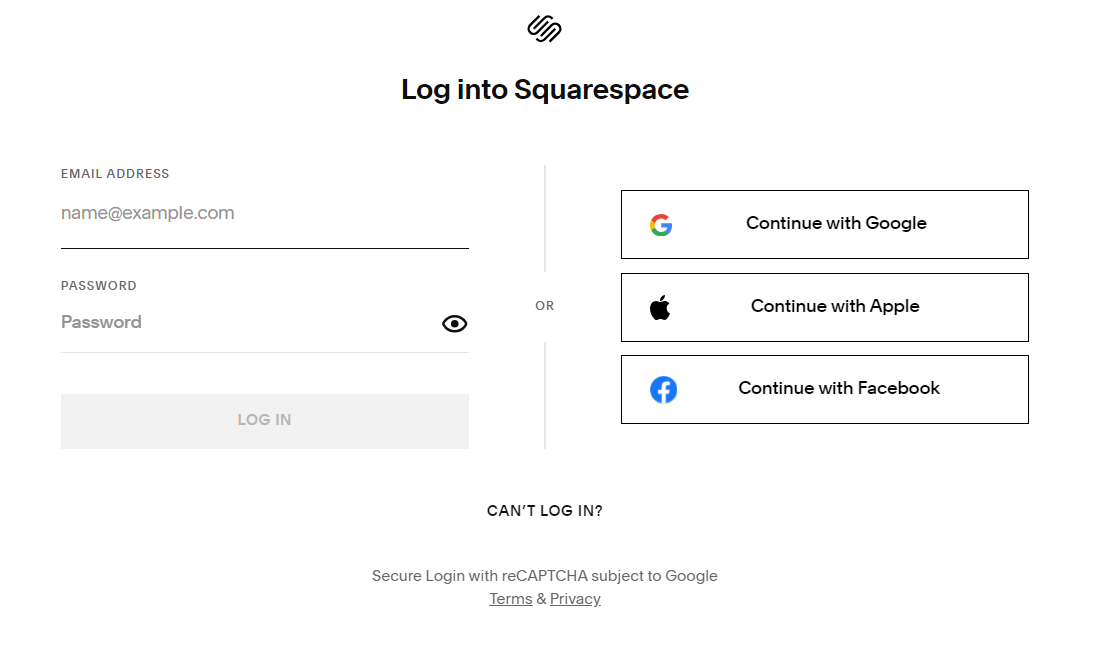
Read MoreAt least a dozen organizations with domain names at domain registrar Squarespace saw their websites hijacked last week. Squarespace bought all assets of Google Domains a year ago, but many customers still haven’t set up their new accounts. Experts say malicious hackers learned they could commandeer any migrated Squarespace accounts that hadn’t yet been registered,…
Read MoreCyber attackers constantly improve their tactics to evade detection and achieve malicious objectives, making it important for organizations to develop better detection and response strategies. The Living Off The Land (LOTL) technique is an example of a stealthy attack vector cyber attackers use to avoid detection. It is an infiltration technique that allows adversaries to…
Read MoreCybercriminals use Facebook business pages and advertisements to promote fake Windows themes that infect unsuspecting users with the SYS01 password-stealing malware. Trustwave researchers who observed the campaigns said the threat actors also promote fake downloads for pirated games and software, Sora AI, 3D image creator, and One Click Active. While using Facebook advertisements to push information-stealing…
Read MoreMicrosoft has confirmed that Windows Server updates from last month’s Patch Tuesday break some Microsoft 365 Defender features that use the network data reporting service. Redmond describes Microsoft 365 Defender (now known as Defender XDR) as a pre-and post-breach enterprise defense suite that helps coordinate detection, prevention, investigation, and response across an organization’s endpoints, identities, email, and…
Read MoreAs part of the annual Tech Innovator Awards evaluation process CRN selects a number of the applicants as finalists. Here’s a look at the innovative products that have made the first round of the judging. Innovation Surge The wave of development around artificial intelligence and generative AI in the last two years has shaken up…
Read MoreNew Zscaler Channel Chief Anthony Torsiello On Plans For ‘Substantial Investments’ With Partners
by nlqip
A ServiceNow veteran who joins Zscaler as of Monday, Torsiello tells CRN that the cybersecurity vendor’s growth strategy ‘starts with having a highly capable ecosystem of partners.’ Anthony Torsiello, a former longtime channel business leader at ServiceNow, has been hired by Zscaler as its new global channel chief, he said in an interview with CRN.…
Read MoreFrom the shocking exit of CEO Adam Selipsky to pouring tens of billions of dollars into cloud infrastructure to fuel its AI future, news stories coming out of the world’s largest cloud computing company have been non-stop in 2024. Amazon Web Services also hit some significant milestones in 2024 that grabbed the IT world’s attention,…
Read MoreRecent Posts
- Red Hat Updates Present ‘Huge’ Partner Opportunities in OpenShift, Edge
- US govt officials’ communications compromised in recent telecom hack
- Microsoft patches Windows zero-day exploited in attacks on Ukraine
- Leaked info of 122 million linked to B2B data aggregator breach
- Dell NativeEdge Platform Brings AI To Edge Operations