‘This workforce reduction is aimed at further driving operational efficiency and customer centricity,’ according to a UiPath regulatory filing. About a month after changing CEOs, business automation platform provider UiPath revealed plans to cut 10 percent of its employee base – about 4,200 employees. The New York-based vendor said in a regulatory filing that most…
Read MoreThe number of persons affected by a recent data breach at Evolve Bank & Trust exceeds 7.64 million, a document submitted to the Office of the Maine Attorney General this week by the law firm representing the financial services organization reveals. According to the document, the breach occurred on February 9, but was not discovered…
Read MoreCISA and the FBI urged software companies on Wednesday to review their products and eliminate path OS command injection vulnerabilities before shipping. The advisory was released in response to recent attacks that exploited multiple OS command injection security flaws (CVE-2024-20399, CVE-2024-3400, and CVE-2024-21887) to compromise Cisco, Palo Alto, and Ivanti network edge devices. Velvet Ant,…
Read MoreCISA and FBI Release Secure by Design Alert on Eliminating OS Command Injection Vulnerabilities | CISA
by nlqip
Today, CISA and FBI are releasing their newest Secure by Design Alert in the series, Eliminating OS Command Injection Vulnerabilities, in response to recent well-publicized threat actor campaigns that exploited OS command injection defects in network edge devices (CVE-2024-20399, CVE-2024-3400, CVE-2024-21887) to target and compromise users. These vulnerabilities allowed unauthenticated malicious actors to remotely execute code on network…
Read MoreA large-scale fraud campaign with over 700 domain names is likely targeting Russian-speaking users looking to purchase tickets for the Summer Olympics in Paris. The operation offers fake tickets to the Olympic Games and appears to take advantage of other major sports and music events. Researchers analyzing the campaign are calling it Ticket Heist and…
Read MoreWWT CEO On ‘Unhappy’ Broadcom VMware Customers Seeking Alternatives And WWT ‘Tripling’ AI Initiatives
by nlqip
‘[Broadcom’s] been an incredibly successful company. They have a strategy and approach that they take. But I can tell you, it’s not sitting well with the majority of the customers—a very large majority. Customers are looking for alternatives,’ says WWT CEO Jim Kavanaugh. Jim Kavanaugh, CEO of the $20 billion tech powerhouse World Wide Technology,…
Read MoreJapan’s Computer Emergency Response Team Coordination Center (JPCERT/CC) is warning that Japanese organizations are being targeted in attacks by the North Korean ‘Kimsuky’ threat actors. The US government has attributed Kimsuky as a North Korean advanced persistent threat (APT) group that conducts attacks against targets worldwide to gather intelligence on topics of interest to the…
Read MoreAs part of its efforts to challenge Nvidia, the chip designer says its $665 million acquisition of European AI lab and open-source large language model developer Silo AI will help enterprises develop and deploy AI solutions faster and more effectively. AMD has reached a deal to acquire Silo AI, which it called the largest private…
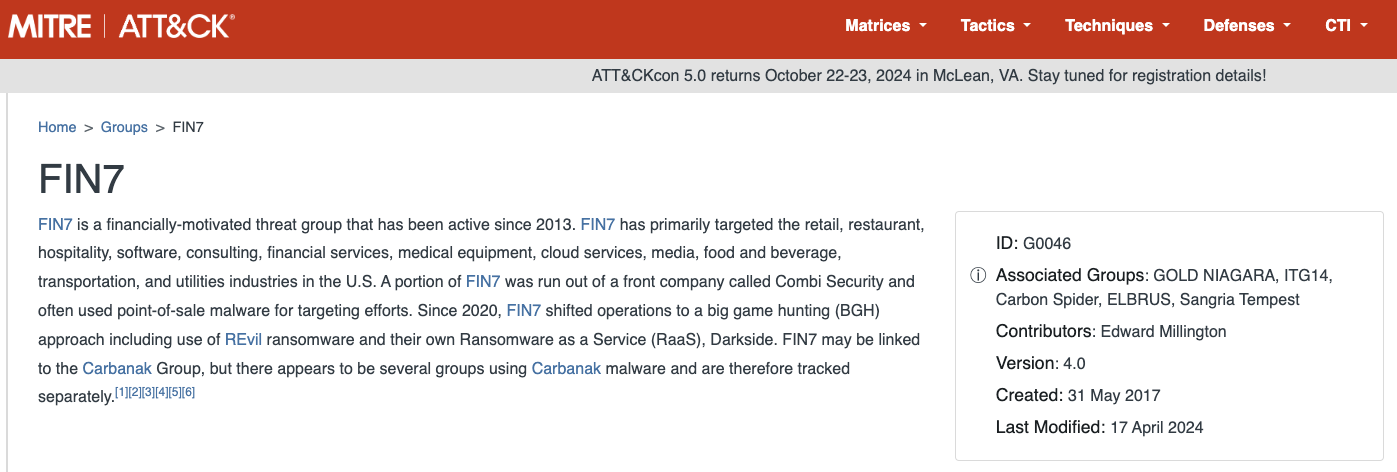
Read MoreThe Russia-based cybercrime group dubbed “Fin7,” known for phishing and malware attacks that have cost victim organizations an estimated $3 billion in losses since 2013, was declared dead last year by U.S. authorities. But experts say Fin7 has roared back to life in 2024 — setting up thousands of websites mimicking a range of media…
Read MoreMicrosoft fixed a Windows zero-day vulnerability that has been actively exploited in attacks for eighteen months to launch malicious scripts while bypassing built-in security features. The flaw, tracked as CVE-2024-38112, is a high-severity MHTML spoofing issue fixed during the July 2024 Patch Tuesday security updates. Haifei Li of Check Point Research discovered the vulnerability and disclosed…
Read More